- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Automatic HIDE NAT for BGP Failover without IS...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Automatic HIDE NAT for BGP Failover without ISP Redundancy
Hello fellow Checkpointers,
I have two ISPs with a peer on each side providing me a default gateway via BGP. (I also advertise 4 different ranges to them)
Since it's BGP, the documentation is quite clear that "ISP Redundancy does not support dynamic routing protocols" - so using it is out of the question.
I imagined weighting the peers so that ISP1-Peer is preferred over ISP2-Peer.
This means I would be receiving 2 advertisements for 0.0.0.0/0, one from each peer. ISP1-Peer's route would be installed unless it goes down, in which case ISP2-Peers default advertisement would be installed into the routing table.
Then I run into a NAT problem? (For now I'm just trying to NAT behind the gateways real address, not any of my BGP addresses). I'm used to doing manual NAT rules.
I've been doing some reading on how ISP Redundancy does this in sk174197 and sk34812.
In an attempt to recreate this myself, I tried enabling "Automatic Address Translation Rules" for each of my cluster members and selecting "Hide behind gateway".
This installs a machine hide nat rule with:
Orig Src | Orig Dest | Orig Svc | Trans Source | Trans Dest | Trans Service
fw1-obj any any fw1-obj (Hiding Address) Original Original
But when I push policy, policy verification fails with: "Module fw1-obj cannot have a NAT rule installed on 'All', the module cannot translate its own address".
And now I'm fairly confused on how to accomplish this. Would appreciate some guidance from those smarter than I.
28 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I was trying this through the cluster member properties window.
It appears I can use the automatic hide object for a given network/host object - but then I can't really organize the NAT screen into my own sections.
Once I set it on a network for "Hide Behind Gateway", it appears to be using the firewall members Cluster VIP on the WAN interface of ISP-Peer-1 (the current active default route) - so I would assume if the default route failed over to ISP-Peer-2 - it would flip to that.
So I guess the question becomes - is it possible to configure what "Automatic Hide NAT" does - but manually?
I also tried the LocalMachine dynamic object as cited by @PhoneBoy suggested in this thread: https://community.checkpoint.com/t5/SMB-Gateways-Spark/Hide-NAT-using-quot-Interface-quot-object/m-p... but to no avail
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can configure that settiong manually, but when you enable it through the object itself, it places rule(s) on its own in NAT rule base.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Forgive my ignorance, how does one accomplish creating a Manual Hide NAT rule in the same way Automatic hide nat rules behind "Gateway" are done?
The abstraction of "use whatever ip is on the interface it gets sent out on" is what I'm after.
It's been a tough week 😞
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You used to be able to configure hide NAT for 0.0.0.0 to hide NAT behind the interface that you are exiting. I have not tried that in a few versions so your mileage may vary. Looks like it is not recommended anymore: Using a "Hide behind IP address 0.0.0.0" as the translated source object (checkpoint.com)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No ignorance, all good, happy new year btw! Anyhow, what you can do to follow my example is pick random subnet, enable hide nat option and you will see 2 rules added in NAT rulebase, that will give you an idea.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks.
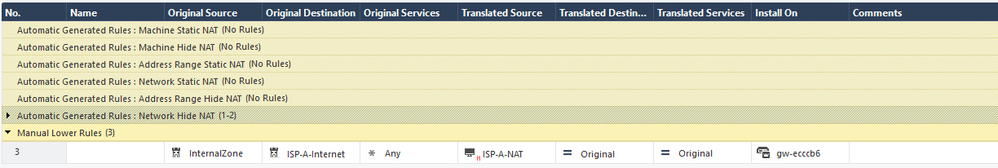
So what I get with using the Automatic Hide NAT behind gateway option using a given subnet is something like this:
Orig Src | Orig Dest | Orig Svc | Trans Source | Trans Dest | Trans Service
SubnetA SubnetA any Original Original Original
SubnetA any any (H) Subnet A (Hiding Address) Original Original
When I try to recreate this manually:
Orig Src | Orig Dest | Orig Svc | Trans Source | Trans Dest | Trans Service
SubnetA SubnetA any Original Original Original
SubnetA any any (H) Subnet A Original Original
I get "Invalid Object Subnet A in Translated Source of Address Translation Rule. Valid objects are host, gateway, gateway cluster, router, dynamic object and address range with one object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have not properly recreated the automatic NAT rule.
The "hiding address" is set on the object itself in the case of an automatic rule.
In the case of a manual HIDE NAT, the translated source NAT field needs to specify an object that resolves to either a single IP (like a gateway object) or an address range.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well if I set a single IP - I will break connectivity if I fail over to ISP2.
If I select an address range with both my WAN interfaces - it is liable to select one that isn't UP.
Does this mean I can't recreate the behavior of Automatic NAT Hide behind Gateway with Manual NAT Hide?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see one of two possibilities:
- Try using a HIDE NAT address of 0.0.0.0 to see if it works
- Write a script to monitor which ISP is active and have it change a Dynamic Object that you create and set the IP to and use in your NAT policy. This is more or less exactly what ISP Redundancy does.
Dynamic Objects are defined in the Access Policy.
The contents of that object are set using the dynamic_objects CLI command in Expert Mode on the relevant gateways.
More information on the dynamic_objects command: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
This SK seems to suggest you can set a Dynamic Object to 0.0.0.0/0.0.0.0 (done as part of an ISP Redundancy configuration): See: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some options in no particular order for lab testing might be:
- Try using Zone objects with your NAT policy (different zone for each interface/ISP)
- NAT using an object 0.0.0.0 to dynamically pickup the local interface address
- Try Dynamic objects like LocalMachine
- NAT using addresses from the advertised subnets
- Use a router external to CP to host the ISP connections
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for all the ideas.
@Chris_Atkinson wrote:Some options in no particular order for lab testing might be:
- Try using Zone objects with your NAT policy (different zone for each interface/ISP)
I don't even get the option to select a zone in Translated Source
- NAT using an object 0.0.0.0 to dynamically pickup the local interface address
I thought this was no longer recommended as mentioned here: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Try Dynamic objects like LocalMachine
I tried this but I got warnings like "Dynamic Object localmachine is used in the policy but not defined on the security gateway". Which lead me to: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
.. which I tried and then I got policy installation errors: "Failed to find a dynamic interface on DAIP module"
- NAT using addresses from the advertised subnets
This is an option
- Use a router external to CP to host the ISP connections
While this makes sense I'd like to avoid it. The CP will be terminating VPNs and I have a need to steer traffic down a specific VPN tunnel which will become problematic. Nevermind adding routing complexity. 2 of the CPs actually live on a different physical sites and what I intend to happen if the interlink goes down is: Side1 can only communicate with ISP1 and Side2 can only communicate with ISP2.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Note using Zones in the NAT policy requires Management version R81 or higher.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm 81.10 and Zones don't even show up in the "Filter" option when selecting a translated source.
I can use them in Original Source and Original Destination, but not translated columns.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Gateway version?
To be honest (though I've not tested it) I was thinking they would be used in the destination context i.e. traffic towards zone A hide behind a certain address, traffic towards zone B hide behind a different address.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Same, 81.10.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you have existing Zone objects that you use elsewhere in your policy / assigned to interfaces or are there none defined yet?
I'll take a look in my lab later this evening...
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed I do and would even prefer to keep using them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Chris_Atkinson is right, zones do work in R81 with nat tules. Does it now give you an option to add them? I just tested in my lab and its there for both src/dst.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
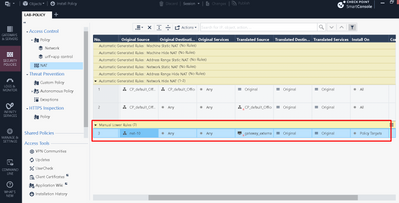
It is not. Only in Original Source and Original Destination. Not Translated columns: 
I'm also still unable to recreate the "Automatic Hide NAT rules" manually (as we discussed above) without getting "Invalid Object Subnet A in Translated Source of Address Translation Rule. Valid objects are host, gateway, gateway cluster, router, dynamic object and address range with one object"
I'm defo 81.10, show version all:
Product version Check Point Gaia R81.10
OS build 335
OS kernel version 3.10.0-957.21.3cpx86_64
OS edition 64-bit
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You cant add them in translated column, only original, so thats expected. As far as creating manual hide nat rules, I would need to see for myself.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For reference this is the rule I just verified / installed in the lab (haven't done any testing beyond this point).
Both the Original Source & Original Destination reference zone objects that I located via text search.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, I can do that. But my objective here is outgoing NAT.
Interface A is ISP1
Interface B is ISP2
Both are advertising a default route to me, I'm preferring ISP1 - so by default I am NAT'ing behind the IP of interface A.
But if ISP1 goes down, ISP2's default routes take over.
I would need the NAT to change to Interface B.
With your screenshot, since it would always use the first NAT rule - it would attempt to NAT behind an ip of an interface that is down.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As long as you have proper default gateway for that IPS link in gateway properties and internal networks are hide-natted behind gateway external IP, if one link fails, then when users go to the Internet, if they were to do whatismyip.com, they would get presented with your 2nd ISP link IP address.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And that is indeed what's happening when I use a Subnet Object and select "Automatic Hide NAT behind Gateway".
Now I just wish I could create that manually for better organization in the NAT table.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
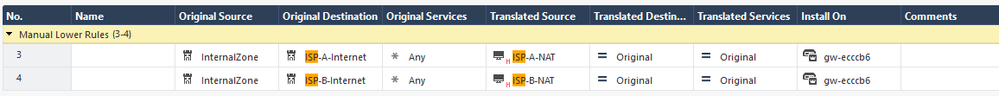
@PhoneBoy is right, you need something like below. Now, I get your point about having NAT rule that does not have to be "active" at this point, so not sure best way to go about except disable it.
Here is nat rule that would work:
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That would work, as long as the ISP for your "gateway_external" is UP. (ISP1 in my case)
ie: 0.0.0.0/0 via x.x.x.x on Interface A
If ISP1 goes down, I would then get a routing table change where 0.0.0.0/0 is now via y.y.y.y on Interface B.
Yet the first NAT rule to be hit would still be Interface A's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see what you are saying, thats true. Sorry, not sure at this point best way to go about it, lets see if anyone else may know.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Indeed depends how we calculate the Zone relative to the egress interface it's tagged to, possibly an RFE.
I've sought some feedback internally based upon the following example:
CCSM R77/R80/ELITE
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 9 | |
| 7 | |
| 7 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter