- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Who rated this post
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R80.30 - ClusterXL CCP Encryption!
Under R80.30 it is possible to encrypt CCP traffic. This is very useful to protect the cluster from manipulated CCP packets. Therefore new commands have been implemented on the CLI for this purpose. The following description shows you how to enable CCP encryption. All settings you make on the CLI are permanently stored in the following file “/etc/fw.boot/ha_boot.conf”. This means that all settings are preserved after the reboot. You have to set the settings on both gateways and they will take effect on the fly. The CCP encryption is disabled by default and must be enabled via CLI on both gateways.

The CCP Encryption:
- Supports SHA-256 hash.
- Key replacement is done on every policy installation
- Encryption & decryption is done by CPU using AES-GCM to achieve minimal effect on performance.
Example commands:
# cphaprob ccp_encrypt
clish> show cluster members ccpenc
With the following command the encryption can be permanently enabled on the fly:
# cphaconf ccp_encrypt on
In this way the encryption can be disabled on the fly
# cphaconf ccp_encrypt off
With this command you can test if the CCP encryption works. Here you should not see any cluster status information on the sync interface (blue). All packages should be visible under unknown when CCP encryption is enabled.
# tcpdump -nepi eth1 -x port -s 0 8116 2>/dev/null | ccp_analyzer -g –c
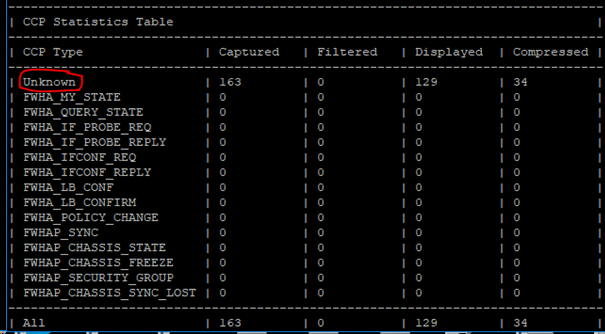
Unfortunately it is no longer possible to analyze the CCP packets via "ccp_analyzer " when encryption is enabled.
The CLISH commands:
- Toggle encryption mode: “set cluster member ccpenc <on/off>”
- Show encryption mode: “show cluster members ccpenc”
The commands under expert mode:
- Toggle encryption mode: "cphaconf ccp_encrypt <on/off>"
- Show encryption mode: "cphaprob ccp_encrypt"
- Display encryption key: "cphaprob ccp_encrypt_key
More interesting articles: cp.ankenbrand24.de
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


