- Products
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- Learn
- Local User Groups
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
- Partners
- More
- ABOUT CHECKMATES & FAQ
- Sign In
- Leaderboard
- Events
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E5:
Powering Prevention: The AI Driving Check Point’s ThreatCloud
The Great Exposure Reset
AI Security Masters E4:
Introducing Cyata, Securing the Agentic AI Era
CheckMates Go:
CheckMates Fest
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Hybrid Mesh
- :
- Firewall and Security Management
- :
- Re: Disable TLS 1.0/1.1 for https inspection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Disable TLS 1.0/1.1 for https inspection
Hello,
we are dealing with the issue of how to disable the entire TLS 1.0/1.1 for outbound HTTPS inspection. I know sk126613, but we dont want to disable ciphers but used protocol. Only TLS 1.2 from GW should be allowed. The configuration should be done one GW not clients, that's a different part.
Some ciphers are used both in TLS 1.0/1.1/1.2 eg.
TLS_DHE_RSA_WITH_AES_128_CBC_SHA
so disabling only ciphers is not what we are looking for.
29 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Recommend discussing this further with TAC, as I recall this needs a change to ssl_min_ver parameter via GuiDBedit.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https://community.checkpoint.com/t5/General-Topics/Disable-TLS-1-0/m-p/70338/page/2
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thx, for some reason I miss this one in search box - Disable-TLS-1-0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Martin,
Did you find a answer to your question? I am having the same question right now and it would be great if you could share your findings 🙂 I also recall that you should edit GuiDBedit as @Chriz mentions, but i can't seem to find the correct SK for this particular question.
I also created a TAC case so if you do not have the answer i will repost it here 🙂
Regards,
Jelle
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Its this - sk107744
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Martin,
Thanks for you answer. I find it very strange that there is no exact SK describing how to achieve this for HTTPS inspection in general. Also there is no information about what to do, when this change is applied. For example there is no information about expected behavior... do we need to reboot the gateways for this change to be active? Is there traffic disruption? All is based on assumptions...
To be more exact on your previous answer, i assume that you mean that we have to execute the "workaround" mentioned in this SK?
Regards,
Jelle
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk126613: Cipher configuration tool for Security Gateways
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi G_W_Albrecht,
Thanks for your response, i am aware of the cipher tool, but disabling a TLS cipher is not the same as disabling the complete tls version...
Is it possible to completely disable TLS1.0/1.1 via the cipher tool? I mean, for example; we can have the cipher string TLS_RSA_WITH_AES_128_CBC_SHA which can be used for both TLS.1.0 and TLS1.2... (LINK)
I think the cipher tool should be extended to also disable the complete protocol or a SK should be available to completely disable these protocols.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Better select which strong cipher suites should be used. TLS_RSA_WITH_AES_128_CBC_SHA is a weak cipher suite - why ?
- Non-ephemeral Key Exchange:
This key exchange algorithm does not support Perfect Forward Secrecy (PFS) which is recommended, so attackers cannot decrypt the complete communication stream.
- Cipher Block Chaining:
In 2013, researchers demonstrated a timing attack against several TLS implementations using the CBC encryption algorithm (see isg.rhul.ac.uk). Additionally, the CBC mode is vulnerable to plain-text attacks in TLS 1.0, SSL 3.0 and lower. A fix has been introduced with TLS 1.2 in form of the GCM mode which is not vulnerable to the BEAST attack. GCM should be preferred over CBC.
- Secure Hash Algorithm 1:
The Secure Hash Algorithm 1 has been proven to be insecure as of 2017 (see shattered.io).
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
My current cipher selection:
SSL Inspection
Enabled:
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
TLS_RSA_WITH_AES_256_GCM_SHA384
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_128_CBC_SHA256
Disabled:
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_3DES_EDE_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_RC4_128_MD5
TLS_RSA_WITH_RC4_128_SHA
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@G_W_Albrecht, Thanks for you answer. This gives a way to indeed get what I'm looking for. But not yet on the initial question. How do I explicitly disable TLS version 1.0/1.1 on versions higher than R77.30?
From sk107744 is this still the correct way?
Connect with SmartDashboard to Security Management Server / Domain Management Server.
Go to File menu - click on Database Revision Control... - create a revision snapshot.Note: Database Revision Control is not supported for VSX objects (sk65420).Close all SmartConsole windows (SmartDashboard, SmartView Tracker, SmartView Monitor, etc.).
Connect with GuiDBedit Tool to Security Management Server / Domain Management Server.
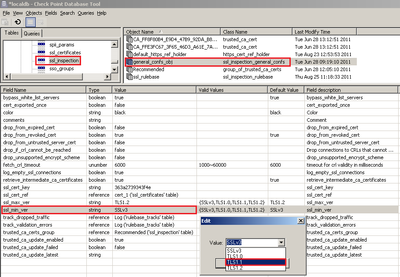
In the upper left pane, go to Table - Other - ssl_inspection.
In the upper right pane, select general_confs_obj.
Press CTRL+F (or go to Search menu - Find) - paste ssl_min_ver - click on Find Next.
In the lower pane, right-click on the ssl_min_ver - select Edit... - select "TLS1.1" - click on OK:
Save the changes: go to File menu - click on Save All.
Close the GuiDBedit Tool.
Connect with SmartDashboard to Security Management Server / Domain Management Server.
Install the policy onto the relevant Security Gateway / Cluster object.
Or do we need to use the cipher_util to implicitly disable old TLS versions to get the job done? Maybe it's my way of explaining things here but i don't seem to get 1 clear answer for this.
Anyhow, there is a existing TAC case on this 1 so ill wait what they come back with 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May well be that BOTH can be used to achieve the same result - but i would rather use cipher_util instead of GuiDBedit 8) as i can at the same time disable the weak ciphers !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
i got this same issues in R81.20. did you get a good reply from TAC? I do have a call logged with them, and a team mate has also found the same issues on a different client system, so it not just a one off.
chipher_util only show TLS1.2 and 1.3 options. GuiDBedit shows as above but i want TAC to confirm the process before i try it on production system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_Val_ ,
FYI, I asked Martin if he could share the solution he found, as you can see above he used a snippet from a Sk107744 that is EOL... Why is it, that there doesn't seem to be a (up-to-date / on the point) valid SK about this topic?
Regards,
Jelle
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sk107744 is not applicable to later versions, there is a cipher_util for supported versions. Which is dully mentioned in that very SK
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_, the cipher_util is not sufficient enough to achieve my goal if i understand this correctly.
someone can use a specific cipher for both TLS1.0/1.1 and TLS1.2. What I mean by this is that it doesn't matter if you turn certain ciphers on or off without disabling the specific versions. (A good example is disabling TLS version 1.0 via IPS where you disable the entire version) So I am looking for an SK that specifically describes how to disable the TLS1.0 and TLS.1.1 versions without having to use an outdated SK .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I believe, we have discussed this multiple times in the community over the years. On top of what was mentioned here already, https://community.checkpoint.com/t5/Security-Gateways/Disable-TLS1-0-Chekcpoint-R80-40/m-p/93023#M71...
I do not think we have an SK for this specific topic though, other than the one mentioned above. Mind, the community team is not running SecureKnowledge. If you need an official document/guidance from Check Point, please open a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@_Val_, i understand that the community is not running SK's but my question was if there is any describing my specific question. TAC case was already created but i also wanted to ask the community, because it felt like i was not able to find the correct SK/discussion for this specific question.... Hence this question. FYI the link you provide is regarding the Gaia portal not HTTPS inspection is this correct? Anyway... I will wait for a reply from TAC on this one.. Thanks anyway 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
as @Ilya_Yusupov has mentioned below, a new SK for supported versions will be available soon. We will keep you posted
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think there should be the SK and guide how to do it. I mean the official way, easy way as other vendors have it quite easy, one command or click in profile and its done.
For CP we need several threads in forum and a couple outdated SKs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I understand your argument, and I will raise this issue with our tech documentation team.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Was researching disabling TLS 1.0/1.1 on a new cluster. Is there still no clear SK on doing this? Feels like it should be a setting within Smart Console...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Val,
this sk107744 and procedure here is the same https://community.checkpoint.com/t5/General-Topics/Disable-TLS-1-0/m-p/70338#M14237
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
We are working these days to prepare a guide of how to disable correctly older TLS versions, once it will be ready we will publish the SK here as well.
Meanwhile in-order to achieve that you can use Application Control blade, choose the services of older TLS versions, enable protocol signature on those services and put in RB as Drop.
This should do the job and drop all traffic for older TLS versions.
please let me know if any further assistance is needed.
You may contact me directly via email.
Thanks,
Ilya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Ilya,
Thank you very much for your response. Good to hear that there is coming an SK to describe the correct and more important "Up to Date" information!.
Regarding the "Meanwhile" you mention, how do we achieve this without Application Control enabled? We have for example:
SSL_INSPECT + IPS
Regards,
Jelle
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @_Jelle ,
this is a bit complicated at the moment but we are looking for solution for such cases as well.
unfortunately we don't have at the moment better solution without involving Application Control blade.
we are working on finding solutions.
Thanks,
Ilya
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So eventually i just tested this out in my lab(SMS on R81.10 and (VSX)Gateway on R80.40).... I can confirm that you have 2 options:
Option 1 - use GuiDBEdit
Connect with SmartDashboard to Security Management Server / Domain Management Server.
Go to File menu - click on Database Revision Control... - create a revision snapshot.
Note: Database Revision Control is not supported for VSX objects (sk65420).Close all SmartConsole windows (SmartDashboard, SmartView Tracker, SmartView Monitor, etc.).
Connect with GuiDBedit Tool to Security Management Server / Domain Management Server.
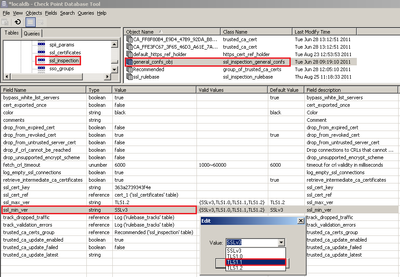
In the upper left pane, go to Table - Other - ssl_inspection.
In the upper right pane, select general_confs_obj.
Press CTRL+F (or go to Search menu - Find) - paste ssl_min_ver - click on Find Next.
In the lower pane, right-click on the ssl_min_ver - select Edit... - select "TLS1.1" - click on OK:
Save the changes: go to File menu - click on Save All.
Close the GuiDBedit Tool.
Connect with SmartDashboard to Security Management Server / Domain Management Server.
Install the policy onto the relevant Security Gateway / Cluster object.
Eventually after testing your new settings, you will see the following logs appearing when trying to connect with TLS1.0/1.1 (Don't mind the strange SSL2.0 message...)
Option 2 - Use the cipher_util
Via this route you can implicitly rule out cipher strings which are also available for TLS1.0/1.1. As discussed above you can use(for example) the cipher list that @G_W_Albrecht provided to achieve the same goal as option 1. The only thing is with option 1 you are certain(because you explicitly configured it) these old TLS versions cannot be used anymore.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 16 | |
| 15 | |
| 15 | |
| 12 | |
| 9 | |
| 7 | |
| 7 | |
| 7 | |
| 6 |
Upcoming Events
Thu 12 Mar 2026 @ 05:00 PM (CET)
AI Security Masters Session 5: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 12 Mar 2026 @ 05:00 PM (CET)
AI Security Masters Session 5: Powering Prevention: The AI Driving Check Point’s ThreatCloudTue 17 Mar 2026 @ 10:00 AM (CET)
Industrial Cybersecurity in Practice: Manufacturing & Utilities - EMEATue 17 Mar 2026 @ 03:00 PM (CET)
From SASE to Hybrid Mesh: Securing Enterprise AI at Scale - EMEATue 24 Mar 2026 @ 06:00 PM (COT)
San Pedro Sula: Spark Firewall y AI-Powered Security ManagementThu 26 Mar 2026 @ 06:00 PM (COT)
Tegucigalpa: Spark Firewall y AI-Powered Security ManagementAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter