- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Policy Insights and Policy Auditor in Action
19 November @ 5pm CET / 11am ET
Access Control and Threat Prevention Best Practices
Watch HereOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: How to manually delete an entry from the Conne...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How to manually delete an entry from the Connections Table
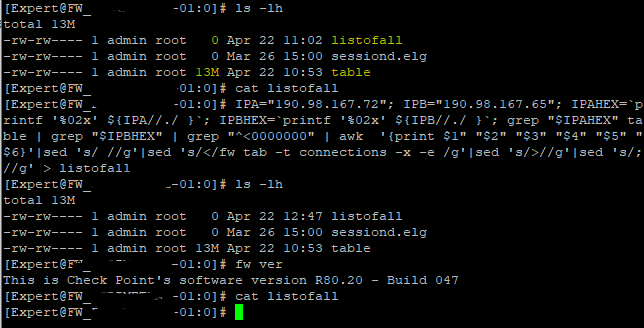
Not that you really need to use this often but it has saved my day once or twice a year. Great SK103876 is available but in a stressful situation calculating HEX numbers is the last thing you want to do and then compiling a complex command out of it is even more challenging
This one-liner actually gives you an opportunity to generate all fw tab kill commands in one file for a pair of given IP addresses. Tested on R80.10 GW but I'm fairly confident it would work in R77.
IPA="x.x.x.x"; IPB="y.y.y.y"; IPAHEX=`printf '%02x' ${IPA//./ }`; IPBHEX=`printf '%02x' ${IPB//./ }`; grep "$IPAHEX" table | grep "$IPBHEX" | grep "^<0000000" | awk '{print $1" "$2" "$3" "$4" "$5" "$6}'|sed 's/ //g'|sed 's/</fw tab -t connections -x -e /g'|sed 's/>//g'|sed 's/;//g' > listofall
You will need to dump all your current connections into a file called table first of course. You may add this to front of the above to make it true one-liner.. But I found it easier to do this in two steps as you have more control
fw tab -t connections -u > table
And result is in file called listofall. Then you just execute those commands by copy-paste for example or chmod the file itself and run it.
Here's an example
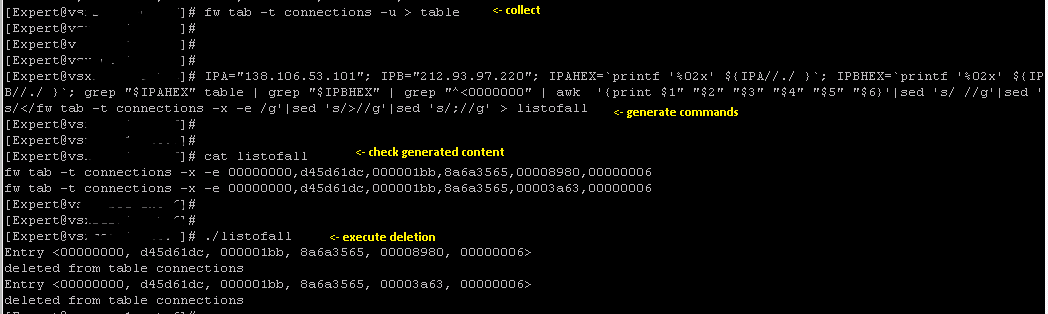
And of course, you can add port numbers if needed
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still gold (works on R81.10.15 as well)
24 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Bravo!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you very much for sharing this information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Modified it a bit, it's still ugly but we don't have to do anything now, apart from providing the values for IPA & IPB
#!/bin/bash
#Dump latest copy of connection table
fw tab -t connections -u > table
#Read input for IPA & IPB values
read -p "IPA: " IPAI
read -p "IPB: " IPBI
#The Decimal to Hex conversion takes place and generates the command file
IPA=${IPAI}; IPB=${IPBI}; IPAHEX=`printf '%02x' ${IPA//./ }`; IPBHEX=`printf '%02x' ${IPB//./ }`; grep "$IPAHEX" table | grep "$IPBHEX" | grep "^<0000000" | awk '{print $1" "$2" "$3" "$4" "$5" "$6}'|sed 's/ //g'|sed 's/</fw tab -t connections -x -e /g'|sed 's/>//g'|sed 's/;//g' > listofall
#Execute commands generated in the file
/bin/bash listofall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Going through my bit buckets of useful Check Point stuff, here's a version I wrote that validates the input and asks before deleting.
#!/bin/bash
#
# Check Point Firewall Connection Killer
#
# Version 0.02
#
# Changelog
# v0.01
# First release
# v0.02
# Added valid_ip
#
#
# Based on the post at https://community.checkpoint.com/t5/Enterprise-Appliances-and-Gaia/How-to-manually-delete-an-entry-from-the-Connections-Table/td-p/13122
#
# It's crude and uses temporary files instead of stored arrays, could do with a fair bit of improvement BUT IT WORKS.
#
# Limited to IP's for now... conn table format at https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk65133
# for whoever wants to nail it down to ports.
#
# Credits: Kaspars_Zibarts https://community.checkpoint.com/t5/user/viewprofilepage/user-id/11456
# MKIT_NMG https://community.checkpoint.com/t5/user/viewprofilepage/user-id/4907
# Mitch Frazier for valid_ip https://www.linuxjournal.com/content/validating-ip-address-bash-script
echo "Check Point Firewall Connection Killer"
# fns
display_usage() {
echo -e "\nPlease ensure you are in the correct VS"
echo -e "\nUsage:\ncpfck IP1 IP2\n"
}
valid_ip()
{
local ip=$1
local stat=1
if [[ $ip =~ ^[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}\.[0-9]{1,3}$ ]]; then
OIFS=$IFS
IFS='.'
ip=($ip)
IFS=$OIFS
[[ ${ip[0]} -le 255 && ${ip[1]} -le 255 \
&& ${ip[2]} -le 255 && ${ip[3]} -le 255 ]]
stat=$?
fi
return $stat
}
# usage
if [ $# -le 1 ]
then
display_usage
exit 1
fi
if [[ ( $# == "--help") || $# == "-h" ]]
then
display_usage
exit 0
fi
#Read input for IPA & IPB values and test
IPA=$1
IPB=$2
#IP Test
for IP in "$@"
do
if ! valid_ip $IP
then
echo -e "\nBad IP: $IP! Please correct and try again."
display_usage
exit 1
fi
done
#The Decimal to Hex conversion
IPAHEX=$(printf '%02x' ${IPA//./ })
IPBHEX=$(printf '%02x' ${IPB//./ })
echo Checking connection table for VS $vsname...
echo
# dump connection table, do stuff
fw tab -t connections -u | grep "$IPAHEX" | grep "$IPBHEX" | grep "^<0000000" | awk '{print $1" "$2" "$3" "$4" "$5" "$6}'|sed 's/ //g'|sed 's/</fw tab -t connections -x -e /g'|sed 's/>//g'|sed 's/;//g' > listofall
#Execute commands generated in the file
echo -e "\nThe following connections were found in the connection table:"
echo
cat listofall
echo "do you wish to delete them?"
select yn in "Yes" "No"; do
case $yn in
Yes ) echo ; echo "deleting connections..."; /bin/bash listofall; echo "the specified connections were deleted"; break;;
No ) echo "no connections were deleted"; exit;;
esac
done- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aaaand for those out there still upgrading your SMS/MDS from R77.30 who have just implemented the new DHCP services, this one's for you,
#!/bin/bash
#
# Check Point Firewall DHCP Connection Killer
#
# Version 0.01
#
# Tired of your DHCP traffic dropped by fw_conn_post_inspect Reason: Handler 'dhcp_request_code' drop?
#
# This script does one thing: queries the connection table for DHCP _requests_ (dest port:67 protocol: UDP) and kills them, if you allow it
#
# Developed for using the new dhcp_request and dhcp_reply services in a policy - see sk104114
# https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk104114
CPPROFILE_PATH=tmp/.CPprofile.sh
. $CPDIR/$CPPROFILE_PATH;
echo "Check Point Firewall DHCP Connection Killer"
echo
echo Checking connection table for DHCP traffic on VS ${vsname}...
# dump connection table, do stuff
fw tab -t connections -u | grep "00000043, 00000011" | grep "^<0000000" | awk '{print $1" "$2" "$3" "$4" "$5" "$6}'|sed 's/ //g'|sed 's/</fw tab -t connections -x -e /g'|sed 's/>//g'|sed 's/;//g' > listofall
# do same for dhcp replies, if necessary
# fw tab -t connections -u | grep "00000044, 00000011" | grep "^<0000000" | awk '{print $1" "$2" "$3" "$4" "$5" "$6}'|sed 's/ //g'|sed 's/</fw tab -t connections -x -e /g'|sed 's/>//g'|sed 's/;//g' >> listofall
#Execute commands generated in the file
echo -e "\nThe following DHCP connections were found in the connection table:"
echo
cat listofall
echo "do you wish to delete them?"
select yn in "Yes" "No"; do
case $yn in
Yes ) echo ; echo "deleting connections..."; /bin/bash listofall; echo "the specified connections were deleted"; break;;
No ) echo "no connections were deleted"; exit;;
esac
done
rm listofall- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
wow! its still alive after 5 years! haha
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Great post!
I tried to use this on R80.20 version but it didn´t work. Can anyone knows if I have to change something in the script?
Thanks a lot.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Greate !!
Many thank,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This really really saved the day for me today after SIP issues following a policy install (sk140112 "Traffic is dropped with error: "fw_handle_old_conn_recovery Reason: old packet rulebase drop"" for the Googlers). Thank you so much!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Brandon,
I am facing the same problem, after policy install SIP VoIP streams is dropped on old packer rulebase drop, although the newly installed policy allows it. Deleting the connections from the fw table resolves the issue, so does rebooting the VoIP gateways. It seems that the old SIP sessions which can be active for a long time are somehow disrupted after policy install so the firewall 'forgets' corresponding UDP ports for VoIP data stream and I have to force the SIP session to be initiated again.
This happens only sometimes, I didn't figure the conditions yet.
Did you make any progress with this issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Lukas - it's not really relevant to the topic here 🙂 best would we to start a new thread.
But my two cents: check the settings on connectivity persistence
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kaspar, I tried it already and it seem to help. But from the security view this can be considered just as a w/a...
Thanks for your point, i will no longer spam here and create a new thread.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A wonderful post which saved us after changing a NAT rule to not to NAT but kept natting based on existing connections.
It was perfectly tested on R80.30
THANK you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Kaspars_Zibarts how would you go about using this including port numbers? We have a need to reset some connections coming in from particular source ports but leaving the other connections in place.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can try this, seems to do the trick, I have highlighted the changed sections
IPA="x.x.x.x"; IPB="y.y.y.y"; SPORT="zzz"; DPORT="zzz"; SPORTHEX=`printf '%08x' ${SPORT}`; DPORTHEX=`printf '%08x' ${DPORT}`; IPAHEX=`printf '%02x' ${IPA//./ }`; IPBHEX=`printf '%02x' ${IPB//./ }`; grep "$IPAHEX" table | grep "$IPBHEX" | grep "$SPORTHEX" | grep "$DPORTHEX" | grep "^<0000000" | awk '{print $1" "$2" "$3" "$4" "$5" "$6}' |sed 's/ //g'|sed 's/</fw tab -t connections -x -e /g'|sed 's/>//g'|sed 's/;//g' > listofall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your quick response - we will give this a try. Really appreciate the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here's how to clear sessions on Check Point Maestro. I was only concerned with traffic between IPA and IPB, no matter what port is was on, so I removed that part of your script.
# let's work in the temp directory
cd /var/log/tmp
# collect the tables from all SGMs in Maestro cluster, save to a file called 'table'
g_fw tab -t connections -u > table
# filter for IP addresses we wish to clear, format the command, save to a file called 'listofall'
IPA="10.1.1.1"; IPB="10.2.2.2"; IPAHEX=`printf '%02x' ${IPA//./ }`; IPBHEX=`printf '%02x' ${IPB//./ }`; grep "$IPAHEX" table | grep "$IPBHEX" | grep "^<0000000" | awk '{print $1" "$2" "$3" "$4" "$5" "$6}' |sed 's/ //g'|sed 's/</fw tab -t connections -x -e /g'|sed 's/>//g'|sed 's/;//g' > listofall
# copy command file to all SGMs
asg_cp2blades /var/log/tmp/listofall
# run script on all SGMs
g_all bash /var/log/tmp/listofall
# you will get errors for 'not found in table connections' these can be ignored.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Colleagues, please help me to adapt this wonderful one-liner to solve the task of removing all UDP connections from the connection table.
I'm currently using fw ctl conntab -proto=17 -x , but perhaps there are more elegant options. We found that if ISP Redundancy is enabled, TCP sessions are reset when the ISP fails, but UDP sessions continue to be translated according to the old NAT rules until they are manually removed from the connection table or by timeout.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
still gold (works on R81.10.15 as well)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
After this threat pops up again I need to add something 8)
I loved your script in the past, but starting from R81.10 I think it is more handy to use fw ctl conntab.
If you are looking for specific connections use for example:
fw ctl conntab -dport=67 -dip=1.2.3.4
If you want to delete those connections use
fw ctl conntab -x -dport=67 -dip=1.2.3.4
You can also use more filters. More details you will find in the updated SK shown above (https://support.checkpoint.com/results/sk/sk103876)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have to say I had given this post link to so many customers and they were all impressed. In my opinion, definitely top 5 in the community, its EXCELLENT!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Haha it still lives after 7 years! Awesome 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im sure this method will be used by many for long, long time 🙂
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 26 | |
| 18 | |
| 15 | |
| 13 | |
| 12 | |
| 10 | |
| 6 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Thu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchThu 20 Nov 2025 @ 05:00 PM (CET)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - AMERThu 20 Nov 2025 @ 10:00 AM (CST)
Hacking LLM Applications: latest research and insights from our LLM pen testing projects - EMEAThu 04 Dec 2025 @ 12:30 PM (SGT)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - APACThu 04 Dec 2025 @ 03:00 PM (CET)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - EMEAThu 04 Dec 2025 @ 02:00 PM (EST)
End-of-Year Event: Securing AI Transformation in a Hyperconnected World - AmericasWed 26 Nov 2025 @ 12:00 PM (COT)
Panama City: Risk Management a la Parrilla: ERM, TEM & Meat LunchAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter