- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Check Point
for Beginners
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Educational Resources
- :
- Check Point for Beginners
- :
- Part 12 - Logs and Reporting
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
OPEN OTHER ARTICLES
 Part 1 - The Architecture
Part 1 - The Architecture
 Part 2 - Preparing the Lab
Part 2 - Preparing the Lab
 Part 3 - Installing Security Management Server
Part 3 - Installing Security Management Server
 Part 4 - Installing Security Gateway
Part 4 - Installing Security Gateway
 Part 5 - Gaia WebUI and CLI
Part 5 - Gaia WebUI and CLI
 Part 6 - Working with SmartConsole
Part 6 - Working with SmartConsole
 Part 7 - Managing Security Policies
Part 7 - Managing Security Policies
 Part 8 - Network Address Translation
Part 8 - Network Address Translation
 Part 9 - Application Control, URL Filtering and Content Awareness
Part 9 - Application Control, URL Filtering and Content Awareness
 Part 10 - Identity Awareness
Part 10 - Identity Awareness
 Part 11 - Threat Prevention
Part 11 - Threat Prevention
 Site to Site VPN in R80.x - Tutorial for Beginners
Site to Site VPN in R80.x - Tutorial for Beginners
 Absolute Beginner’s Guide to R80.x
Absolute Beginner’s Guide to R80.x
 Handling Traffic in the Access Policy - Knowledge Nuggets
Handling Traffic in the Access Policy - Knowledge Nuggets
 Video - Security Administration Experience
Video - Security Administration Experience
 Video - Securing Hybrid Cloud Environment
Video - Securing Hybrid Cloud Environment
 Video - Smart-1 Cloud - Cloud Based Security Management
Video - Smart-1 Cloud - Cloud Based Security Management
 Video - Container Security
Video - Container Security
 Video - Identity Based Segmentation
Video - Identity Based Segmentation
 Video - Securing Public Cloud Environment
Video - Securing Public Cloud Environment
 Video - Threat Hunting, Detection, and Monitoring
Video - Threat Hunting, Detection, and Monitoring
 Video - Firewall as a Service (FWaaS)
Video - Firewall as a Service (FWaaS)
 Video - Application Control and URL Filtering
Video - Application Control and URL Filtering
 Video - TLS Inspection
Video - TLS Inspection
 Video - Hyper Scale Clustering with Quantum Maestro
Video - Hyper Scale Clustering with Quantum Maestro
 Video - Check Point R81.X - Crash Course - Introduction
Video - Check Point R81.X - Crash Course - Introduction
 Video - Check Point R81.X - Crash Course - Admin GUI
Video - Check Point R81.X - Crash Course - Admin GUI
 Video - Check Point R81.X - Crash Course - SmartConsole
Video - Check Point R81.X - Crash Course - SmartConsole
 Check Point R81.X - Crash Course - Admin GUI Part 2
Check Point R81.X - Crash Course - Admin GUI Part 2
 Network Security
Network Security
PREVIOUS ARTICLE
TO READ THE FULL POST
it's simple and free
NEXT ARTICLE
Part 12 - Logs and Reporting
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
2020-06-11
04:59 AM
Logging and Reporting are major points for any security solution. In this lecture, we talk about working with logs and security reports in our Check Point environment.
New User Interface
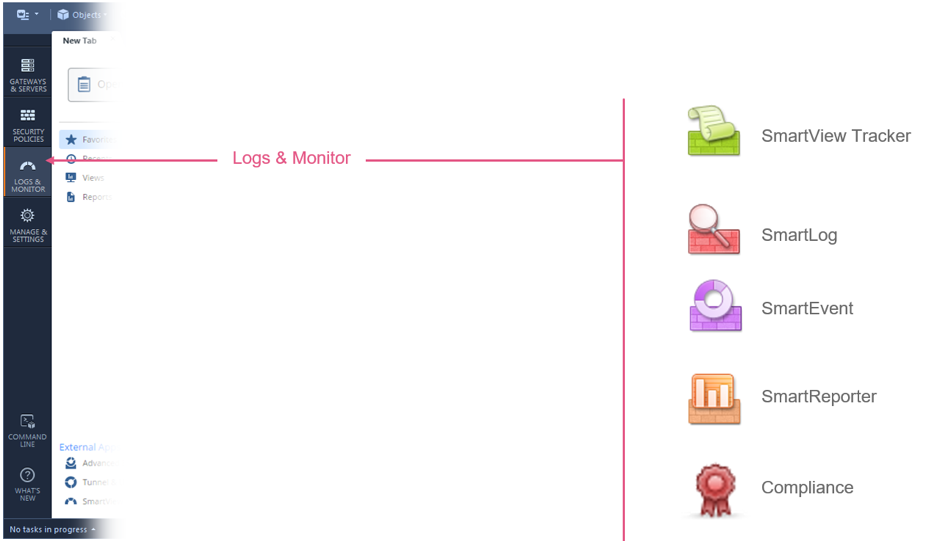
Check Point has completely re-worked the admin user interfaces in the R80 versions. If you have some experience with previous versions (R77 and below), you can appreciate how many different utilities are now unified under Logs & Monitor tab in SmartConsole:
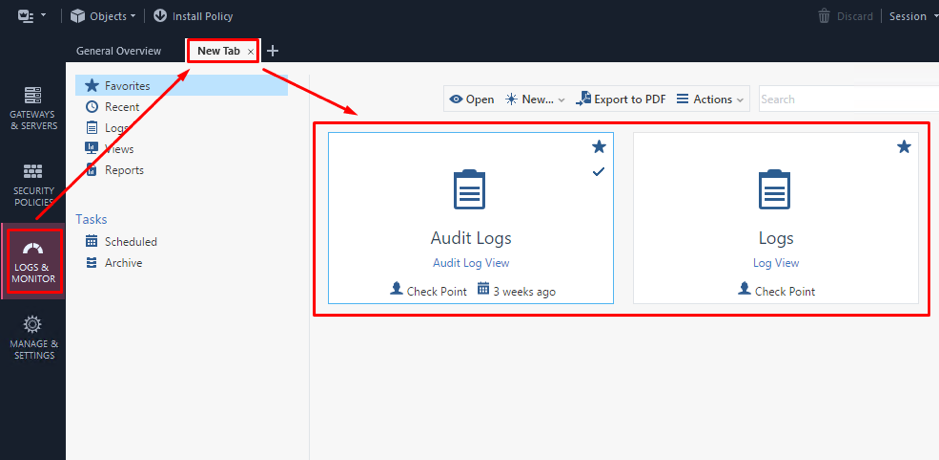
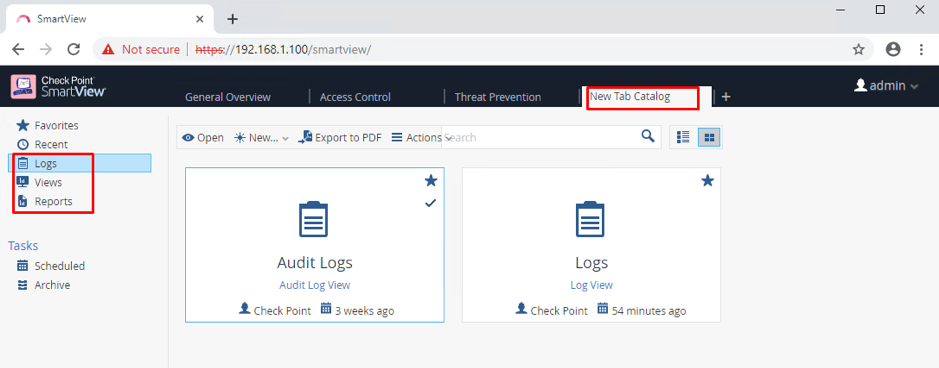
Let’s take a closer look. Go to Logs & Monitor and open a New Tab there. This is what you will see:
There are two default options:
- Audit Logs View – this shows all events related to administrative operations: admin logins and logouts events, configuration changes, policy and objects edits, etc. This is a standard Audit tool to track admin actions over time.
- Logs View – shows security logs generated by the various Software Blades: Firewall, Anti-Virus, IPS, etc. We have looked at some security logs multiple times in our previous lectures.
The same User Interface allows us to work with Reports and various Dashboards (Views). SmartEvent should be enabled for reporting. We will address this a bit later.
Let’s look at the security logs first. Double-click on Logs to open the view.
Working with Logs
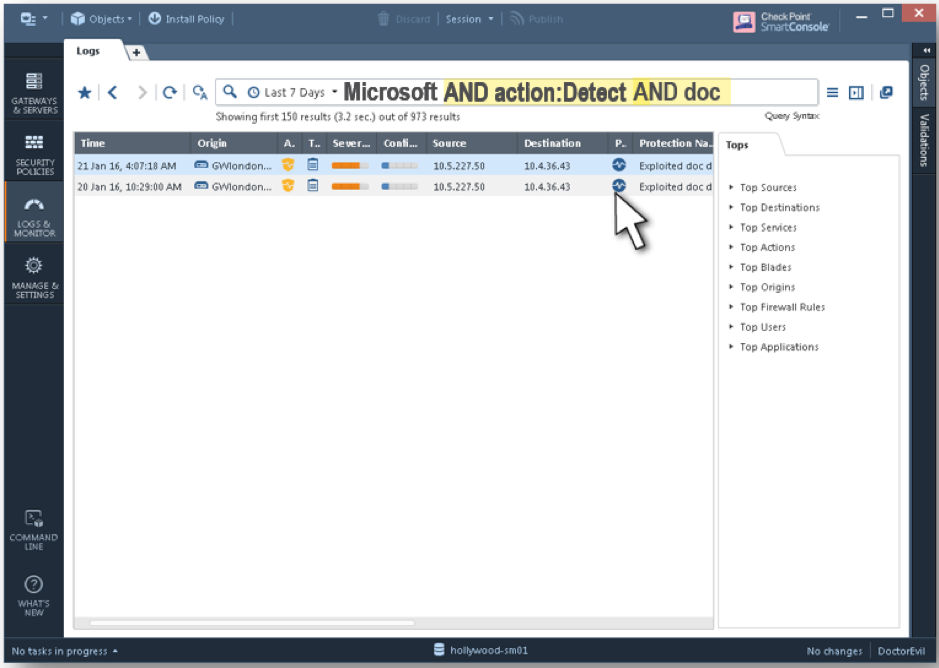
In the log window we have all security logs sent by various Software Blades. There can be a lot of them in a busy environment. To simplify log management, Check Point uses elaborate search capabilities. There are multiple options available:
- Free text search (for example, “Microsoft”);
- Filtering via Software Blade. Enter “blade:” in the search field and then choose one you need (firewall, IPS, antivirus etc.);
- Predefined fields search: src, dst, action and so forth. For example: action:prevent;
- You can use logical operators (AND, OR, NOT);
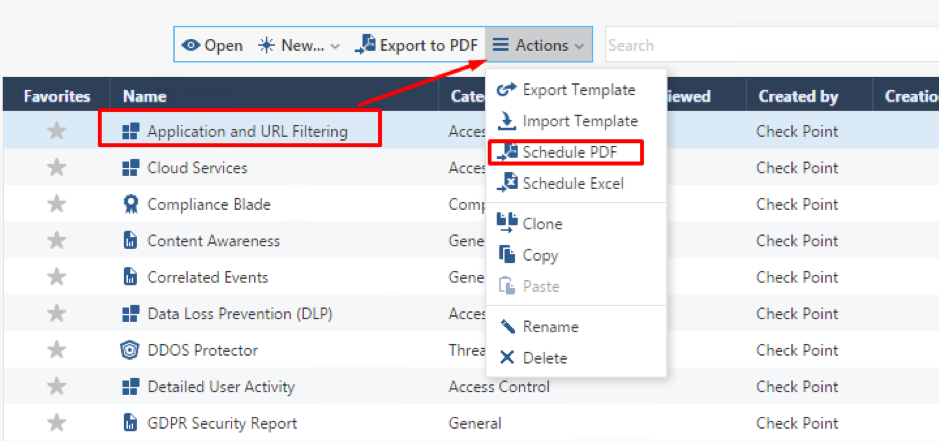
You can combine multiple filters in a single search. You can also add a custom filter with a right click on a log field:
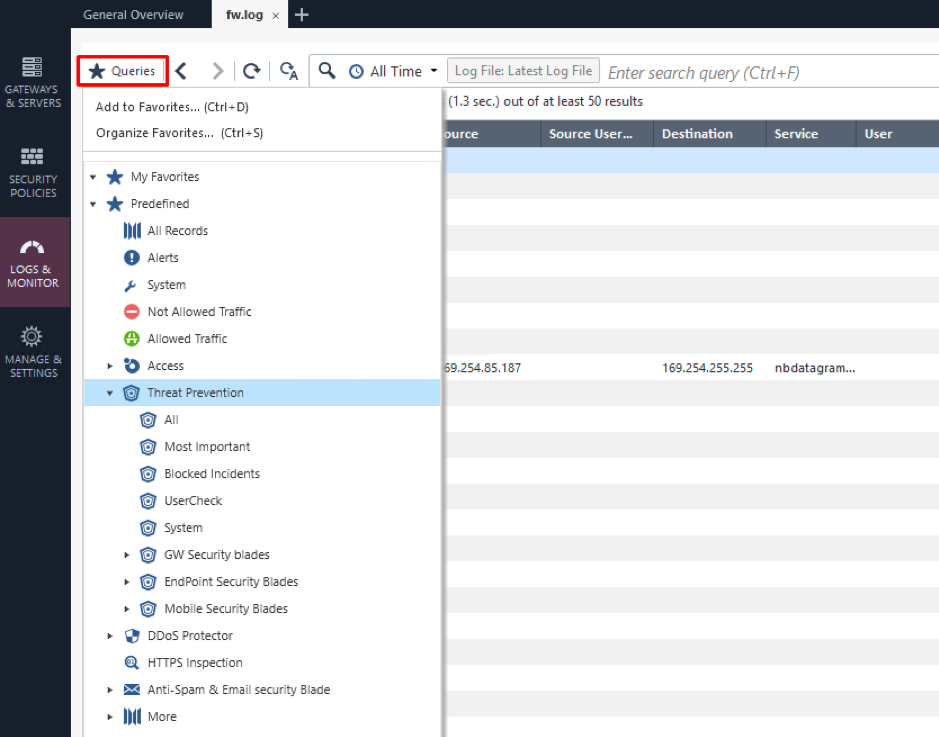
There are multiple pre-defined filters in the Queries menu on the left:
You can add your own filters there by pressing Ctrl+D.
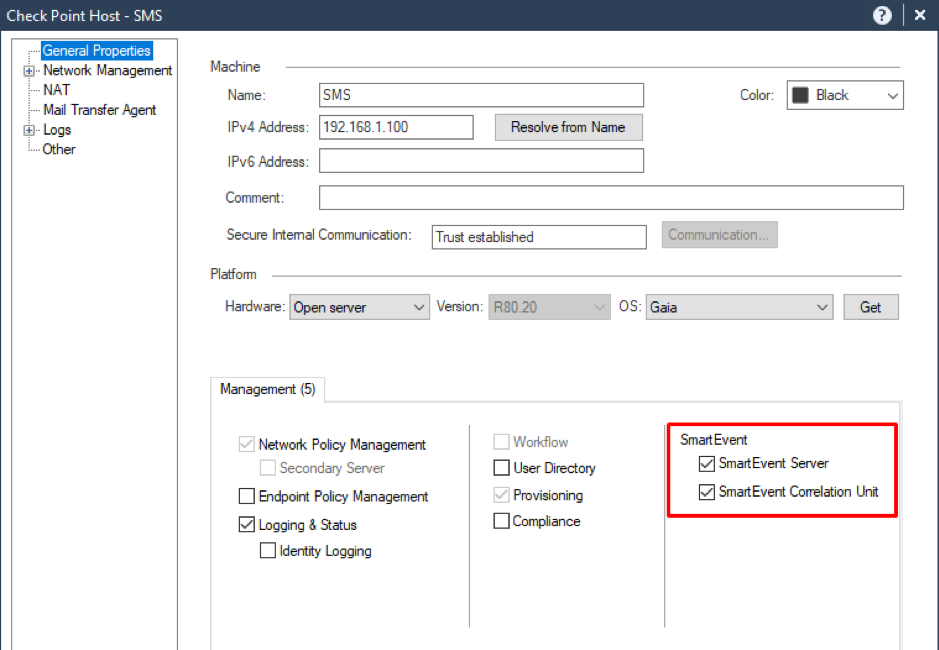
SmartEvent
To work with Views & Reports, we need to enable the SmartEvent Software Blade on our Security Management Server:
Choose both SmartEvent Server and SmartEvent Correlation Units and press OK.
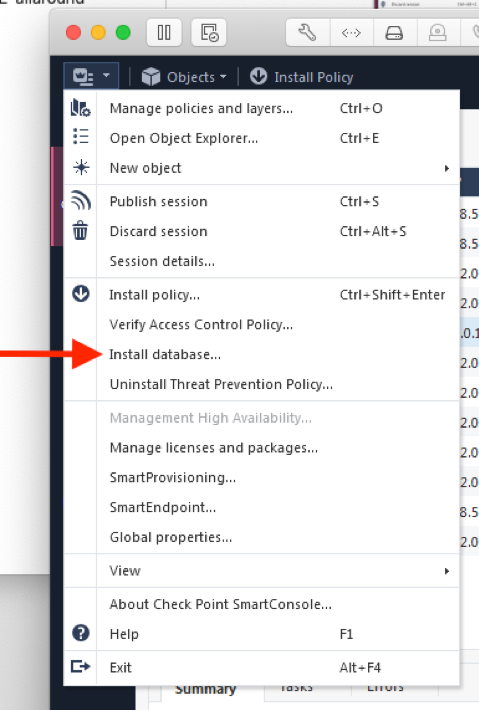
Then install database on the Security Management Server object:
Once done, you will see Views and Reports options in Logs & Reports window.
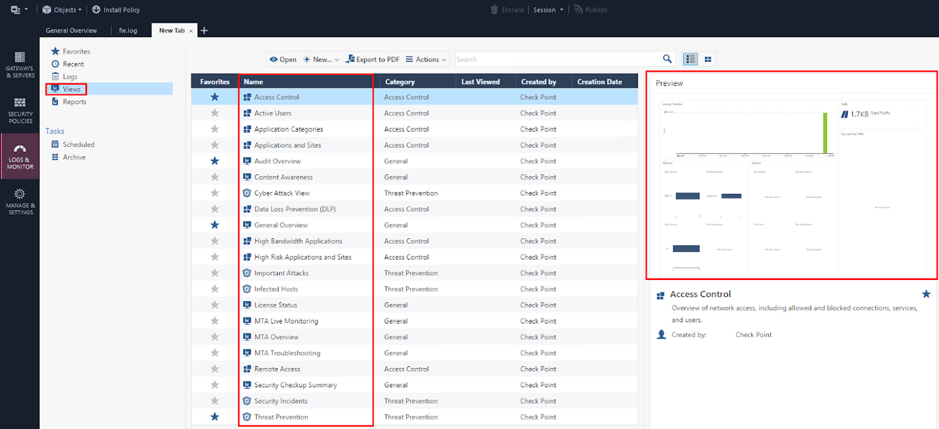
Views
There are multiple default views available. When choosing a view, you can see a preview of the one you are selecting.
Views can be modified. You can also create your own as well as import and export them. You can play with different views in the lab, but since we only have a limited number of logs there, it is much better to run SmartConsole in Demo View when doing so.
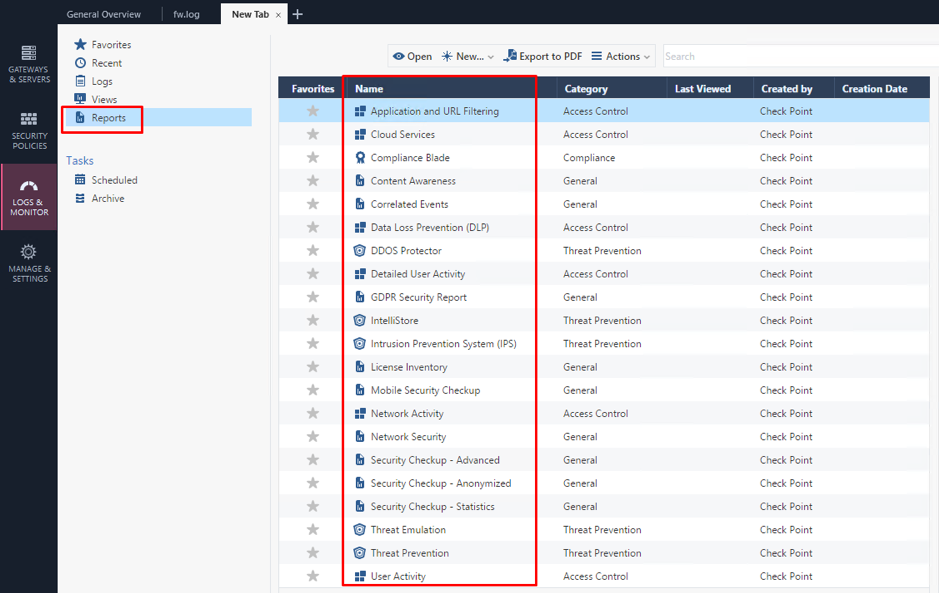
Reports
Detailed security information can be collected and processed as Reports. Here as well, there are quite a number of pre-defined reports already available:
If required, Reports can be scheduled and sent via email.
Same as Views, Reports can be modified, customized, exported, and imported.
SmartView via a Browser
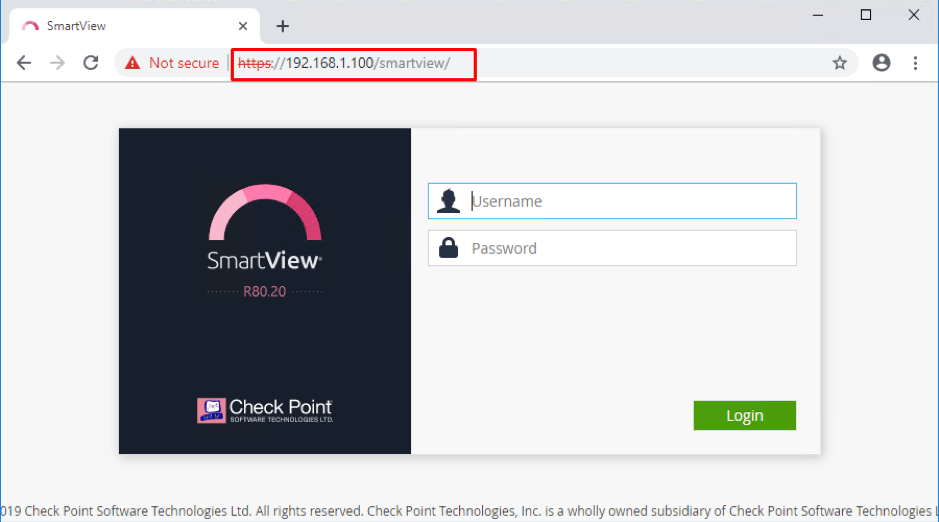
With R80.x, you can work with Logs and Views in a browser, without opening SmartConsole. This functionality is called SmartView. To access SmartView, open the following URL:
https://192.168.1.100/smartview
In the logon screen, enter your admin credentials:
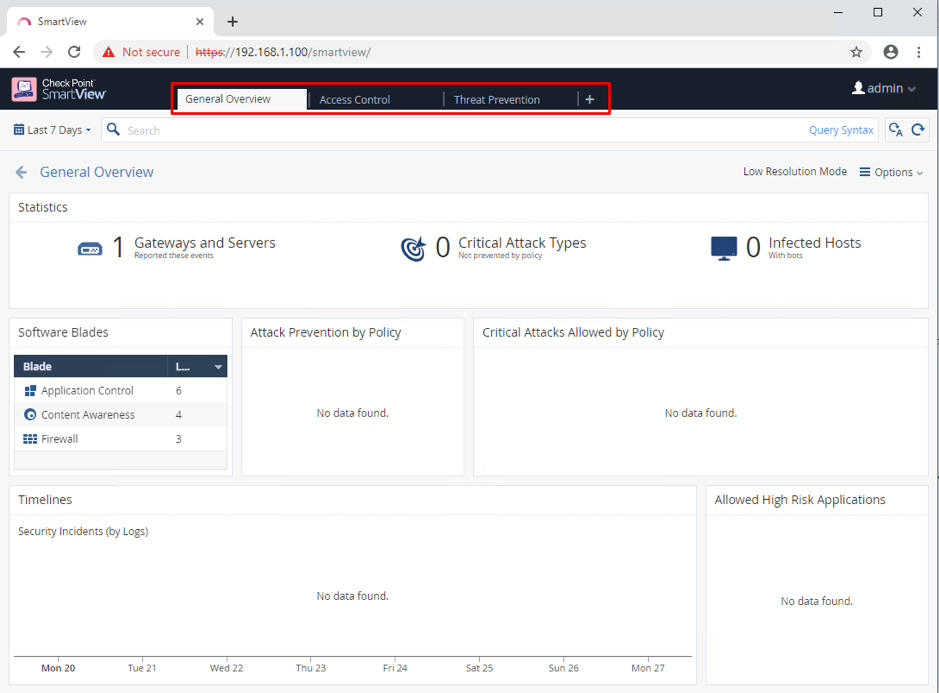
Once logged in, the look and feel is very similar to SmartConsole:
The same tabs you see in Logs and Reporting in SmartConasole are available:
Browser-based SmartView is very handy when security operators need simple access to the logs and security events but do not need other administration tools. In such cases you do not need to deploy SmartConsole on their machines.
To learn more about SmartView capabilities, refer to Check Point Infinity Talks: R80.20 log enhancements How-To video on CheckMates.
----------------------------
Authors and Contributors
Author - Evgeniy Olkov, CTO at TS Solution.
Founded in 2010, the TS Solution is a fast growing Russian company, focused on integrating high-tech networking, security and server virtualization systems and technologies, along with maintenance and professional services.
Translation and editing - Valeri Loukine
Review and editing - Dameon Welch-Abernathy
Labels
Logging and Reporting are major points for any security solution. In this lecture, we talk about working with logs and security reports in our Check Point environment.
New User Interface
Check Point has completely re-worked the admin user interfaces in the R80 versions. If you have some experience with previous versions (R77 and below), you can appreciate how many different utilities are now unified under Logs & Monitor tab in SmartConsole:
Let’s take a closer look. Go to Logs & Monitor and open a New Tab there. This is what you will see:
There are two default options:
- Audit Logs View – this shows all events related to administrative operations: admin logins and logouts events, configuration changes, policy and objects edits, etc. This is a standard Audit tool to track admin actions over time.
- Logs View – shows security logs generated by the various Software Blades: Firewall, Anti-Virus, IPS, etc. We have looked at some security logs multi
2 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter