- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Remote Access VPN
- :
- Re: SMBv2-v3 on Mobile Access File Share (and not ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
SMBv2-v3 on Mobile Access File Share (and not only SMBv1 - CIFS)
Hi,
I've found some unclear information regarding Server_Message_Block versions supported on mobile-access-blade file-share functionality.
What is unclear? We have "A file share defines a collection of files (...) such as SMB for Windows" in the MobileAccess Admin Guide R77 or in the sk104577 ATRG: Mobile Access Blade .
Even the sk111097 Slow upload speed of files via Mobile Access File Share (CIFS for example) says "CIFS for example".
BUT referring the sk112202 File Shares using SMBv2/SMBv3 cannot be accessed using the Mobile Access Blade File Share applicatio... : Mobile Access only support SMBv1 (formerly CIFS) and not SMBv2 nor SMBv3 (on any version and any platform).
Even in the ATRG, we have the picture bellow:
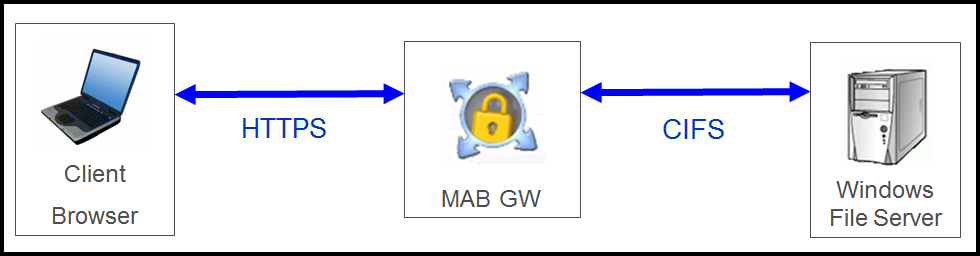
So, could we:
- Be more accurate and say that only SMBv1 (CIFS) is supported on Mobile Access File Share functionality
- support SMBv2 or SMBv3 ?
I've asked yesterday team to understand if there is a plan to support such versions.
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can force it on the server side, I think, which is the correct approach.
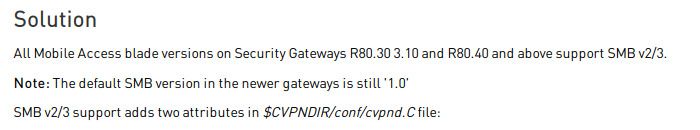
In any case, we only support SMBv2/v3 on releases with Linux 3.10 kernel (default in R80.40).
In any case, we only support SMBv2/v3 on releases with Linux 3.10 kernel (default in R80.40).
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reason we don't currently support SMBv2/v3 has to do with the Linux kernel we are using.
Once the gateway supports a newer kernel (like is planned for R80.20), it should be possible to support SMBv2/v3.
However, I can't say if R80.20 will support this out of the gate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And secureknowledge team answered:
R&D responded: "It's a known RFE."
sk was modified accordingly.
The Solution part of the sk112202 as been effectively updated:
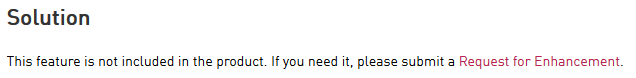
So: do not hesitate to Request for Enhancement.
Cybersecurity Evangelist, CISSP, CCSP, CCSM Elite
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ouch, I'm disappointed as SMB1 should be gone everywhere... too many vulnerabilities in it (remember wannacry?)
Check this link, even Microsoft wants it to be obsolete: https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1/
I'll submet the RFE right now as only supporting SMB1 is not worthy for a security vendor!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not to pile on here, but SMBv1 does not handle latency in excess of what is typically encountered on a LAN very well. Quoted from the second edition of my book:
Special Case: CIFS/SMB Performance over VPN
The well-known CIFS/SMB (Common Internet File System/Server Message Block)
protocol frequently experiences degraded performance in the context of a site-to-site or
Remote Access VPN, but probably not for the reason you think. Commonly used for
mounting drive shares (among other functions) in Microsoft Windows networks,
CIFS/SMB version 1 was originally intended and optimized for use in a low-latency
LAN environment. Part of this optimization was the requirement that for every certain
amount of data sent (called an Application Block Size which ranges between 4KBytes-
64Kbytes), an acknowledgement must be received from the peer before any more data
can be sent. Note that this peer acknowledgement requirement is part of CIFS/SMB
itself, and completely unrelated to the underlying transport protocol such as TCP window
sizes or ACKs. The Network File System (NFS) protocol was also originally designed to
run across a LAN with assumed low latency.
While this performance limitation of CIFS/SMB version 1 is not directly related to
the use of a VPN, the networks employed by a VPN such as the Internet tend to have
significantly higher latency than LAN or private WAN connections. There could be an
impressive 10Gbit of Internet bandwidth between two sites on the Internet, but if the
latency is 100ms or greater, CIFS performance across the VPN (or even in the clear) will
be dismal no matter what you do.
While there is really no firewall tuning we can perform to improve this situation,
there is something you can do: Try to force the systems involved to utilize SMB version
2.1 or higher which supports pipelining; many very old Windows systems still default to
SMBv1. While the peer acknowledgement requirement still exists in SMB version 2.1
and later, pipelining allows multiple Application Blocks to be in transit between the
peers simultaneously instead of just one block at a time. Ensuring the use of SMB
version 2.1 or higher can provide dramatic CIFS/SMB performance improvements across
a VPN or any other network with high latency.
--
Second Edition of my "Max Power" Firewall Book
Now Available at http://www.maxpowerfirewalls.com
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
old topic, but just wanted to reply that Gaia on kernel 3.10 gateways support SMBv2/v3
So that is one reason to reinstall your gateways instead of upgrading so you can use the new kernel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, there a way to force "SMBv3 only" on the Gaia?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can force it on the server side, I think, which is the correct approach.
In any case, we only support SMBv2/v3 on releases with Linux 3.10 kernel (default in R80.40).
In any case, we only support SMBv2/v3 on releases with Linux 3.10 kernel (default in R80.40).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi! The default for 80.30 is SMBv1, not v2/3. You must enforce the SMBv2/3 on Gaia side.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 4 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 | |
| 1 | |
| 1 | |
| 1 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter