- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- HowTo: Block IoT scanners like Shodan, Censys, Sha...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
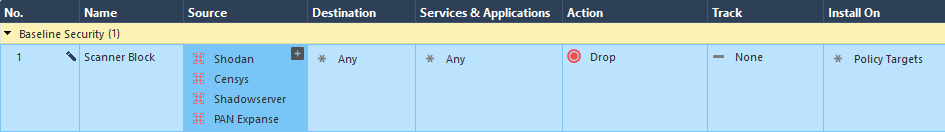
HowTo: Block IoT scanners like Shodan, Censys, Shadowserver, PAN Expanse etc.
Protect your environment against all those internet IoT port scanners / web crawlers that scan your network devices to collect all kind of data. Simply create a drop rule and put it on the beginning of your security policy. Create a network group for each of these scanners and fill it with the data listed below.
Supported scanners:
- Shodan --> see Check Point Threat Alert
- Censys --> see their FAQ
- Shadowserver --> see their FAQ
- PAN Expanse --> feeds their Expander
Sample rule:
Group contents:
- Shodan --> create domain objects with FQDN enabled!
.census1.shodan.io.census2.shodan.io.census3.shodan.io.census4.shodan.io.census5.shodan.io.census6.shodan.io.census7.shodan.io.census8.shodan.io.census9.shodan.io.census10.shodan.io.census11.shodan.io.census12.shodan.io.atlantic.census.shodan.io.pacific.census.shodan.io.rim.census.shodan.io.m247.ro.shodan.io.pirate.census.shodan.io.ninja.census.shodan.io.border.census.shodan.io.burger.census.shodan.io.house.census.shodan.io.mason.census.shodan.io.turtle.census.shodan.io.goldfish.census.shodan.io.flower.census.shodan.io.dojo.census.shodan.io.cloud.census.shodan.io.sky.census.shodan.io.inspire.census.shodan.io.battery.census.shodan.io
- Censys
74.120.14.0/24162.142.125.0/24167.248.133.0/24192.35.168.0/23
- Shadowserver
64.62.202.96/2766.220.23.112/2974.82.47.0/26184.105.139.64/26184.105.143.128/26184.105.247.192/26216.218.206.64/26141.212.0.0/16
- PAN Expanse
144.86.173.0/24
- Others
Additional info:
Adding such a drop rule on top of your access control rulebase helps raising the baseline security level of your overall firewall security policy. Other free methods to raise it even more are:
- dynamically block blacklisted IPs early - even before your access control rulebase
- or via Custom Intelligence Feeds (IoC Management) if you have AV/ABOT licensed
- or via Generic DataCenter objects starting from R81+
- create a leading ordered layer to drop unwanted incoming traffic based on Geo Location
- use SNORT rules to advance your IPS protection profile
- if you don't have IPS licensed, use at least IPS Core Protections and Inspection Settings that are both installed with your access control policy
- activate HTTPS inspection
- enable and use Content Awareness
- enable and use Identity Awareness
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nice one Danny!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great work Danny.
Would have been nice if Check Point could add those hosts as dynamic objects so it would be automatically updated when any of the scanners changes ip subnets
Best Regards
Kim
Kim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Kim_Moberg the best way to request this is to add a feedback note to sk173416.
Citing from the SK:
Can I suggest to support a specific service as an Updatable object?
Suggestions for additional Updatable objects can be submitted in the "Give us Feedback" section of the SecureKnowledge article, with the relevant information that will be rendered by R&D (who is responsible for adding new updatable objects). The most common suggestions will get highest priority:
- Service name
- Link to public content maintained by the vendor
- Is it currently used in my policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Censys has different and more IPs listed to Opt-Out as per,
https://support.censys.io/hc/en-us/articles/360043177092-Opt-Out-of-Scanning
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for this post, and I used it to create a rule on my firewall to block the traffic, but can I ask why the individual urls for shodan? Could we just block .shodan.io and get all of them?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Because FQDN Domain Objects cannot be used with wildcards.
You could put shodan.io into a Custom Threat Intel feed (ioc_feeds command) or in a Network Feed object (R81.20 and above).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Terri_Hawkins use of wildcard-FQDN objects as source or destination will result in massive performance degrading, because of the needed DNS reverse lookups. See Traffic latency through Security Gateway when Access Control Policy contains non-FQDN Domain objects
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you both very much. I believe I have some work to do on some of my rules now. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good afternoon
Will these rules work if we have implied rules where ports 80,443,264,18264 are allowed?
As far as I know implied rules come before firewall rules.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How are these implied rules defined?
HowTo: Block IoT scanners like Shodan, Censys, Shadowserver, PAN Expanse etc.
Protect your environment against all those internet IoT port scanners / web crawlers that scan your network devices to collect all kind of data. Simply create a drop rule and put it on the beginning of your security policy. Create a network group for each of these scanners and fill it with the data listed below.
Supported scanners:
- Shodan --> see Check Point Threat Alert
- Censys --> see their FAQ
- Shadowserver --> see their FAQ
- PAN Expanse --> feeds their Expander
Sample rule:
Group contents:
- Shodan --> create domain objects with FQDN enabled!
.census1.shodan.io.census2.shodan.io.census3.shodan.io.census4.shodan.io.census5.shodan.io.census6.shodan.io.census7.shodan.io.census8.shodan.io.census9.shodan.io.census10.shodan.io.census11.shodan.io.census12.shodan.io.atlantic.census.shodan.io.pacific.census.shodan.io.rim.census.shodan.io.m247.ro.shodan.io.pirate.census.shodan.io.ninja.census.shodan.io.border.census.shodan.io.burger.census.shodan.io
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 15 | |
| 8 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter