- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: SIP over TLS non standard ports
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
SIP over TLS non standard ports
Starting a couple days ago I've been having problems with some of our video conferencing applications.
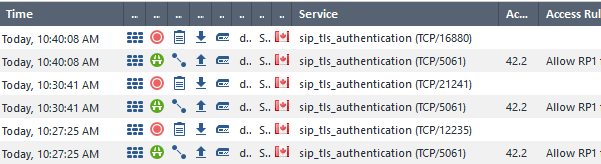
We use RP1cloud as our VC service. Normally we would see traffic on tcp5061 head out accepted. Now i'm seeing traffic dropped with the gateway as the target on non SIP ports alongside the normal traffic.
See non standard ports here. The drops are destined to our external IP, and accepts are to the VC cloud service:
The drop logs show the following
In order to allow the inspection of encrypted SIP over TLS connections, please add the 'sip_tls_with_server_certificate' service to the relevant rule,
make sure that the 'sip_tls_authentication' service is removed from the rule and configure TLS on the corresponding SIP Server object
I found the following SK related to this VoIP Configuration message, however i'm unsure if it's viable for this situation:
No changes have been made on the firewall between when it was and wasn't working.
Anyone have thoughts on the behaviour change? I'm unsure why I'm seeing the odd TCP ports being listed in the SIP_tls_authentication service.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty easy fix. I just used the predefined 'sip_tls_not_inspected' instead of 'sip_tls_authentication' and it began working.
Not sure why it suddenly stopped working unless our vendor changed to TLS encrypted SIP.
I'm guessing the odd TCP port range is just how the firewall logs the dropped traffic.
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Pretty easy fix. I just used the predefined 'sip_tls_not_inspected' instead of 'sip_tls_authentication' and it began working.
Not sure why it suddenly stopped working unless our vendor changed to TLS encrypted SIP.
I'm guessing the odd TCP port range is just how the firewall logs the dropped traffic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This didnt work for me. We have the same problem here, but even if I put services to "ANY" the connection is not allowed.
Do you have a further idea?
Best regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Linus,
Any doesn't actually match for any service, only servies that are marked as being able to be matched by any.
If I remember correctly neither of the SIP protocols are matched by any, so you would need to specify them or modify them to be matched by any.
I'd recommend making a rule specifying your sip traffic. If you are seeing your SIP traffic in your logs, is it being accepted or blocked?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi David,
according to the documentation, the match for any should only take place, when there are more then one service, that matches the connection:
"Match for Any: Indicates whether this service is used when 'Any' is set as the rule's service and there are several service objects with the same source port and protocol."
I have also tried to use "sips_tcp_tls_noprotocol" and "sips_tcp" but without success. The log shows drops, with stating "Encrypted VoIP signaling over TCP is not allowed" and "In order to allow the inspection of encrypted SIP over TLS connections, please add the 'sip_tls_with_server_certificate' service to the relevant rule,
make sure that the 'sip_tls_authentication' service is removed from the rule and configure TLS on the corresponding SIP Server object" but there is no such service-object.
according to the documentation, the match for any should only take place, when there are more then one service, that matches the connection:
"Match for Any: Indicates whether this service is used when 'Any' is set as the rule's service and there are several service objects with the same source port and protocol."
I have also tried to use "sips_tcp_tls_noprotocol" and "sips_tcp" but without success. The log shows drops, with stating "Encrypted VoIP signaling over TCP is not allowed" and "In order to allow the inspection of encrypted SIP over TLS connections, please add the 'sip_tls_with_server_certificate' service to the relevant rule,
make sure that the 'sip_tls_authentication' service is removed from the rule and configure TLS on the corresponding SIP Server object" but there is no such service-object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Linus,
I am having the same issue. My rule uses the following services: TCP3100-33499; gsip_tls_not_inspected; gsip_any-tcp. Seeing the logs, I found that several ports are being dropped using the gsip_tls_authentication (TCP/33227) object and so on.
Any idea how to fix it?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It worked for me using sip_tls_not_inspected instead of sip_tls_authentication
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 16 | |
| 6 | |
| 5 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter