- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Check Point
for Beginners
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Check Point for Beginners
- :
- Part 2 - Preparing the Lab
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
OPEN OTHER ARTICLES
 Part 1 - The Architecture
Part 1 - The Architecture
 Part 3 - Installing Security Management Server
Part 3 - Installing Security Management Server
 Part 4 - Installing Security Gateway
Part 4 - Installing Security Gateway
 Part 5 - Gaia WebUI and CLI
Part 5 - Gaia WebUI and CLI
 Part 6 - Working with SmartConsole
Part 6 - Working with SmartConsole
 Part 7 - Managing Security Policies
Part 7 - Managing Security Policies
 Part 8 - Network Address Translation
Part 8 - Network Address Translation
 Part 9 - Application Control, URL Filtering and Content Awareness
Part 9 - Application Control, URL Filtering and Content Awareness
 Part 10 - Identity Awareness
Part 10 - Identity Awareness
 Part 11 - Threat Prevention
Part 11 - Threat Prevention
 Part 12 - Logs and Reporting
Part 12 - Logs and Reporting
 Site to Site VPN in R80.x - Tutorial for Beginners
Site to Site VPN in R80.x - Tutorial for Beginners
 Absolute Beginner’s Guide to R80.x
Absolute Beginner’s Guide to R80.x
 Handling Traffic in the Access Policy - Knowledge Nuggets
Handling Traffic in the Access Policy - Knowledge Nuggets
 Video - Security Administration Experience
Video - Security Administration Experience
 Video - Securing Hybrid Cloud Environment
Video - Securing Hybrid Cloud Environment
 Video - Smart-1 Cloud - Cloud Based Security Management
Video - Smart-1 Cloud - Cloud Based Security Management
 Video - Container Security
Video - Container Security
 Video - Identity Based Segmentation
Video - Identity Based Segmentation
 Video - Securing Public Cloud Environment
Video - Securing Public Cloud Environment
 Video - Threat Hunting, Detection, and Monitoring
Video - Threat Hunting, Detection, and Monitoring
 Video - Firewall as a Service (FWaaS)
Video - Firewall as a Service (FWaaS)
 Video - Application Control and URL Filtering
Video - Application Control and URL Filtering
 Video - TLS Inspection
Video - TLS Inspection
 Video - Hyper Scale Clustering with Quantum Maestro
Video - Hyper Scale Clustering with Quantum Maestro
 Video - Check Point R81.X - Crash Course - Introduction
Video - Check Point R81.X - Crash Course - Introduction
 Video - Check Point R81.X - Crash Course - Admin GUI
Video - Check Point R81.X - Crash Course - Admin GUI
 Video - Check Point R81.X - Crash Course - SmartConsole
Video - Check Point R81.X - Crash Course - SmartConsole
 Check Point R81.X - Crash Course - Admin GUI Part 2
Check Point R81.X - Crash Course - Admin GUI Part 2
 Network Security
Network Security
PREVIOUS ARTICLE
TO READ THE FULL POST
it's simple and free
NEXT ARTICLE
Part 2 - Preparing the Lab
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-06-11
04:20 AM
Introduction
Our lectures are designed for mastering both theoretical and practical aspects of Check Point products. Before moving forward, we need to build a lab environment. All further discussions have in mind the virtualization lab setup described below.
Attention: this document refers to R80.10 version. You can use exactly the same settings to run any of R81.x versions in the lab.
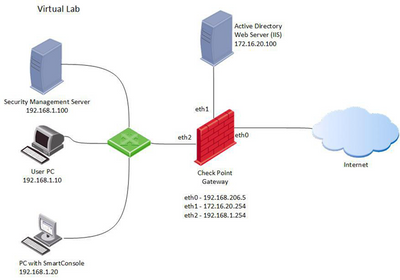
Virtual Lab
The virtual lab layout is presented on the diagram below.
It consists of five virtual machines
- Security Management Server (SMS)
- Security Gateway (SG)
- Lab User PC
- PC with SmartConsole[1]
- Windows Server (Active Directory and IIS are enabled)
Virtualization platform
While we are using VMware Workstation 14 in our lab, you can also use ESXI or Virtual box as a virtualization platform.
Installation Software Images
To install and setup all Check Point machines you need R81.20 Check Point ISO file. It can be found here.
You will also need to install Windows Client (Windows 7 or higher) and Windows Server (2012 or higher) machines.
Note: Installation and setup of Windows machines are out of scope.
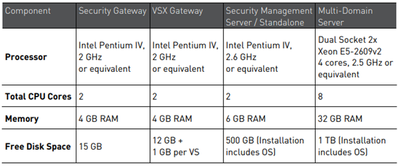
Hardware Requirements
Minimal Hardware requirements for Gaia R80.10 Open Server installation are listed in Check Point R81.20 Release Notes:
Although going below these requirements is definitely not recommended in the production, we can have some allowances in the lab.
These are recommended virtual machine parameters for our lab:
- SMS: 6GB RAM, 4 CPU Cores, 80GB HDD
- SG: 4GB RAM, 2 CPU Cores, 50GB HDD
You can chose your own RAM, CPU and HDD settings for Windows lab machines.
We believe the lab can be performed on a virtualization host with the following parameters:
- 4 cores CPU,
- 16BG RAM,
- 500GB HDD/SSD.
Network Layout
We recommend using the same IP addresses as shown on the lab diagram above. Make sure you use different VMnet segments for each of the lab networks.
All three Security Gateway network interfaces should be defined in the different network segments.
In case of VirtualBox based lab, chose Host-Only Ethernet Adapter.
[1] In case you are building this lab on your Windows PC, your virtualization host can take the role of SmartConsole Client.
----------------------------
Authors and contributors
Author - Evgeniy Olkov, CTO at TS Solution.
Founded in 2010, the TS Solution is a fast growing Russian company, focused on integrating high-tech networking, security and server virtualization systems and technologies, along with maintenance and professional services.
Translation and editing - Valeri Loukine
Review and editing - Dameon Welch-Abernathy
Labels
Introduction
Our lectures are designed for mastering both theoretical and practical aspects of Check Point products. Before moving forward, we need to build a lab environment. All further discussions have in mind the virtualization lab setup described below.
Attention: this document refers to R80.10 version. You can use exactly the same settings to run any of R81.x versions in the lab.
Virtual Lab
The virtual lab layout is presented on the diagram below.
It consists of five virtual machines
- Security Management Server (SMS)
- Security Gateway (SG)
- Lab User PC
- PC with SmartConsole[1]
- Windows Server (Active Directory and IIS are enabled)
Virtualization platform
While we are using VMware Workstation 14 in our lab, you can also use ESXI or Virtual box as a virtualization platform.
Installation Software Images
To install and setup all Check Point machines you need R81.20 Check Point ISO file. It can be found here
...
16 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter