- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Monitoring VPN tunnels
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Monitoring VPN tunnels
Hey guys,
I know there were few posts about this before, but here is what Im looking for. I know many methods you can check the status of the tunnel itself, with tcpdump on proto 50, vpn tu options, sv monitor etc, but those are all manual methods. What Im after is automatic method that would alert a customer if there is an issue with the tunnel.
I get the options inside the community under tunnel management you can set to tunnel down and up for different actions, but I wonder if there is anything more intuitive (for the lack of better term) that can be set up.
Thanks as always for any suggestions.
Best,
Andy
Best,
Andy
Andy
2 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey guys,
Just to give a quick update on this. Talked to Tier 3 guy in DTAC and what I was informed is quite disappointing, to put it bluntly. So, he told me that when it comes to VPN monitoring, supposedly, it ONLY works if its CP to CP tunnel, so say if you have cp to 3rd party, which probably 99% of customers would have, you cant even configure pop-up alert to work and here comes really odd part for me. Say even if you have cp cluster to another single gateway VPN tunnel, its not enough to even reset the tunnel via vpn tu tlist del or vpn tu command, but you would need to do cpstop on BOTH cluster members.
O well, as disappointing as this is, if thats how it is, we just have to accept it. I still, personally, find it bit hard to believe that even pop-up alert is only possible if its strictly CP vpn tunnel.
Anyway, figured would share the info I was given. At least searching for log filter by "Key Install" would give log when tunnel may have went down, so its better than nothing. I sure hope VPN monitoring is totally revamped in R82...
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are the sk sk63663 you can simply use any NMS or I am using open source like check_mk and it perfectly
shows the tunnel status and if any issue occurs
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
53 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy
I think I mentioned it before, in R82 we have a completely new VPN Monitoring Tool:
- Introducing the Advanced VPN Monitoring tool that shows information on each VPN Tunnel and tracks its health and performance.
Perhaps @itamarav can ass additional details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Tal_Paz-Fridman , but in the meantime, since who knows how long it might be before most clients are on R82, does anything similar exist in R81.20?
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Within R82, will it be possible to send SNMP traps to more than 1 trap server in case VPN state is changed?
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't know of any ways to alert automatically from the firewall. We use an external monitoring server to monitor endpoints on the other end of the VPN and get our automatic notifications (e-mail / sms) that way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I will do some testing in the lab tomorrow to see if I can make it work with pop up alert when tunnel is reset.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Andy,
Let me answer your question with a question. When should Check Point consider a VPN tunnel problematic?
Some tunnels are used more then others. There are tunnels that are maybe used once a day. If no traffic flows via the tunnel the tunnel goes down.
I think the best would be , for now using a monitoring tool and ping something via the tunnel on the other side. In this way you know that the tunnel is up and there is no issue. Until they restart something at the other end of course 🙂
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me answer your question. When should CP consider tunnel problematic? I would say when it goes down 🙂
See, what we are trying to accomplish is to get some sort of pop up alert or a log when tunnel is down.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good morning,
I´d expect something like "active tunnel". so Tunnel UP is one thing. Checking if there is traffic (i.e. Keepalives - so even when tunnel is not in use actively) is a better bet. So - something like
- "tunnel up and traffic flowing = tunnel good"
- "tunnel up and no traffic (uni/bidirectional?) = tunnel problematic"
- "tunnel up and traffic = tunnel fine"
Personally, I´d stick to an external monitoring, using either snmp or by checking if resources on "the other side" are available.
(might be an idea to extend GAiA API to see local tunnel sessions (Site to Site and/or Client to Site) and if there are sessions and if there is activity on tunnel? )
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the way 🙂 Don't trust the firewall to give you the state. Use tests on the actual services on the other end.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree 🙂
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
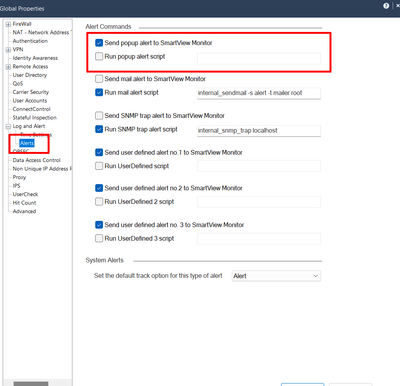
In case you are using permanent tunnels (suggesting to do so), within VPN community, set the tracking to desired option. If you choose any of available Alerts, then go to the Global Properties on Domain where VPN is configured, go to the Log and Alert -> Alerts and add proper alert scripts.
In case you are using regular tunnels (suggesting to switch to Permanent), then go to the Global Properties -> Log and Alert -> select desired option for "VPN configuration & key exchange errors". If you choose any of available Alerts, then go to the Global Properties on Domain where VPN is configured, go to the Log and Alert -> Alerts and add proper alert scripts.
Another option is to create script using VPN SNMP OID (for example .1.3.6.1.4.1.2620.500.9002.1.3)
Some other ideas for scripting:
- output from "vpn tu"
- monitor VPN logs (traffic and/or .elg files)
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @JozkoMrkvicka . I actually let TAC guy know what I had tried in the lab...so, say if I change tunnel monitoring option to log inside vpn community, then I do see the log with blade:"VPN" filter indicating key exchange, which matches with when I do tunnel reset, perfect. Now...IF I set the option to pop up alert and set rule that way, it does NOT work. I have a feeling Im missing something in global properties, but not sure which option.
Thoughts?
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am pretty sure this is it, but since support site is down atm, cant look up the sk for it. If anyone has any idea what this should be, happy to try 🙂
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I never tried that "pop up" option. To be honest, I am not sure what is the goal of that one...
I used snmp trap alert script and mail alert script, which are working perfectly fine.
There is only 1 issue with snmp or mail script - you can specify only 1 IP (only 1 SNMP trap reciever / only 1 smtp mail relay IP).
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@JozkoMrkvicka If you would be kind enough mate to provide the steps to make it work with snmp script, I would be very grateful, while I wait for TAC response.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Very important note is that the SNMP traps are NOT sent from the gateway.
SNMP trap alerts are sent from management Main IP (Leading Interface IP) or Logserver Main IP.
Steps:
-
Connect with SmartDashboard to Security Management Server / Provider-1 CMA / Domain Management Server.
-
Go to the Policy menu - click on the Global Properties...
-
Expand the Log and Alerts - click on the Alerts pane.
-
In the Run SNMP trap alert script field, enter/paste the following:
internal_snmp_trap -c YOUR_SNMP_COMMUNITY IP_ADDRESS_OF_YOUR_SNMP_TRAP_SINKNote: By default,
YOUR_SNMP_COMMUNITY=public.
For example:
internal_snmp_trap -c public 1.1.1.1
"public" is snmp community string
1.1.1.1 is snmp trap reciever IP.
Kind regards,
Jozko Mrkvicka
Jozko Mrkvicka
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you. Let me see if TAC guy can make it work with pop up alert, that would probably be best option in this case.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just to update quick...TAC came back saying they got it working with pop up alert, so I will update once I do remote sessionto see if we can get it working in my lab as well.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just in case, AFAIK, only permanent tunnels can be SNMP monitored.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe thats the case, yes.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey guys,
Just to give a quick update on this. Talked to Tier 3 guy in DTAC and what I was informed is quite disappointing, to put it bluntly. So, he told me that when it comes to VPN monitoring, supposedly, it ONLY works if its CP to CP tunnel, so say if you have cp to 3rd party, which probably 99% of customers would have, you cant even configure pop-up alert to work and here comes really odd part for me. Say even if you have cp cluster to another single gateway VPN tunnel, its not enough to even reset the tunnel via vpn tu tlist del or vpn tu command, but you would need to do cpstop on BOTH cluster members.
O well, as disappointing as this is, if thats how it is, we just have to accept it. I still, personally, find it bit hard to believe that even pop-up alert is only possible if its strictly CP vpn tunnel.
Anyway, figured would share the info I was given. At least searching for log filter by "Key Install" would give log when tunnel may have went down, so its better than nothing. I sure hope VPN monitoring is totally revamped in R82...
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
nah - Did you try monitoring through SNMP? I am monitoring my tunnels through SNMP and with particular OIDs it does given you status about P1 or P2 failures
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not yet, but though I did mention it to TAC, it was not tested. I will try in the lab what @JozkoMrkvicka provided, unless you have something more simple, happy to try 🙂
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are the sk sk63663 you can simply use any NMS or I am using open source like check_mk and it perfectly
shows the tunnel status and if any issue occurs
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Forgot to mention - Let me know if any help is required setting check_mk and I am happy to help.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks brother.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks! So are you saying you can put that snmp oid into the tool check_mk and it shows the status? If so, thats super easy, will try it Tuesday.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well you don't even need to add those OIDs or any other OIDs
- Just Install check_mk
- enable SNMP on firewalls
- Add host in check_mk and it automatically detect the Tunnels since it has those scripts enabled.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter