- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Identity Awareness - Could not connect to AD s...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Identity Awareness - Could not connect to AD server
Hello everyone,
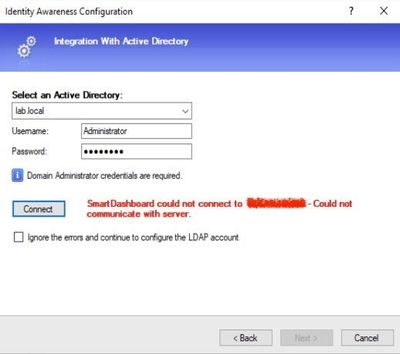
I tried to test the Identity Awareness Blade on my lab and connect to a AD server but always got the error message on SmartDashboard (R80.30):
"SmartDashboard could not connect to x.x.x.x - Could not communicate with server."
I did several troubleshooting things like mentioned on the link below:
I can connect to the AD server without any error from the cli on my security gateway using "test_ad_connectivity" and "ldapsearch" but from SmartDashboard it does not work.
I moved on with checking the box "Ignore the errors and continue to configure the LDAP account" and put in the login DN which worked fine. I also activated Browser-based Authentication which I could test successfully from my test client.
I did a packet capture on the AD server to check if there is any traffic from the security gateway to the AD server during the activation of AD Query within the Wizard, but there are no packets arrived on the AD server.
I also tried to add a LDAP Account Unit before activating the Identity Awareness blade, so that you can choose it from the dropdown within the configuration wizard. Adding the LDAP Account Unit worked also without errors, but during the AD Query activation it failed again to connect like before.
Anyone had similar issues or any experiences with that error?
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2 things to check:
Can your client directly access the AD server?
Can your Management server directly access the AD server?
Have you enabled NTLMv2 and pushed policy?
From expert mode run: adlogconfig a
Check the setting for NTLMv2 make sure it is enabled, if not enable it and push policy!
Can your client directly access the AD server?
Can your Management server directly access the AD server?
Have you enabled NTLMv2 and pushed policy?
From expert mode run: adlogconfig a
Check the setting for NTLMv2 make sure it is enabled, if not enable it and push policy!
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firewall rules?
Source: SmartConsole IP
Destination: AD Server IP
Service: Port 135 AD query
More read here:
R80.x - Ports Used for Communication by Various Check Point Modules
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're right, Daniel.
So, one of the Active Directory servers was decommissioned on the environment, that was the cause of the issue.
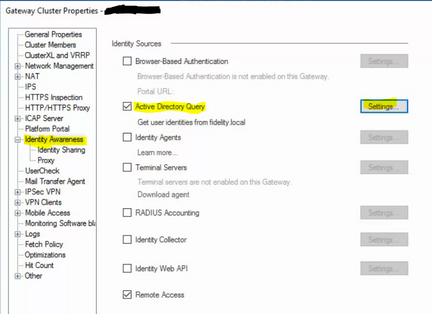
First, I checked the Identity Awareness settings on the SmartConsole:
Gateway Cluster Properties > Identity Awareness > Active Directory Query > Settings and confirmed the name of the Object that define the Active Directory Domains.
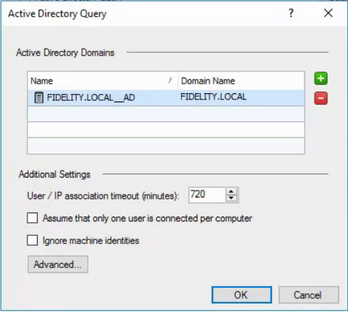
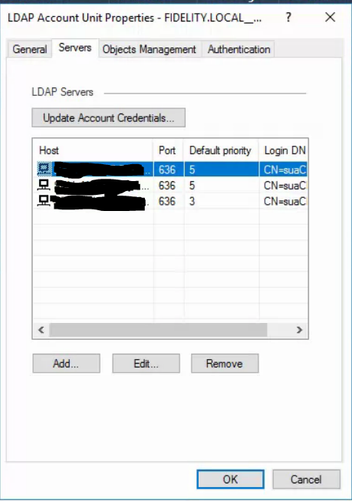
Then, I located the FIDELITY.LOCAL__AD object and removed the decommissioned server from the servers list.
After publishing the changes and installing the policies, the issue was resolved.
Hope that it was helpful.
Cheers!
Saulo
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2 things to check:
Can your client directly access the AD server?
Can your Management server directly access the AD server?
Have you enabled NTLMv2 and pushed policy?
From expert mode run: adlogconfig a
Check the setting for NTLMv2 make sure it is enabled, if not enable it and push policy!
Can your client directly access the AD server?
Can your Management server directly access the AD server?
Have you enabled NTLMv2 and pushed policy?
From expert mode run: adlogconfig a
Check the setting for NTLMv2 make sure it is enabled, if not enable it and push policy!
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Maarten, thanks a lot for your reply. I could solve the issue now. As I already thought it was a simple error. The problem was that I was not able to connect to the AD server from the management client pc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firewall rules?
Source: SmartConsole IP
Destination: AD Server IP
Service: Port 135 AD query
More read here:
R80.x - Ports Used for Communication by Various Check Point Modules
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The client your connecting from, the firewall(cluster) and SmartCenter should be able to connect to the AD server. The client workstation proxies on behalf of the management station and the firewall also verifies it can communicate to the AD server. If you go into expert mode on firewall and run following:
nslookup
> set type=srv
>_ldap._tcp.<domain_name>
It should return back the AD servers in the environment. If it does not then you need to fix either (a) reverse lookup for your domain (b) the dns server on the firewall. I have seen where people will use the ISP dns servers and this breaks AD query. Also, I would suggest you look at Identity Collector (sk108235) it is much more stable way of doing identity awareness and is less resource intensive on both your firewall and AD server(s).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Heiko, thanks a lot for your reply. The link you posted was very helpful for troubleshooting and I bookmarked it for future usage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Daniel!
I'm having the same issue with the Identity Awareness blade. But my problem is with the AD server setting on the CheckPoint.
The Identity Awareness wizard is detecting mu domain but it is trying to connect to a AD server that has been decommissioned long ago.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Were you able to solve the issue? Seems like you need to re-initialize (disable/enable) Identity Awareness... (I'm only guessing because I don't know your environment)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Daniel,
Yes, I managed to get it sorted.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What did you do to get it solved? Maybe others can benefit from your experiences.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're right, Daniel.
So, one of the Active Directory servers was decommissioned on the environment, that was the cause of the issue.
First, I checked the Identity Awareness settings on the SmartConsole:
Gateway Cluster Properties > Identity Awareness > Active Directory Query > Settings and confirmed the name of the Object that define the Active Directory Domains.
Then, I located the FIDELITY.LOCAL__AD object and removed the decommissioned server from the servers list.
After publishing the changes and installing the policies, the issue was resolved.
Hope that it was helpful.
Cheers!
Saulo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Saulo!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Like you, we have 3 domain controllers, but in our scenario, one of the servers was not decommissioned, but just crashed one day.
The purpose of listing the 3 DCs in the LDAP unit is for redundancy.
However, when that server crashed, IA completely failed and did not work anymore. Remote Access users could not be authenticated until that server was restarted.
Do I need to specifically set "If you can't access this DC, use that DC instead" anywhere, to get this to work?
Isn't that the point of listing multiple DCs in the LDAP unit?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 8 | |
| 6 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter