- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R82 - ElasticXL
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R82 - ElasticXL
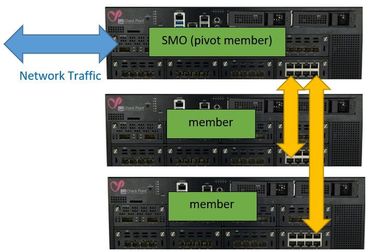
ElasticXL is a new cluster technology that enables simplified operation with a single management object with automatic configuration and software synchronisation between all cluster members.
ElasticXL is expected to be delivered with R82 or later versions. ElasticXL is based on similar technology to Maestro, but without MHOs. It is based on Check Point's SP versions for a scalable platform that allows you to increase the performance of the security gateways almost linearly.
This is achieved naturally by load balancing between individual gateways that operate in a cluster as a single entity.
This new cluster technology will some of the Maestro featchers such as SMO (Singel Management Object) use.
A ElasticX gateway will work as a pivot member and act simelar as a MHO's in a Maestro environment and simultaneously takes on the role of SMO.
The pivot member takes over the network connection and controls the ARP requests in the network. The pivot member distributes the connections via a distribution matrix to the connected member in the security group similar to a Maestro environment.
Same as the Maestro environments, the familiar SP commands will also be available here and there will also be a gclish. The management traffic will be handled by the SMO (pivot member).
Installation process:
1) The gateways are installed as usual via the First Configuration Wizard. ElasticXL" is now selected instead of "ClusterXL" on the product page.
2) After that, the SIC to the first gateway (pivot member) will be established single gateway (not as a cluster object). Afterwards, the policy can be installed.
3) In the following step the next gateways can be added by (host name, serial number).
Here you can find detailed installation information about ElasticXL:
Install ElasticXL Cluster
>>> Please note that this information is not yet an official statement from Check Point and may change at any time. <<<
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah for a while, all I did was Solaris and Firewall-1 v4.0 and v4.1 ("Check Point 2000", NG, and later NG-X) at the time, on the Netra T1 servers. The coolest little 1U things at the time. I didn't care much for the long list of "required Solaris patches" that were on the install requirements, but the other Unix nerds on the network built a nice NFS repo for everything for me. Later the other Unix nerds helped me work out an auto-install for everything, too. We had the earliest days of deployment automation; I just fed a MAC address to one of the build scripts, booted it up, PXE did its thing, and *poof* I had a working firewall in about 2 hours. I was unafraid to hack together an objects.C file out of band with a script of my own. Ran fwstop, copy the file over, fwstart, and had a pretty good template. I don't recall a ton of of the details now, tho (SIC? something else...). But yeah, Firewall-1 on Solaris was incredibly solid.
Oh the good ol' days of having to rip open that cardboard packaging to get the certificate key, go to the license site (which may or may not have been online that day) and register the certkey to then generate the license. 🙂 The old days before the automatic 15-day eval.
68 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good info.. seems like a step forward compared to load sharing clusterXL.
Would the other members need uplinks too to avoid the single point of failure?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The interface configuration of each node in an ElasticXL configuration is similar ClusterXL (dedicated sync interface plus data/management interfaces).
Which means you would need interface bonds for redundancy on the relevant interfaces per your business requirements.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@PhoneBoy has been absolutely right with his statement.
The yellow arrows do not represent the physical wiring. It only show that the connections is forwarded via the data interface to the other gateway.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sounds like IPSO cluster from the good old days 😄
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Man, IPSO cluster was the BEST!! 👌
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Even VRRP still used the sync piece of ClusterXL.
Though I also remember the days of Stonebeat and Qualix HA 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh yeah... I did Stonebeat Full Cluster a few times. That was a really cool FC product, in my opinion. I remember RainWall as well, but never used it. ISTR there was another cluster vendor at the time, but I can't remember now who it was...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Personally, I was always super impressed with management server running on Solaris...NEVER an issue. You know its rock solid when customers just call you to say that lol
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah for a while, all I did was Solaris and Firewall-1 v4.0 and v4.1 ("Check Point 2000", NG, and later NG-X) at the time, on the Netra T1 servers. The coolest little 1U things at the time. I didn't care much for the long list of "required Solaris patches" that were on the install requirements, but the other Unix nerds on the network built a nice NFS repo for everything for me. Later the other Unix nerds helped me work out an auto-install for everything, too. We had the earliest days of deployment automation; I just fed a MAC address to one of the build scripts, booted it up, PXE did its thing, and *poof* I had a working firewall in about 2 hours. I was unafraid to hack together an objects.C file out of band with a script of my own. Ran fwstop, copy the file over, fwstart, and had a pretty good template. I don't recall a ton of of the details now, tho (SIC? something else...). But yeah, Firewall-1 on Solaris was incredibly solid.
Oh the good ol' days of having to rip open that cardboard packaging to get the certificate key, go to the license site (which may or may not have been online that day) and register the certkey to then generate the license. 🙂 The old days before the automatic 15-day eval.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not that I remember anything about it, as I was a teenager living in war zone on totally another continent, so if anyone said Solaris to me back then, it would have meant absolutely nothing 🤣🤣🤣
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Before SIC, there was fw putkey.
I once got a call about trouble with a VPN after an upgrade to R62. Turns out the other end of the tunnel was running 4.1 on Solaris 2.6, I think. It was definitely on an Ultra 5 with the Happy Meal Ethernet (100 megabit with a side of 10 megabit!). So many wild stories from that single call.
Lately, I'm making myself learn PowerShell, and using Windows Server with Hyper-V for my main VM host to help with this goal. Outside of that, I run a lot of illumos (community fork of OpenSolaris made after Oracle bought Sun). ZFS, Dtrace, zones, SMF, fmd, and more recently bhyve. Outside of the XML manifests for SMF, the internals all still feel very current and capable. I'm willing to put up with XML for the benefits SMF provides. It's leaps and bounds better than systemd unit files.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now I'm going to be a pilosopher too:
I also started in 1996 with the first Check Point Firewalls I believe in version 2.01.
At that time, rules.def and objects.C were still edited by hand. No management server.
With version 3, a tool was provided with which the rules and objects could be created on the gateway.
At that time, a competitor's Raptor firewall was the first FW on the market and it already used Stonebeat.
Raptor is an application-level firewall driven by proxies, which is a bit safer than stateful-inspection or packet-filtering firewalls at this time.
Then came the good old days with Check Point Firewall-1, 4.0, 4.1, Stonebeat Full Cluster, Solaris and IPSO cluster...and my personal favourite version R65 HF60 (not HF 70).
But we now live in the world of 1TBps firewall throughput and I prefer the modern techniques:
Maestro:
- Maestro Fast Forwarding
- HyperFlow
- Maestro Autoscaling
- Lightspeed Appliance
...
PS:
Only with the kernel versions Check Point should also arrive in today's time and perhaps use a 5.x or 6.x;-)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow Heiko, it's interesting how we all seem to have been involved in the same tech throughout our many many years, and better still to see how things have progressed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @genisis__ ,
Even found a few old books in the cupboard:
@PhoneBoy must not be sad now. The book is at home in the cupboard.;-)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow, Im sure those books were golden back in the day 🙂
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
just for the hell of it, dug these out!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good ol' R70 P-1 hehe
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice! 😁
NGX: The only version that came in hardback. And.... if you got lucky you got a free backpack or shoulder bag with the book.
I had all that and also NGX III (CCSE Plus). That was the best course, covering IKEView and INFOView 😄
Many hand written notes in those books.
Also Nokia NSA I & NSA II and PIX and Juniper SRX books (where you have Stonesoft).
Setting up for the VSX NGX courses back then was all sorts of fun.
It took hours to set up and an hour or so to tear down. Now I can start a VSX (CCVS) lab in the cloud in 2 or 3 minutes 😆
VMWare workstation was great but only so much could be running on one under-powered host. And then came the VLAN part...
It took careful planning and documenting. I had to take a picture of how the classroom looked.
reset_gw
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Don .... I have the shoulder bag!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Me too. 😀
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Those were the good old days;-)
Now we're having fun with Maestro, ElasticXL and VS Next.
Architecture and Performance Tuning - Link Collection
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now that brings back memories!
Actually got certified with Stonesoft back in the day, and did a eval of IPSO/Checkpoint, Cisco and StoneSoft. At the time Stonesoft out performed the lot but I made a number of observations to the poor SE (who still remembers me!).
Anyone remember Raptor running on Solaris!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just googled Stonesoft and not surprising, it was Finnish company. Anything that ever came from Finland, rock solid.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If I remember correctly the founders where ex-Checkpoint.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe thats true, yes.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are truly showing our age!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Speak for yourself mate 😉
Im only 43 years old, so not THAT old LOL
Okay, depends who you ask 🤣🤣
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very interesting indeed.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All very off-topic but brings back lots of memories, so I can't resist .. 🙂
I can go further back. 1992 be be exact. The first IP/Internet firewall was written by Marcus Ranum while he was at DEC (and even contains code "shamelessly stolen" from Guido Van Rossum, according to the source code comments). This was the DEC SEAL, a 3 node fw (bastion host, filter and proxy) which we initially compiled on-site at the customer on DEC Ultrix boxes. All great fun 🙂 Then came Altavista Firewall which was a SEAL in 1 box and had a very reasonable Web GUI. We even had "clustering" for Altavista for some customers.
Around this time 1994/5ish Checkpoint showed their stateful-firewall and the rest is history (and some of it has been re-written by the winners).
Even before that there was a DECnet firewall but we won't go there because I guess there is nobody here who goes that far back 😉
D
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 10 | |
| 10 | |
| 10 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter