- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Problem in facing SIC Management to Branch off...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
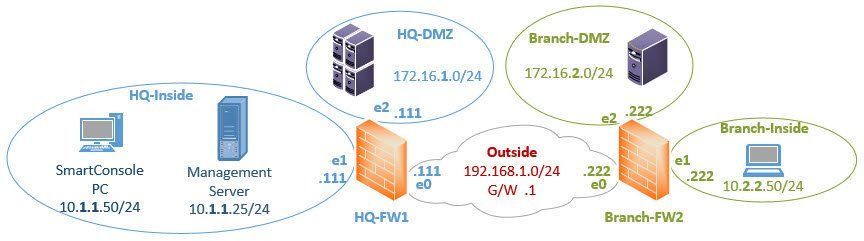
Problem in facing SIC Management to Branch office firewall
Hi All,
Currently i build my Home lab for CCSA R.76 .
When i try to add or link Management and Branch Firewall SIC is not establishing
Note : HQ F-W and Management SIC established working fine no problem with that,,.please help #CCSA .76
Can some one help me to resolve my problem
@cbtnuggets R76
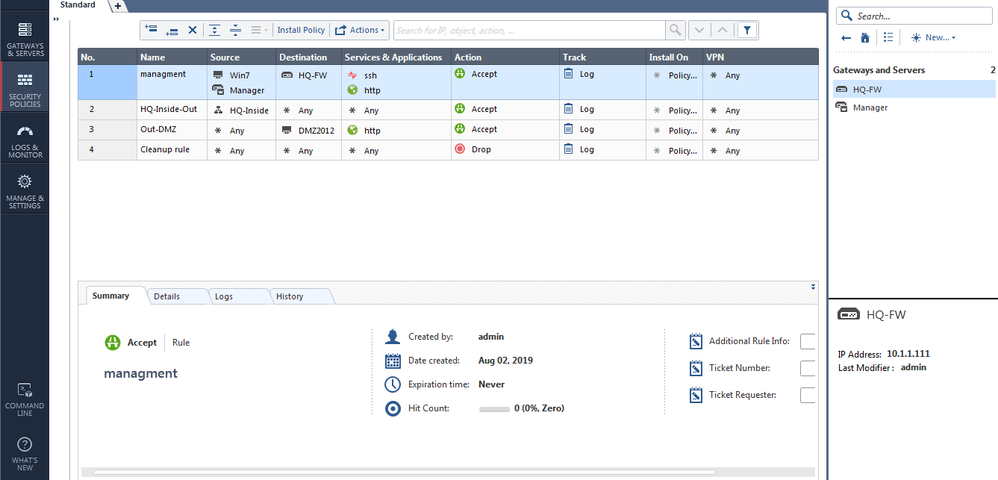
Below are the topology :
26 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume routes are ok.
I think you have not pushed policy to HQ-FW1 after creating object of Branch-FW2 with correct IP.
This is necessary for HQ-FW1 to create relevant implied rules to allow Mgmt/GW-communication!
I think you have not pushed policy to HQ-FW1 after creating object of Branch-FW2 with correct IP.
This is necessary for HQ-FW1 to create relevant implied rules to allow Mgmt/GW-communication!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI Norbort,
Thanks for reply,
I have one management , for the first gateway (HQFW) SIC is established.
In rule base table , I allow any source any destination is accept which mean from management to FW-2 need to form SIC but in my case ,SIC is not established ...Please help
Thanks for reply,
I have one management , for the first gateway (HQFW) SIC is established.
In rule base table , I allow any source any destination is accept which mean from management to FW-2 need to form SIC but in my case ,SIC is not established ...Please help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Routes are ok?
Can you reach gw2 from mgmt using SSH for example?
What are you seeing in log?
Have you tried capturing packets on gw1 using tcpdump/fw monitor?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
from Management i added routes to 10.1.1.111
on GW 1 i added routes to 192.168.1.1 outside ,so i taught from management we can able to reach GW2 ..
whether i need to add routes from GW2 to Management, Is it necessary ?? Please reply
on GW 1 i added routes to 192.168.1.1 outside ,so i taught from management we can able to reach GW2 ..
whether i need to add routes from GW2 to Management, Is it necessary ?? Please reply
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
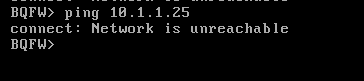
I havent verified logs and but
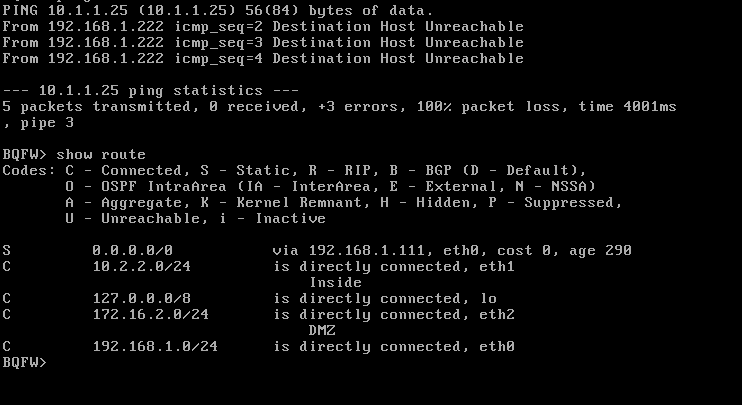
From management to GW2 when i ping 192.168.1.111 its unreachable..
So which means there is problem with routes ? Correct me if i am wrong..
From management to GW2 when i ping 192.168.1.111 its unreachable..
So which means there is problem with routes ? Correct me if i am wrong..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Because this is the lab an you are trying to determine if your routing is OK, do the following:
In your SmartConsole go to Global Policy Properties and enable ICMP as well as "Log Implied Rules".
SSH into your branch gateway (or open an emulated console) and perform "fw unloadlocal".
Its default policy will be blocking ICMP.
Then verify that your routing is working and that you are getting ICMP responses where expected.
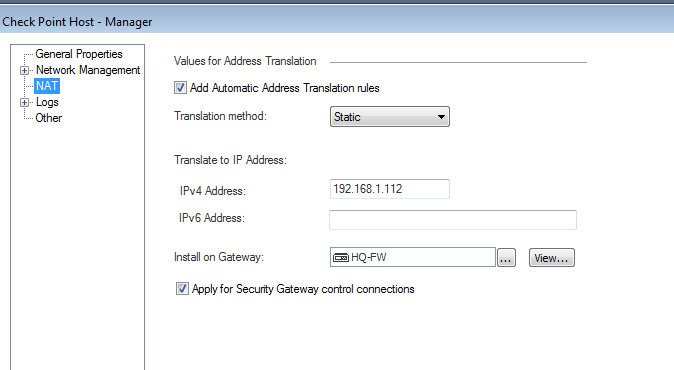
Configure Static NAT for the Management Server object to translate its internal IP into one of the available IPs in 192.168. network.
Cheers,
Vladimir
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir,
Still facing same issue ,Unable to for SIC between Management to B-FW
Unable to ping Management
help..
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have no route on your gateway! As management is not in a directly attached network, you need to add correct routing!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Akram_wasim , your management server's IP is not in your FW2 routing table.
If you want to ping it, provided the static NAT is assigned to the Management server's object, you should be able to ping the IP you are NATing it to, i.e. one in the 192.168.1.*/24 range.
Otherwise, provided you have ICMP enabled in Global properties, you should add a route to 10.1.1.25/255.255.255.255 to your BQF or specify the route to the entire 10.1.1.0/24 network with the next hop being external IP of your primary gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
can you help how to add route in B-FW ,Seriously i cant do it .Please help
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you are using WebUI, it is self-explanatory.
If you are trying to do this via Clish:
On your Management server (where SMS is the hostname of your management server):
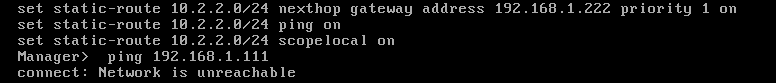
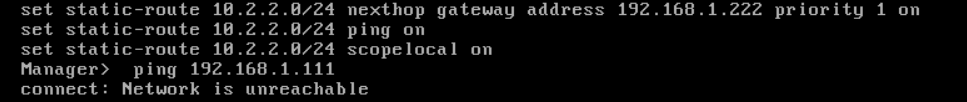
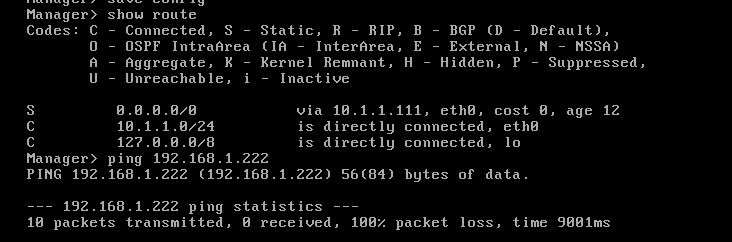
SMS> set static-route default nexthop gateway address 10.1.1.111 on
SMS>save config
On your HQ-FW1:
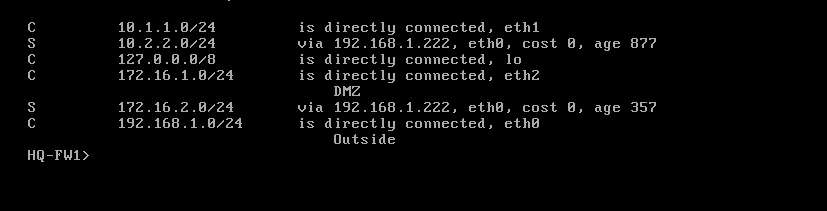
HQ-FW1> set static-route 10.2.2.0/24 nexthop gateway address 192.168.1.222 on
HQ-FW1> set static-route 172.16.2.0/24 nexthop gateway address 192.168.1.222 on
HQ-FW1>save config
On your Branch-FW2:
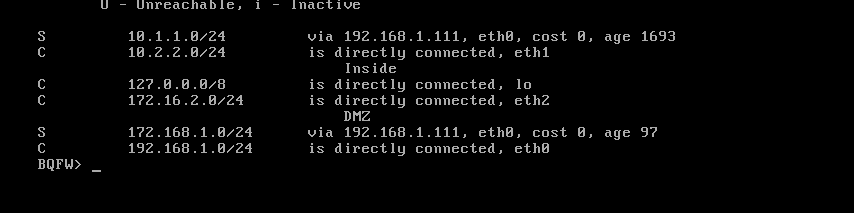
BQFW> set static-route 10.1.1.0/24 nexthop gateway address 192.168.1.111 on
BQFW> set static-route 172.16.1.0/24 nexthop gateway address 192.168.1.111 on
BQFW>save config
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
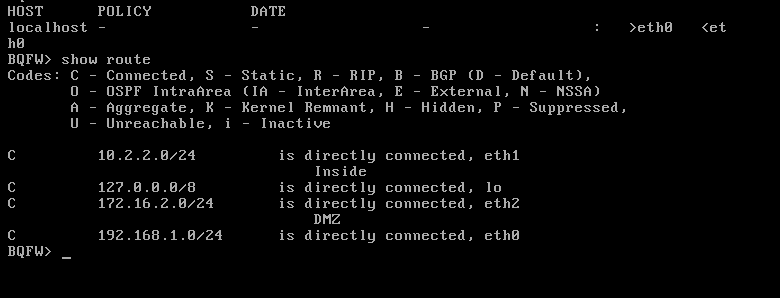
Hi,
Added all route as per instruction you had given to me but same issue nothing has changed ,able to ping FW2 to Manager
Above are current routing table after you shared me new routes ,i added everything and enable icmp in the global properties ,,i done everything ,, This is so headache,, i am unable to figure out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Show the route on your management server.
Have you created the firewall objects, defined their topology, configured security policy for the HQ-FW, published it and installed?
If not, you cannot expect this to work unless you perform "fw unloadlocal" on both firewalls.
Please show a screenshot of your policy here.
Please show the "Network" property of both firewall objects here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
P.S. In your management server's screenshot, the routes shown are NOT the one I have wrote you to add:
On your Management server (where SMS is the hostname of your management server):
SMS> set static-route default nexthop gateway address 10.1.1.111 on
SMS>save config
VS. yours:
Your management server cannot know how to reach the 10.2.2.0/24 network, your HQ-FW does.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir ,
This is current scenario
Manager to FW 1 - Ping working
FW1 to Fw 2 ping working
Fw2 to FW 1 Ping working
FW2 to Manager Ping working
real problem exist " Manager to FW 2 Ping not working"
Is it because of VMnet setting or i really dont know mate.
I can see all routes in the routing table
Policy also install
why i dont know SIC is not establish FW2 to Manager ,when though all policy and routes available ,,why ??
Help ..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
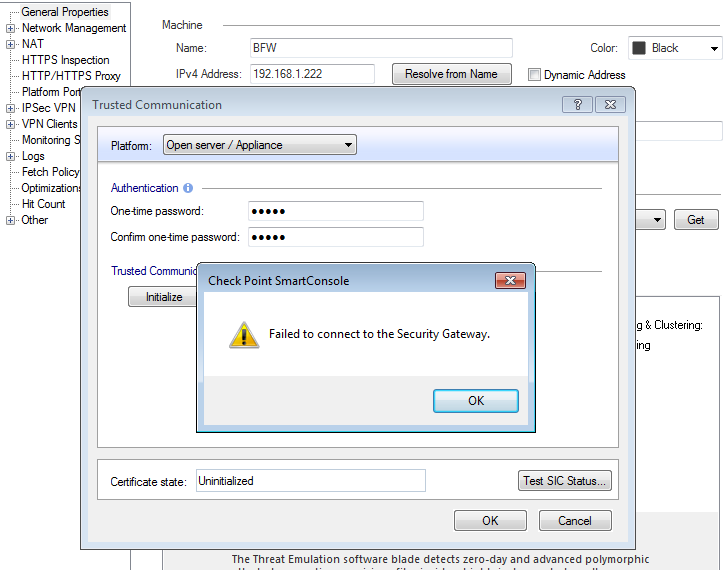
Hi Vladimir
Same issue
1. I have enabled the ICMP in Global properties
2. add default routes from BFW to FW1 external IP
I am unable to ping ..
Pic 1 : Add static Nat from Manager to 192.168.1.112
Pic 2 : routing table FW 2
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you ping from BQFW the IP of 192.168.1.112?
Have you enabled the "Log Implied Rules" in Global properties to see where your ICMP traffic is going in the logs?
You either use static NAT and refer to the Management server by its' NATed IP (the most common scenario in practice), or in your lab environment, do not NAT, but rely on static routes.
As shown in your screenshot below, the Static NAT is being applied to the "Security Gateway control connections".
This means that you should be able to establish SIC with BQFW even in the absence of ICMP, if your routing is correct.
Try performing "fw unloadlocal" on the BQFW and ping and trace route to it from your management server to see where things are breaking down.
Additionally, verify that on your Management Server the default route is configured to use FW1 internal interface as it's gateway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you ping 192.168.1.222 from your HQ-FW1?
Answer : No
Can you ping 192.168.1.111 from your Branch-FW2?
Answer : No
Can you ping your 10.1.1.111 from your management server?
Answer : No
What do you see in logs when looking for ICMP traffic?
I dont know how to check ICMP logs in Checkpoint ,Can you share me the command in CLISH
In Logs and monitor i cant find any icmp traffic
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK Vladimir ,I will check and come back if there is any issue..
Thanks
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
manager routes
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you ping 192.168.1.222 from your HQ-FW1?
Can you ping 192.168.1.111 from your Branch-FW2?
Can you ping your 10.1.1.111 from your management server?
What do you see in logs when looking for ICMP traffic?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now i am to ping Management -FW1-FW2 eachother
But SIC not forming ,,Still something is missing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When you configured the branch firewall, have you configured it as a standalone or as a gateway only?
If it is configured correctly, as a gateway only and if you did not restrict its management in Gaia, reset SIC via cpconfig on the branch firewall, verify that its object configured properly, and re-initialize SIC for it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have some doubt whether i am setup VMnet setting correctly
Do you have any idea of Vmwareworkstation Vmnet detting
in my case Management - Vmnet 1
FW1 - Vm1 ,vmt 2 ,vmnet 3
FW2 - Vmnet1 ,Vmnet2,Vmnet3
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have one doubt,, I am almost there ,,
when i configured B-FW i select only Gateway ,,
My quiz ,,Can one management server SIC support two gateways ??
Whether SIC password need to be same on both GW ?
Now I am ping FW1 to FW2
But cant ping from FW2 to Management and also FW1
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 15 | |
| 13 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter