- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
The Great Exposure Reset
24 February 2026 @ 5pm CET / 11am EST
CheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: INFO - https sites not working, zdebug errors ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
INFO - https sites not working, zdebug errors PSL Drop: MUX_PASSIVE and PSL Drop: TLS_PARSER
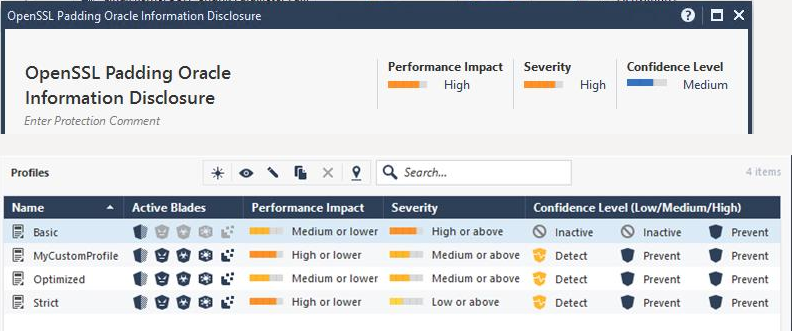
zdebug drop shows errors PSL Drop: MUX_PASSIVE and PSL Drop: TLS_PARSER and https sites were not working on several environments due to IPS protection "openssl padding oracle information disclosure" that was updated on 7/8/2020.
Disabling this protection resolves the issue.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS update has been replaced. It is now safe to update.
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
"zdebug" is a macros that only sends debug flags to fw module, if used without additional efforts, as "fw ctl zdebug drop". In R80.x fw module does not do much. You need to debug KISS and UP.
It is better to involve TAC in your case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this - got several customers affected by this. Can confirm that disabling the protection restores internet access.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please raise TAC case for this, thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Have engaged TAC - but also received the following update from my CP SE:
The problematic updates are:
634204548 or 635204548
The impact:
- After IPS update, many drops observed (via fw ctl zdebug + drop on CLI)
dropped by fwmultik_process_f2p_cookie_inner Reason: PSL Drop: TLS_PARSER
- The following may be seen in /var/log/messages:
kernel: [fw4_4];ips_gen_dyn_log: malware_policy_global_send_log() failed
- High CPU utilization and traffic impact
Short term remediation:
1. Re-enable IPS on the gateway object if it was disabled as a workaround.
2. Ensure that updates are not set to automatic gateway updates. (See sk120255 for more info)
a. Open Gateway Object in SmartConsole
b. Go to IPS tab (blade must be enabled)
c. Under "IPS Update Policy" select "Use IPS management updates"
3. Revert to previous good IPS database update
a. Under the "Security Policies" tab, select Threat Prevention or IPS policy
b. Under "Threat Tools" (left hand side) select "Updates"
c. Click the arrow next to "Update Now" and select "Switch to version..."
d. Select a previous version that is not 634204548 or 635204548 and click "Switch" (note it may take some time for the previous versions to populate if there are many previous versions. Look at the top right of the dialogue box where it says "# items")
e. Update will be pushed to gateways
f. Clear any scheduled updates from the "scheduled updates" option
4. Turn on IPS on the gateway if "IPS off" command was used to disable IPS via the CLI and test traffic.
Best practices for updates and IPS implementation:
This document (while it is specified for R80.10, it is still relevant for newer versions) contains our best practices recommendations about IPS profile implementation, and update best practices. https://sc1.checkpoint.com/documents/Best_Practices/IPS_Best_Practices/CP_R80.10_IPS_Best_Practices/...
Alternately, disabling TLS parsing for IPS is a secondary workaround. However, this degrades IPS protections and is therefore not the recommended path at this time. Nonetheless, if customers are experiencing severe issues, they can use this command on the gateway:
fw ctl set int tls_parser_enable 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We were facing this issue at a customers installation today as well.
After opening sr we got update, that IPS versions 634204548 or 635204548 are affected. We reverted to 635204525 and the issue persisted.
As we did not want to try and error we now have disabled this protection and now the issue is gone for now.
Now we're waiting for the next update (and reply from sr owner)
and now to something completely different - CCVS, CCAS, CCTE, CCCS, CCSM elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, we are aware of the issue and are working to provide a fix for it.
Meanwhile, if you are affected, please use the following steps for short term remediation:
1. Re-enable IPS on the gateway object if it was disabled as a workaround.
2. Ensure that updates are not set to automatic gateway updates. (See sk120255 for more info)
a. Open Gateway Object in SmartConsole
b. Go to IPS tab (blade must be enabled)
c. Under "IPS Update Policy" select "Use IPS management updates"
3. Revert to previous good IPS database update
a. Under the "Security Policies" tab, select Threat Prevention or IPS policy
b. Under "Threat Tools" (left hand side) select "Updates"
c. Click the arrow next to "Update Now" and select "Switch to version..."
d. Select a previous version that is not 634204548 or 635204548 and click "Switch" (note it may take some time for the previous versions to populate if there are many previous versions. Look at the top right of the dialogue box where it says "# items")
e. Update will be pushed to gateways
f. Clear any scheduled updates from the "scheduled updates" option
4. Turn on IPS on the gateway if "IPS off" command was used to disable IPS via the CLI and test traffic.
Alternately, disabling TLS parsing for IPS is a secondary workaround. However, this degrades IPS protections and is therefore not the recommended path at this time. Nonetheless, if customers are experiencing severe issues, they can use this command on the gateway:
fw ctl set int tls_parser_enable 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
🤐
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am also facing the same issue after active the OpenSSL Padding Oracle Information Disclosure (CVE-2016-210).
After disabling this protection resolves the issue.
Regards,
R.B
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS update has been replaced. It is now safe to update.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello
First question: in which package is the IPS protection CPAI-2016-0349 updated and fixed?
Second question: why is not an official advisory regarding this issue? Impact has been huge
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anyone having this update propagate?
I'm mashing update and still 635204548.
CCSME, CCTE, CCME, CCVS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just FYI
Due to the high performance impact this will affect customers with a "strict" or custom IPS profile only:
Oddly enough my colleague's lab system has this very protection as "low confidence"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yeah, that was a nasty one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check Point has finally released sk167939 which describes the issue and solution.
It also outlines that Check Point will improve their QA testing.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: AI-Generated Malware - From Experimentation to Operational RealityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026About CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter