- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Most URLs categorized as X-VPN this morning
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Most URLs categorized as X-VPN this morning
Hi,
we encountered a big issue this morning as nearly all URLs were categorized as X-VPN application which is blocked in our rulebase because of the category (Anonymizer) and it's also set to critial risk.
Did you encounter the same and is there any official statement? It's obviously an issue with the database and the first time we see such an issue.
4 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
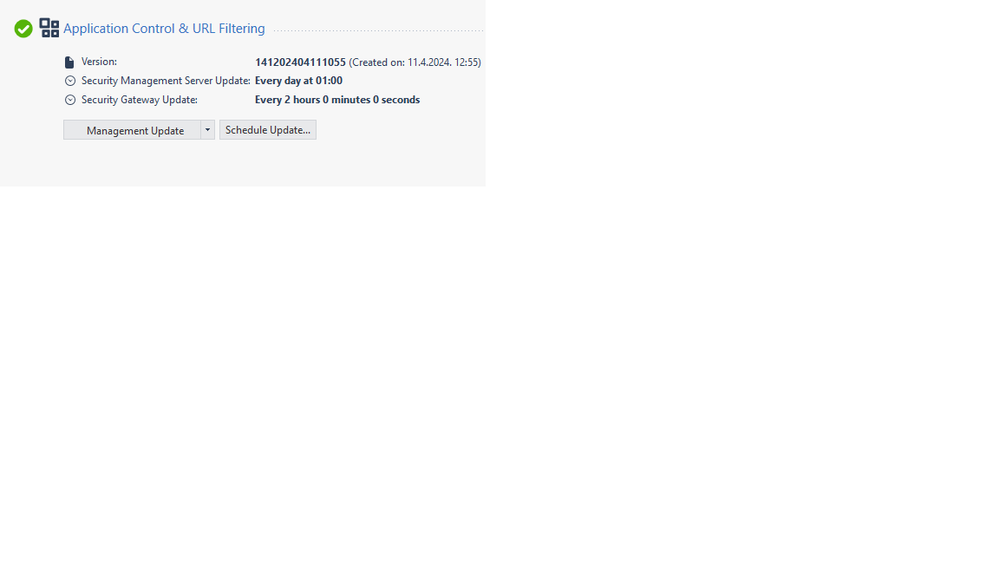
I can confirm that indeed from the last ~15 minutes this issue has been resolved, using the APPI package 11042401.
Gateways will be updating according to their scheduled update policy.
If you need to rush the update, please do the following on the security gateways:
- # rm $FWDIR/appi/update/Version
- # rm $FWDIR/appi/update/next_update
- Wait for 5 minutes.
A new dedicated sk182202 is now available for this issue.
An official and detailed RCA will follow.
Ofir Israel
VP, Threat Prevention Check Point Software Technologies
P.S. We are aware that the fix seems to have not worked for a limited amount of our customers. We currently suspect this as a logging behavior where old connections have new sessions and are updated on the log view. If you encounter drops please let us know through a TAC ticket, we are monitoring the situation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I noticed something that may help others as well.
Yesterday once the issue has been resolved and the new package released, I performed the Update of the Application Control & URL Filtering via SmartConsole. This resolved the issue on 2 out of 3 clusters. The 3rd cluster, although it had the same updated package version(110424_1) as the other gateways, was still dropping traffic.
So I performed the steps mentioned in https://support.checkpoint.com/results/sk/sk182202 and suddenly it worked. The package version was still the same but apparently there was a difference between updating via Mgmt and manually deleting the files.
Hope this helps anyone else
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All gateways had the new file yet we still had to create the manual whitelist for X-VPN.
I then completed the SK article on ALL gateways (even ones not using the application blade) and only then did we stop seeing logs.
I will monitor to see if anymore appear but the trick is going through the SK regardless of the file date.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, let me introduce some more information.
As I wrote last week even after releasing the package we encountered cases of customers still seeing the issue. We later saw evidence on incorrect MD5 and that's why we added that section to the SK182202.
We did not tweak the signatures in the package therefore no new package was issued but we did perform manual operations to speed up the integration & deployment of package 110424_1 into the updates system, so that our customers get it faster than usual - this caused some issues with wrong MD5 for small portion of customers.
Therefore the recommendation is for anyone who still has issues with X-VPN classification to check the MD5 and if necessary force re-download of the package.
Ofir Israel
VP, Threat Prevention
Check Point
69 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
We have the same issue. We had this the other day and just now again on one site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi,
we have the same issue since today.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
same issue here. It started around 04:12 AM CEST.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
We have the exact same issue! Nothing is passing by as every web request is categorized as X-VPN and therefore blocked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have this from this morning,is there a reason why or we have to raise a TAC ticket?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, we have the same issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same here. Any comments from Check Point?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just raised
Case
6-0003912005
so we will see if they come up with an idea ,other that remove anonymizer category from rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
we have the same problem. We registered an ticket bye Check Point Support. At the moment no reaction. On the status Checkpoint website https://status.checkpoint.com/ there are all services OK.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
We are aware of the miscategorization by Application Control / URL Filtering blade, where legitimate traffic is categorized as X-VPN and being dropped accordingly. Right now, a joint Task force that includes both R&D and TAC experts are working together to mitigate the issue.
We will keep you posted
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you Val,
hope you will sort it out
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will update this post once we have a definitive fix.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your quick response!
Is it possible that you provide a status update in this thread as soon as you get the news that the issue has been resolved? That would would be amazing.
Appreciate you and best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm experiencing the same issue since this mornig.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @_Val_.
This issue has caused disruption, and it raises a question about communication. While we understand technical problems occur, many partners rely on prompt notifications from Check Point to address such situations effectively.
I'd like to inquire why there wasn't a more immediate communication effort to partners regarding this miscategorization issue. Timely updates would have significantly aided troubleshooting and minimized disruption for many organizations. Are there plans to improve communication protocols for future occurrences?
In addition to the previous questions, I'm also interested in:
- Any recommended workarounds or mitigation strategies in the meantime.
- Whether there's an estimated timeframe for a resolution.
Thank you for your time and any information you can share.
Sincerely,
Nenad Vijatov
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please can we have an update and ETA on the issue this is causing significant disruption for our staff and CP are being frustratingly quiet. the website reports there will be an update every 30 minutes but I do not see any posts regarding this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same here... We have spent an hour thinking that our PCs were infected and trying to find what happened.
This seems to only be happening on Harmony Connect?
Update: nvm, it's happening on all gateways.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It seems the issue is occurring for users that are using Full SSL Inspection.
We have a case open to TAC since yesterday but no updates yet.
I noticed X-VPN signature was updated on 8-Apr (Mon) in APPI package No. 070424_1.
If this is the case, then I hope a new package is released soon 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is not the case. We do not use full ssl inspect and are still impacted.
Question to Check Point, when can we expect an official statement?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for sharing.
It's strange because we have many customers but don't experience this issue with only HTTPS categorization... Note we do have Anonymizers to be blocked in the policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not so weird at all. The detection is based on a perceived header. Without HTTPS inspection you will not be able to look into that traffic to match this.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not 100% what you mean by this but we have multiple environments impacted that are not decrypting one bit of SSL. In other words, SSL inspection is not a pre-requisite to experience this issue.
HTTPS categorization is enabled.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks all for the insight 🙂
I was just wondering because that we have more than hundreds of customers, but only 3-4 reports from the field experiencing this issue, and it was just that all of those 3-4 customers had Full SSLINS enabled.
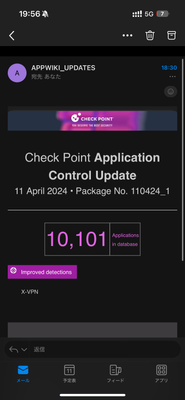
Btw, I just noticed there was a APPI package update No.110424_1 with just "X-VPN" updated.
Maybe the issue was addressed?🤔
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
if you meant this one it does not help still traffic is x-vpn categorized
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Where do you see that "X-VPN" was updated?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I recieved a mail from APPWIKI_UPDATES just around an hour ago. I haven't checked on MGMT yet... probably the package is still not distributed to the update servers?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems a bit more complicated than that. Incoming traffic to our own website's webservers with HTTPS-inspection and IPS also gets frequently blocked as X-VPN, but not all, even when the same URL's are requested. Not every browser triggers this protection, but mostly Chrome and MS Edge do.
Not all users are impacted by the issue, or many hours after others were inpacted by the issue. Hopefully it is NOT something that get's distributed to pc's with (cloud) shared/synchronized browser profiles, such as google and microsoft stored browser profiles.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same problem here, seeing this since April 8 4pm CEST
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Stefan, Did you open a service request yet? As you seem to be seeing this 2 to 3 days before most other see it.
And this is the sort of additional insight that might help finding a root cause.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter