- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: R80.30 - ClusterXL CCP Encryption!
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
R80.30 - ClusterXL CCP Encryption!
Under R80.30 it is possible to encrypt CCP traffic. This is very useful to protect the cluster from manipulated CCP packets. Therefore new commands have been implemented on the CLI for this purpose. The following description shows you how to enable CCP encryption. All settings you make on the CLI are permanently stored in the following file “/etc/fw.boot/ha_boot.conf”. This means that all settings are preserved after the reboot. You have to set the settings on both gateways and they will take effect on the fly. The CCP encryption is disabled by default and must be enabled via CLI on both gateways.

The CCP Encryption:
- Supports SHA-256 hash.
- Key replacement is done on every policy installation
- Encryption & decryption is done by CPU using AES-GCM to achieve minimal effect on performance.
Example commands:
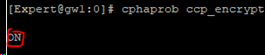
# cphaprob ccp_encrypt
clish> show cluster members ccpenc
With the following command the encryption can be permanently enabled on the fly:
# cphaconf ccp_encrypt on
In this way the encryption can be disabled on the fly
# cphaconf ccp_encrypt off
With this command you can test if the CCP encryption works. Here you should not see any cluster status information on the sync interface (blue). All packages should be visible under unknown when CCP encryption is enabled.
# tcpdump -nepi eth1 -x port -s 0 8116 2>/dev/null | ccp_analyzer -g –c
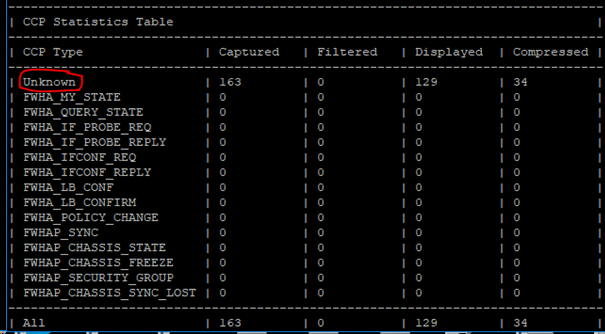
Unfortunately it is no longer possible to analyze the CCP packets via "ccp_analyzer " when encryption is enabled.
The CLISH commands:
- Toggle encryption mode: “set cluster member ccpenc <on/off>”
- Show encryption mode: “show cluster members ccpenc”
The commands under expert mode:
- Toggle encryption mode: "cphaconf ccp_encrypt <on/off>"
- Show encryption mode: "cphaprob ccp_encrypt"
- Display encryption key: "cphaprob ccp_encrypt_key
More interesting articles: cp.ankenbrand24.de
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Intel‘s AES New Instructions AES-NI is a encryption instruction set that improves on the Advanced Encryption Standard (AES) algorithm and accelerates the encryption of data in many processor familys.
Comprised of seven new instructions, AES-NI gives your environment faster, more affordable data protection and greater security.
You found more informations about AES NI here:
https://community.checkpoint.com/docs/DOC-3278-r80x-performance-tuning-tip-aes-ni
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
17 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is this already available with R80.20?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To further clarify, CCP encryption is enabled by default on R80.30 Gaia kernel version 3.10 only. CCP encryption is disabled by default on R80.30 Gaia kernel version 2.6.18. See sk162358: R80.30 cluster, with CCP Encryption enabled, managed by an R80.10 Security Management come... Just noticed this difference in my lab and could not figure out what was going on until I found that SK.
Also tagging @PhoneBoy with this follow-up question: If CCP encryption is enabled it impacts both CCP traffic emanating out all clustered interfaces presenting a Cluster IP, and the CCP traffic on the sync interface, correct? Is there any way to disable CCP encryption just for the state sync traffic (FWHAP_SYNC) yet leave it enabled for all the clustered interfaces presenting a Cluster IP? My guess is no, but if one has a crossover cable connecting the sync ports in a 2-member cluster, it would be nice to save the overhead involved encrypting/decrypting that heavy sync traffic if the sync network is known to be secure. Securing CCP on the cluster interfaces is still very important of course since they are accessible to the surrounding networks.
Yes I suppose someone could vampire into the sync cable and mess with the cluster if the sync network CCP traffic is not encrypted, but if the attacker already has physical access to your cluster and the sync cable you've got much bigger problems afoot...
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nice
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
Thank you, that share this information with CheckMates. Did you mean "R80.30 - ClusterXL CCP Encryption!", right? ![]()
Regards,
Dmitry.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dmitry,
Thanks, I made a mistake. That must be named ClusterXL:-)
Regards
Heiko
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very nice feature. I have all cluster encrypted:-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it possible to use certificates to protect ccp sessions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't know that.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko,
I would to provide more information about the CCP encryption, could you update your article according to it.
The CCP Encryption:
- Supports SHA-256 encryption.
- Key replacement is done on every policy installation
- Encryption & decryption is done by CPU using AES-GCM to achieve minimal effect on performance.
You don't need to set key manually, it will be generated automatically and we recommend to use only this mode, at least because every policy installation will be generated new key (this option doesn't work if a key was set manually). The key can be set manually only as option for troubleshooting.
The CLISH commands:
- Toggle encryption mode: “set cluster member ccpenc <on/off>”
- Show encryption mode: “show cluster members ccpenc”
The commands under expert mode:
- Toggle encryption mode: "cphaconf ccp_encrypt <on/off>"
- Show encryption mode: "cphaprob ccp_encrypt"
- Display encryption key: "cphaprob ccp_encrypt_key"
Regards,
Dmitry.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Aviel,
No, it isn't possible. In my opinion, we don't have a reason to use certificates here.
Regards,
Dmitry.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What kind of performance impact are we talking about when enabling CCP encryption ?
It says: "minimal effect on performance"
But are there numbers available ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The encryption/decryption is most likely using AES-NI instructions built into recent Intel processors.
On systems that don't have AES-NI instructions, I imagine the performance impact will be a bit more noticeable.
As for exact numbers, I don't think we can comment until after GA.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Intel‘s AES New Instructions AES-NI is a encryption instruction set that improves on the Advanced Encryption Standard (AES) algorithm and accelerates the encryption of data in many processor familys.
Comprised of seven new instructions, AES-NI gives your environment faster, more affordable data protection and greater security.
You found more informations about AES NI here:
https://community.checkpoint.com/docs/DOC-3278-r80x-performance-tuning-tip-aes-ni
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can I change the encrytion algorithm.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We use now the encryption. It works fine.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unfortunately, it is no longer possible to analyze the CCP packets via "ccp_analyzer " when encryption is enabled.
Is there any other way to analyze CCP packets, or do I need to simply disable encryption when debugging clusterxl?
BR Jernej
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 27 | |
| 18 | |
| 10 | |
| 9 | |
| 7 | |
| 7 | |
| 6 | |
| 6 | |
| 5 | |
| 4 |
Upcoming Events
Mon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANMon 23 Feb 2026 @ 11:00 AM (EST)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - AMERTue 24 Feb 2026 @ 10:00 AM (CET)
Latest updates on Quantum Spark including R82 features and Spark Management zero touch - EMEATue 24 Feb 2026 @ 11:00 AM (EST)
Under The Hood: CloudGuard Network Security for Azure Virtual WANThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Introducing Cyata, Securing the Agentic AI EraFri 06 Mar 2026 @ 08:00 AM (COT)
Check Point R82 Hands‑On Bootcamp – Comunidad DOJO PanamáAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


