- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- R82 - ElasticXL
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R82 - ElasticXL
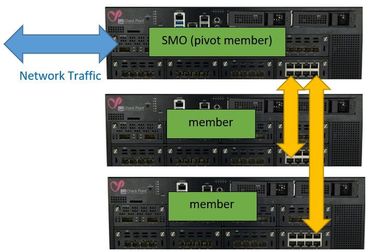
ElasticXL is a new cluster technology that enables simplified operation with a single management object with automatic configuration and software synchronisation between all cluster members.
ElasticXL is expected to be delivered with R82 or later versions. ElasticXL is based on similar technology to Maestro, but without MHOs. It is based on Check Point's SP versions for a scalable platform that allows you to increase the performance of the security gateways almost linearly.
This is achieved naturally by load balancing between individual gateways that operate in a cluster as a single entity.
This new cluster technology will some of the Maestro featchers such as SMO (Singel Management Object) use.
A ElasticX gateway will work as a pivot member and act simelar as a MHO's in a Maestro environment and simultaneously takes on the role of SMO.
The pivot member takes over the network connection and controls the ARP requests in the network. The pivot member distributes the connections via a distribution matrix to the connected member in the security group similar to a Maestro environment.
Same as the Maestro environments, the familiar SP commands will also be available here and there will also be a gclish. The management traffic will be handled by the SMO (pivot member).
Installation process:
1) The gateways are installed as usual via the First Configuration Wizard. ElasticXL" is now selected instead of "ClusterXL" on the product page.
2) After that, the SIC to the first gateway (pivot member) will be established single gateway (not as a cluster object). Afterwards, the policy can be installed.
3) In the following step the next gateways can be added by (host name, serial number).
Here you can find detailed installation information about ElasticXL:
Install ElasticXL Cluster
>>> Please note that this information is not yet an official statement from Check Point and may change at any time. <<<
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
68 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Review the Known Limitations for R82, specifically the following two sections: ElasticXL and Maestro/Scalable Platforms (which ElasticXL is an implementation of).
The only place where ClusterXL has to be used, to the best of my knowledge, is a "Full HA" configuration (management + gateway on both cluster members).
For an HA-only cluster (no load sharing) you have to set up ElasticXL as "Dual Site" where each site has a single member.
Otherwise, I can't think of a reason one should choose ClusterXL over ElasticXL (beyond familiarity with ClusterXL).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are a few more limitations compared to vanilla ClusterXL:
- Central licensing isn't possible with ElasticXL, since the management sees all members as one "device"
- Branded servers can't fetch their own licenses with ElasticXL (not sure why this is)
- ElasticXL doesn't support open servers
- ElasticXL only supports KPPAK, so no HyperFlow
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ElasticXL should work with Open Servers similar to how you can make it work with VMs.
I believe both will be supported in the near future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
KSFW is the limitation for Hyperflow as I understood not KPPAK so shouldn't be a problem.
Refer: sk167052, sk178070
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello PhoneBoy,
you said that for an HA-only cluster (no load sharing) you have to set up ElasticXL as "Dual Site" where each site has a single member. This is very useful information, it's like you have active and standby gateway in ClusterXL HA but realised as ElasticXL.
But I think that is better to have a both gateways as Active/Active to process traffic equally, to waste CPU and memory equally than to have one standby gateway which doesn't work anything (it only waiting for something to happen with active gateway).
I think that ElasticXL has a lot of benefits compared to ClusterXL (configuration, management, performance, etc).
I will prefer to use ElasticXl in some future configurations, when Gaia R82 become recommended version.
As far as I know, currently there is no a way to automatically convert ClusterXL to ElasticXL but I'm very interested in how to do it in future, what are the steps and what is the down time?
Best regards,
Milan Babic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are planning a migration tool of sorts for converting from ClusterXL to ElasticXL.
Not sure on the exact timing of this, but it might be by the time R82 is considered the recommended version. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was playing around in demo point R82 elastic XL and its great. I never realized you do failover with same command clusterXL_admin down like normal clusterXL.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @the_rock ,
Our recommendation for site or member failover to use either from gclish:
[Global] SMO-s01-01> set cluster members-admin-state
[Global] SMO-s01-01> set cluster sites-admin-state
end from expert to use the new command cluster-cli(if you run it without param you will get textual UI which will show you all options)
[Expert@SMO-s01-01:0]# cluster-cli set --help
Usage: cluster-cli set [OPTIONS] COMMAND [ARGS]...
Cluster set commands. Tip: Use shortcut command 'cset'
Options:
--help Show this message and exit.
Commands:
members-admin-state Manage the administrative state of cluster members.
members-reboot Reboot members command Will apply to all given...
sites-admin-state Manage the administrative state of cluster sites.
without param, see attached screenshot
Regards,
Shai
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Okay, good to know!
Andy
Best,
Andy
Andy
R82 - ElasticXL
ElasticXL is a new cluster technology that enables simplified operation with a single management object with automatic configuration and software synchronisation between all cluster members.
ElasticXL is expected to be delivered with R82 or later versions. ElasticXL is based on similar technology to Maestro, but without MHOs. It is based on Check Point's SP versions for a scalable platform that allows you to increase the performance of the security gateways almost linearly.
This is achieved naturally by load balancing between individual gateways that operate in a cluster as a single entity.
This new cluster technology will some of the Maestro featchers such as SMO (Singel Management Object) use.
A ElasticX gateway will work as a pivot member and act simelar as a MHO's in a Maestro environment and simultaneously takes on the role of SMO.
The pivot member takes over the network connection and controls the ARP requests in the network. The pivot member distributes the connections via a distribution matrix to the connected member in the security group similar to a Maestro environment.
Same as the Maestro environments, the familiar SP commands will also be available h
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter