- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Properly defining the Internet within a securi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Properly defining the Internet within a security policy
Let's discuss!
There are various methods of defining the Internet within your firewall security policy.
I've showcased the five most common methods in the screen shot below.
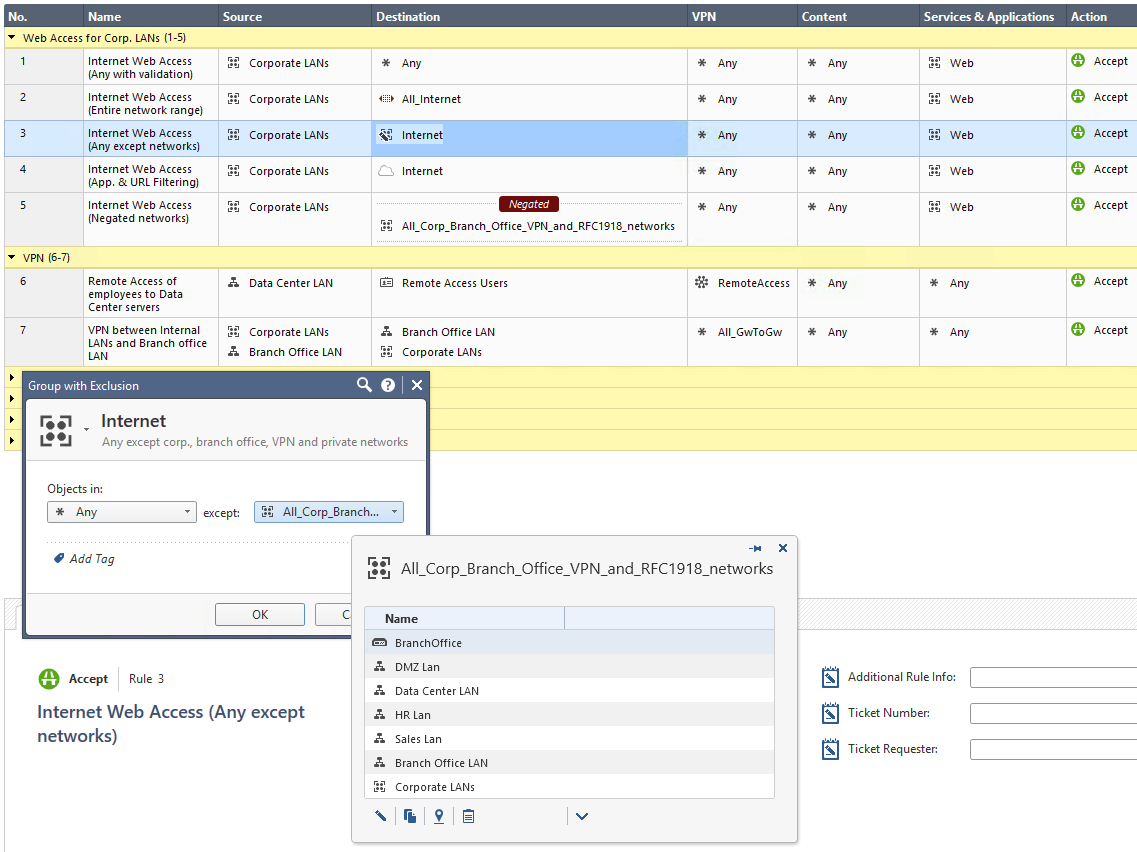
The proper firewall definition of the Internet depends on your needs!
This discussion shall raise your awareness that it's required to evaluate your specific demand to avoid using * Any or All_Internet by default.
Method 1: Using the default * Any definition
Pro: Allows for proper Security Policy verification checks.
Con: Any is not the Internet. In an ideal security world, you shouldn't use * Any in any of your firewall rules.
Method 2: Using the default IP Address range: All_Internet (0.0.0.0-255.255.255.255)
Pro: While Hide-NAT on "Any" source doesn't work, using All_Internet as the source will do the job.
Con: The Internet consists of various networks, public, private and other ones. In a security environment you operate all kind of corporate networks, DMZs, VPNs, Remote Users, Office Modes and many more entities using IP addresses. From a firewall security point of view the Internet definition means everything that is not internally, branch office, Site-to-Site or Remote Access VPN connected. For a firewall the Internet is everything else, public, untrusted, external. A simple IP Address range object with the name All_Internet provokes many misunderstandings. A security reviewer, like me, would be happy that * Any was replaced with an object someone hopefully took care of properly defining what the Internet for that specific firewall implementation is. Only when looking deeper into the object it gets clear that this definition is even more worse than * Any because it might supersede the automatic validation checks Check Point does. Please see the Global Properties for Non Unique IP Adresses shown below.
Method 3: Using a Group with Exclusion (Any except all corp. networks, branch office networks, VPN encryption domains, office mode networks, RFC 1918 networks and so on)
Pro: Easy to use and understandable for humans within normal firewall administration.
Con: Groups with Exclusion are very complex for automatic firewall validation checks, hard to troubleshoot for humans, known to sometimes cause issues when used in VPN encryption domains and therefore have many limitations (sk97246, sk101506, sk107543, sk107417, ..). Also, what is * Any from a firewalls perspective? How does a firewall define * Any? Are there exclusions from * Any? For Services everyone knows that Check Point per default excludes X11 from Any. How about Networks?
Method 4: Using the Application and URL Filtering object 'Internet'
Pro: Only applies to traffic heading outside the corporate network - to the DMZ and external interfaces. The object distinguishes between internal and external addresses.
Con: This is only the default destination for Application and URL Filtering rules so you can only use this object in the destination column of Application and URL Filtering enabled rules and layers.
Method 5: Negating a group that contains all your networks (similar to Method 3 without using a Group without Exclusion)
Pro: Perfect definition of the Internet for the firewall and all of its automatic verification and validation mechanisms. Simple negation of all networks that your firewall 'knows' not to be part of the public, untrusted, external Internet.
Con: Harder to understand for humans, especially in security policies with advanced complexity.
Appendix:
Menu > Global Properties > Non Unique IP Addresses
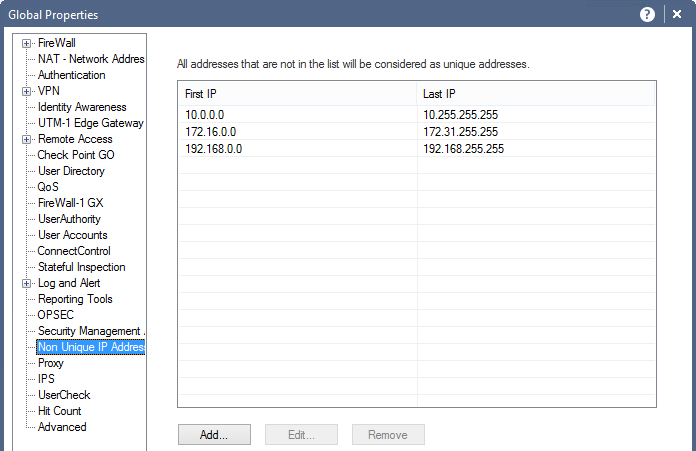
In the above window you can see the non-unique IPv4 and IPv6 address ranges.
Security Management considers addresses that are routable on the Internet as unique, and private, non-routable addresses as being non-unique (duplicated). It is possible to add address ranges to the default list. There is normally no need to change the default addresses.
This list is used by SmartDashboard to perform automatic validity checks on addresses.
IPv4 Addresses
RFC 1918 documents private address spaces which may be used on internal networks that will not have hosts directly connected to the Internet. The Internet assigned Numbers authority (IANA) has set aside the following three blocks of IP addresses for internal (private) network use:
- Class A network numbers: 10.0.0.0–10.255.255.255
- Class B network numbers: 172.16.0.0–172.31.255.255
- Class C network numbers: 192.168.0.0–192.168.255.255
In an intranet that uses private addresses, a Check Point Security Gateway NAT gateway is put in place to connect the intranet to the Internet and translate the private addresses, to routable addresses. The default list of non-unique addresses are the three ranges specified in RFC 1918.
IPv6 Addresses
There are so many IPv6 public addresses that is not usually necessary to assign private IPv6 addresses for an internal network. There is a "Unique Unicast" IP range of fc00::/7 that can be used for private IPv6 addresses as specified in RFC4193.
Labels
- Labels:
-
Policy Installation
-
SmartConsole
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd like to add one more method
Method 6: Using Security Zones
(Ref: SmartConsole R80.10 Help)
Security Zones let you to create a strong Access Control Policy that controls the traffic between parts of the network.
A Security Zone object represents a part of the network (for example, the internal network or the external network). You assign a network interface of a Security Gateway to a Security Zone. You can then use the Security Zone objects in the Source and Destination columns of the Rule Base.
Use Security Zones to:
- Simplify the Policy. Apply the same rule to many Gateways.
- Add networks to Gateways interfaces without changing the Rule Base.
Workflow
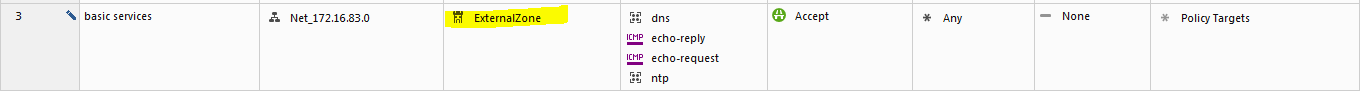
Define Security Zone objects. Or, use predefined security zones (ie. ExternalZone, InternalZone, DMZZone, WirelessZone)
- Assign Gateway interfaces to Security Zones
- Use the Security Zone objects in the Source and Destination of a rule. For example:
Source
Destination
VPN
Service
Action
InternalZone
ExternalZone
Any Traffic
Any
Accept
Below are screenshots from SmartConsole topology settings and an example of a policy
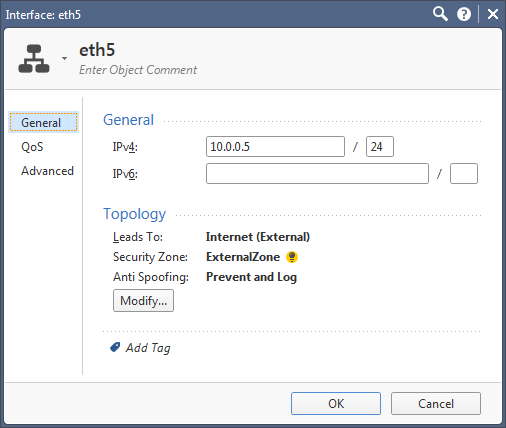
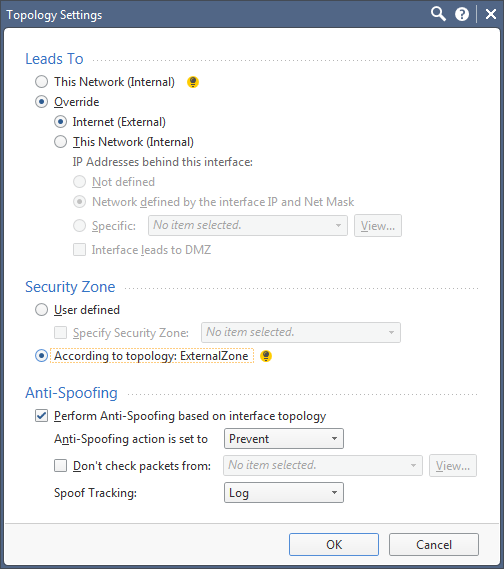
And can be defined in the rule base.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Method 7: Using Public IP Network Ranges
Create 6 network address ranges listed below, these should cover all the routable IPv4 public space:
1.0.0.0 - 9.255.255.255
11.0.0.0 - 126.255.255.255
128.0.0.0 - 169.253.255.255
169.255.0.0 - 172.15.255.255
172.32.0.0 - 192.167.255.255
192.169.0.0 - 223.255.255.255
Create a network group called Internet_IPv4 to include all of them.
Use Internet_IPv4 instead of any for internet rules.
The ranges that have been excluded are listed below in red:
10.0.0.0 - 10.255.255.255 Private-Use Networks
127.0.0.0 - 127.255.255.255 Loopback
169.254.0.0 - 169.254.255.255 Link Local
172.16.0.0 - 172.31.255.255 Private-Use Networks
192.168.0.0 - 192.168.255.255 Private-Use Networks
Note: There are several reserved IP subnets in the 192.0.0.0 and 198.0.0.0 address blocks that are included in the ranges above, to simplify the ranges a bit. I'm not too worried about including them. If the IPs are not forward-able the ISP will drop them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the IP layer perspective, you can define sensible ISP provided IPv4 Internet as a group wih exclusion network object:
INCLUDE:
All IPv4 prefix:
"All_Internet" predefined network range object (0.0.0.0 - 255.255.255.255)
EXCLUDE:
IPv4 private prefixes:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
IPv4 bogon prefixes:
0.0.0.0/8
100.64.0.0/10
127.0.0.0/8
169.254.0.0/16
192.0.0.0/24
192.0.2.0/24
192.88.99.0/24
198.18.0.0/15
198.51.100.0/24
203.0.113.0/24
240.0.0.0/4
IPv4 multicast prefix:
224.0.0.0/4
I find all other definitions to be confusing or too permissive. If you allow Internet access using such a network object, then looking through the cleanup DENY rule logs will give information about weird behavior of internal resources.
56 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
for me most of the time negating group is one of the most reliable ad easy way to define internet , I personally dislike group with exclusion for maaaany reason ![]() , by the way ther's a chance that we can use the defined internet (any exeternal and dmz ) in the firewall policy in the future?
, by the way ther's a chance that we can use the defined internet (any exeternal and dmz ) in the firewall policy in the future?
Nice post btw ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
These are the small things but can impact a lot.
Good Information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am just negating a group with all "private" ipv4 ranges.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is always how I've done it, as well!
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi guys, what are your thoughts about Check Point's out-of-the-box "Internet" object?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Tomer Sole
I just found this thread when searching for information about the All_Internet object.
What you are asking about is the App control object 'Internet', yes? I like it and would like to be able to use it for the access control policy instead of using the negate option like I am currently doing. Luckily this seems to be the least bad option from the list in the OP. Reading the answers here it seems many others would like to have the Internet object available for access control as well.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd like to add one more method
Method 6: Using Security Zones
(Ref: SmartConsole R80.10 Help)
Security Zones let you to create a strong Access Control Policy that controls the traffic between parts of the network.
A Security Zone object represents a part of the network (for example, the internal network or the external network). You assign a network interface of a Security Gateway to a Security Zone. You can then use the Security Zone objects in the Source and Destination columns of the Rule Base.
Use Security Zones to:
- Simplify the Policy. Apply the same rule to many Gateways.
- Add networks to Gateways interfaces without changing the Rule Base.
Workflow
Define Security Zone objects. Or, use predefined security zones (ie. ExternalZone, InternalZone, DMZZone, WirelessZone)
- Assign Gateway interfaces to Security Zones
- Use the Security Zone objects in the Source and Destination of a rule. For example:
Source
Destination
VPN
Service
Action
InternalZone
ExternalZone
Any Traffic
Any
Accept
Below are screenshots from SmartConsole topology settings and an example of a policy


And can be defined in the rule base.

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice Information. I think This applies to R80 only as lower than R80 version don't have zone concept.
This is good feature in R80
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also available in SMB appliances running R77.20.XX.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Security Zones are definitely helpful, and their use does not appear to impact SecureXL acceleration, templating, or the new Column-based/Early Drop rule matching based on my research so far.
--
My book "Max Power: Check Point Firewall Performance Optimization"
now available via http://maxpowerfirewalls.com.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately Check Point seems to have issues with Security Zones in R80.x.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Danny,
Is it really an issue if all you have to do is create a single rule with "External Zone" object and label it in a separate section "Do not delete, will cause policy installation failures!"?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Security zones cannot be used in NAT rules, so when you wan't to do a HIDE nat for all internet traffic, it is useless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I found an interesting bug(?) with this. When setting the zone "According to topology" in topology settings, policy validation fails with "Rule X has security zone objects that are not attached to any interface used in (gateway) : (zone).". Performing a "where used" on the zone object does not show the relevant gateway until I manually define the zone. For example, I selected "According to topology" which set my external interface to "ExternalZone". Validation failed until I manually forced it to "ExternalZone", and gateway didn't show up as "used" by the zone until then either. I am on R80.20 with JHFA Take 118.
I'm backing off of using Zones in my Policies for now. I am using the method with all of my networks in a group and then negating the cell. It works, but I feel it can be error prone in a larger environment. Topologies have to be correct for our various VPN's, so tagging a zone to this seems like it would scale better. I'll check back on this later when NAT is also supported like others seem to be doing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
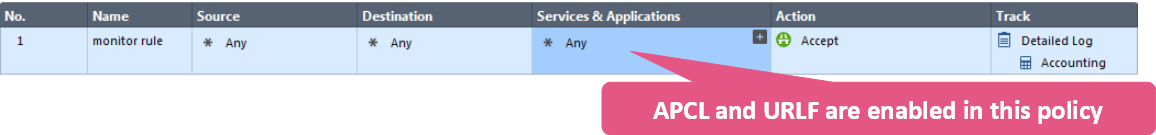
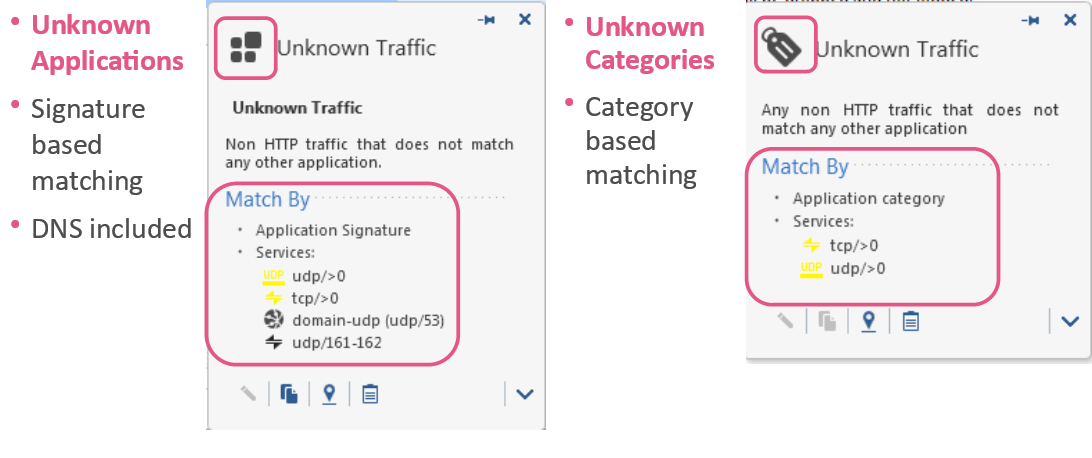
Addendum - Services & Applications
How To Describe "Any Application"
Matching unknown traffic

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Actually IPv6 makes it much simpler. 2000::/3 is a good starting point for Internet. If you want it more accurate you can exclude your local Public IPv6 range(s). Nothing much to it.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
According to Marc Lampo this is not working since R80.20 anymore.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To be precise : one cannot enter a route for 2000::/3, anymore.
I now have 32 ![]() routes, each a /8. (2000::/8, 2100::/8, 2200::/8, ... 3F00::/8)
routes, each a /8. (2000::/8, 2100::/8, 2200::/8, ... 3F00::/8)
Thanks R80.20 ;-(
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Method 7: Using Public IP Network Ranges
Create 6 network address ranges listed below, these should cover all the routable IPv4 public space:
1.0.0.0 - 9.255.255.255
11.0.0.0 - 126.255.255.255
128.0.0.0 - 169.253.255.255
169.255.0.0 - 172.15.255.255
172.32.0.0 - 192.167.255.255
192.169.0.0 - 223.255.255.255
Create a network group called Internet_IPv4 to include all of them.
Use Internet_IPv4 instead of any for internet rules.
The ranges that have been excluded are listed below in red:
10.0.0.0 - 10.255.255.255 Private-Use Networks
127.0.0.0 - 127.255.255.255 Loopback
169.254.0.0 - 169.254.255.255 Link Local
172.16.0.0 - 172.31.255.255 Private-Use Networks
192.168.0.0 - 192.168.255.255 Private-Use Networks
Note: There are several reserved IP subnets in the 192.0.0.0 and 198.0.0.0 address blocks that are included in the ranges above, to simplify the ranges a bit. I'm not too worried about including them. If the IPs are not forward-able the ISP will drop them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
At first glance this was my favorit way of defining Internet. But, when comparing adding 6 address ranges to a group vs. negating RFC1918 networks in a group the latter feels like the better choice from a performance perspective.
Considerations:
- 3 networks is less than 6 address ranges. But which one has the smaller performance impact?
- Does negating have any impact on performance?
- You cannot negate a src/dst cell in NAT rules.
- Negating doesn't feel as natural as allowing.
I'm currently sticking with the negated RFC1918. But if using address ranges can be proved not causing a large performance impact I'll consider using it just because it looks cleaner and is usable in NAT rules.
/ Ilmo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm surprised at all the ways you're trying to mask 'ANY'. Depending on your topology, infrastructure, security posture (layered defense), and active blades, most of these solutions are still effectively 'ANY'. Embrace it, accept it, secure it, and document it. BTW, I'm only talking about 'ANY' as a source or destination, when related to the Internet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm... "ANY" should be avoided whenever possible.
Please see this comment by Timothy Hall:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In most all cases, I agree the use of ANY is prohibited. In these "Internet" cases, I'll agree if you can show me the value of replacing ANY with a negated or excluded internal networks object. Or replacing ANY with all applicable IP ranges that represent the Internet. In most common topologies that have a dedicated "Internet" firewall, you would never see your internal networks as an Internet source or destination. You can mask ANY with some of these methods, and it can be debated that you've provided additional security by explicitly defining the Internet as a whole, but the effective outcome is still ANY. To me, the danger is in providing a false sense of security to those that don't fully understand this concept.
Personally, I accept ANY in these instances (related to Internet only), and ensure that there's a documented process to manage and mitigate the associated risk with using ANY. This includes, but isn't limited to, periodic reviews for continued use of ANY, requirements for additional security measures when using ANY, and management understanding and approval to use ANY.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If it would only affected security aspects of access control, I'd agree with you. The problem with "Any" is the impact on performance of the gateways, as per post referenced earlier as well as inclusion of RFC 1918 ranges in it.
I have seen too many environments with Anti-Spoofing disabled to be comfortable with it.
My personal preference is to use "All Internet" object available with URLF and Application Control blades or the "External" zone object.
If you do use "Any" extensively, I'd check the SecureXL status on the gateways to see how the acceleration is being affected. Your environment may very well perform nominally, if hardware specks are way higher than could've been otherwise.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
On other firewall brands I have used in the past, using "Any" was not affecting the performance. I know "Any" sounds bad, but there are things one want to be accessible from any IP, for example a web public server located in DMZ, behind the firewall. You want all the Internet IPs and private internal IPs to reach that Web server.
Another example is cloud services that cannot be properly handled by a DNS rule, due to the fact that the IPs change all the time and when the firewall checks, the IP is already different.
Even the Stealth and Cleanup rule has "Any" in it. As bad as it sounds "Any" might be a necessary evil.
For performance reasons I try to avoid "Any" and I was able to replace it with Internet_IPv4 when I have no choice like inbound traffic to a public web server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are concerned about cleaning up as many *ANY* rules as possible, you could have a group containing all your private address space (or all RFC-1918 LANS) and negate that group for rules granting inbound access from the Public Internet.
R80 CCSA / CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As mentioned earlier in this thread, from a functional perspective using "Any" in your policies works fine. However avoiding "Any" helps optimize the new Column-based matching function which is described here:
Unified Policy Column-based Rule Matching
This feature causes much more efficient matching of policy rules in the PXL/F2F paths. It is not part of SecureXL and using various SecureXL commands like "fwaccel stat" will not show the potential impact of using "Any" in your policies. As mentioned in my book the "throwing out" of rules by Column-based matching that cannot possibly match the connection happens for the Destination column first, so trying to avoid use of "Any" in that one column can be the most beneficial, because if almost all rules can be "thrown out" during the first pass through the Destination column there are very few rules left when going through the Source and Service columns. Once all non-matching rules have been thrown out, a traditional "top-down, first-fit" evaluation of the surviving rules commences.
There do not appear to be any commands that allow you to measure how efficiently Column-based matching is operating on the firewall, other than a full-blown kernel debug of the policy evaluation.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the reminder about column-based matching!
The only caveat is that it has to be an R80.X environment and I cannot deduce that it is from Shannon's posts.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is confusing. So, for allowing your internal network out to the Internet, what is the best method to only specify the Internet and nothing extra.
Thanks
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 7 | |
| 7 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


