- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- How to unhide 'user_name: ******;' when calling cu...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
How to unhide 'user_name: ******;' when calling custom script as a SmartEvent correlation rule?
I'm just not finding references to unhiding additional fields when calling a custom correlation rule, as detailed here:
I essentially have a script which will simply log all input passed to it:
[Expert@checkpoint-management:0]# cat $RTDIR/bin/ext_commands/block_on_clearpass
#!/bin/bash
EVENT=$(cat)
echo $EVENT >> /tmp/block_on_clearpass
This in turn yields the following data being collected:
[Expert@checkpoint-management:0]# tail -n 1 /tmp/block_on_clearpass
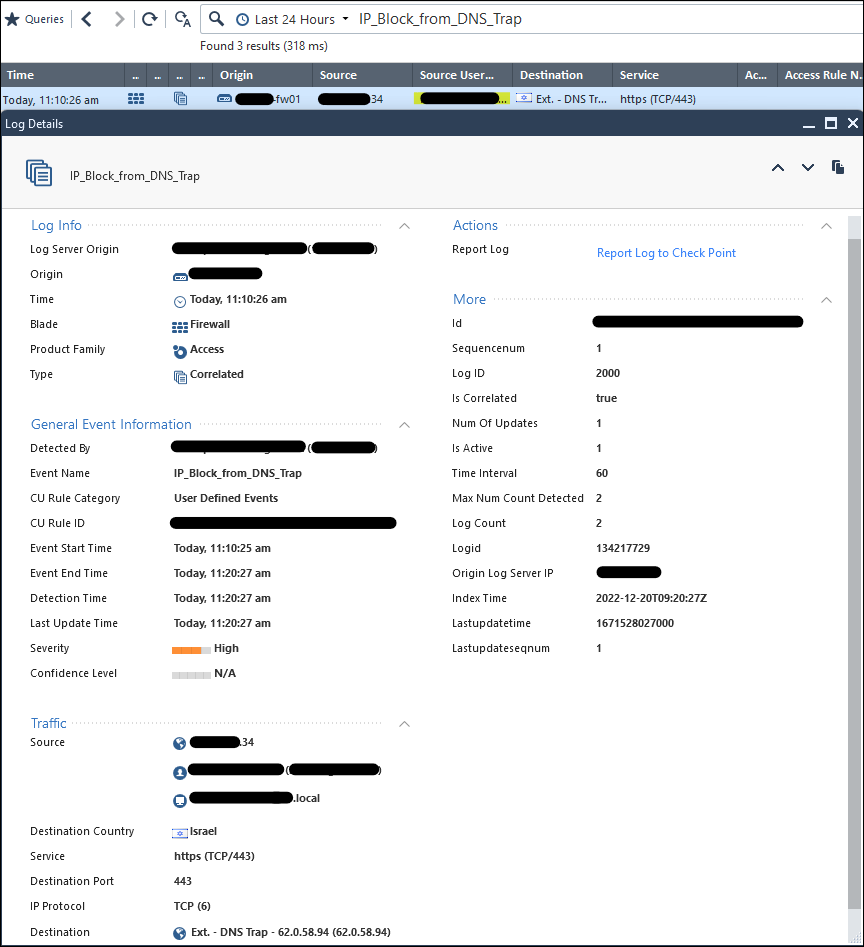
(StartTime: 20Dec2022 11:10:26; Uuid: deadbeef-dead-beef-dead-beef00000000; rowid: ENdeadbeef-dead-beef-dead-beef00000000; id_generated_by_indexer: false; first: true; sequencenum: 1; log_id: 2000; DisplayName: IP_Block_from_DNS_Trap; Category: User Defined Events; cu_rule_id: DEADBEEF-DEAD-BEEF-DEAD-BEEFDEADBEEF; is_correlated: 1; num_of_updates: 0; is_last: 0; event_start_time: 1671534625; detection_time: 2022-12-20T09:10:26Z; time_interval: 60; max_num_count_detected: 2; cu_log_count: 2; cu_detected_by_hostname: checkpoint-management; cu_detected_by: 172.254.254.23; users_repetitions: 2; aba_customer: SMC User; source_repetitions: 2; origin_repetitions: 2; destination_repetitions: 2; service_repetitions: 2; Severity: High; type: Correlated; ProductName: VPN-1 & FireWall-1; product_family: Access; Destination: (hostname: ******; countryname: Israel; IP: 62.0.58.94; repetitions: 1) ; Origin: (IP: 0; hostname: redacted-fw01; repetitions: 1) ; Service: (port: 443; protocol: 6; servicename: https; repetitions: 1) ; Source: (user_name: ******; IP: 172.254.254.23; machine_name: ******; repetitions: 1) ; logid: 392281947) ;
PS: I understand the importance of sanitising input variables, is this possibly simply a safety mechanism so that people can be warned about the dangers?
The logs themselves do contain user identities:
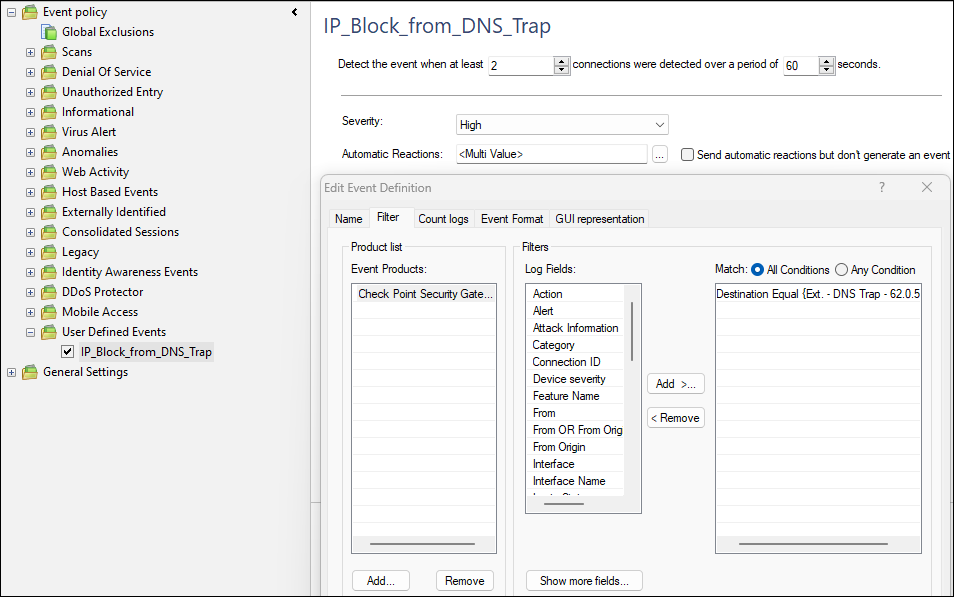
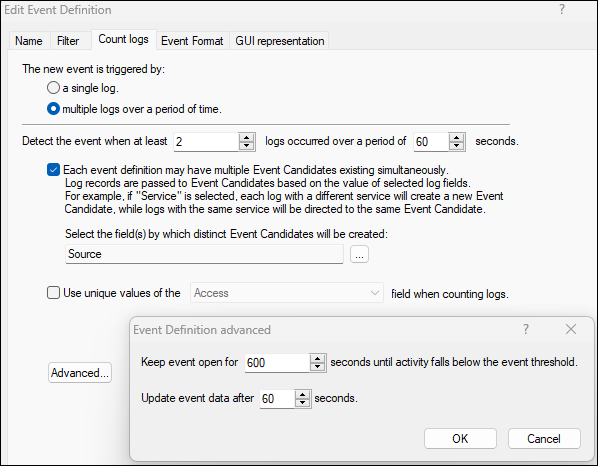
SmartEvent is configured as follows:
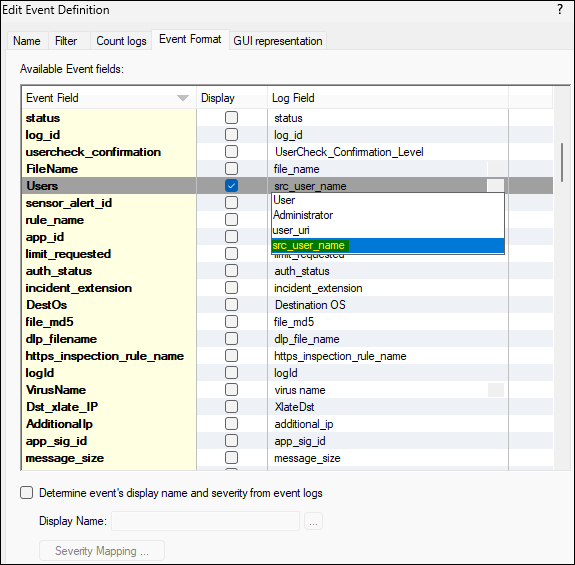
We did add the 'Users' event field with the 'src_user_name' field:
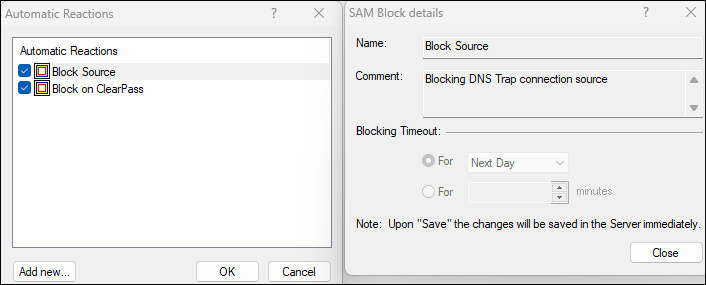
This then has two actions, the first to drop traffic from that source:
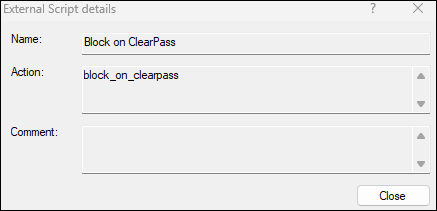
And the 2nd to stop the device being able to communicate with other devices in the same subnet. For now I'm simply calling the custom script detailed above:
Regards
David Herselman
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
An old known issue: sk68020: In E-mail alerts sent by SmartEvent, the user name field contains '*** Confidential ***' in...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
3 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
An old known issue: sk68020: In E-mail alerts sent by SmartEvent, the user name field contains '*** Confidential ***' in...
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hope the following saves someone else time in future, it should hopefully:
- Sanitise input
- Extract the username who's devices we wish to drop off the network
- Call an API
- Log debug information
[Expert@checkpoint-management:0]# cat $RTDIR/bin/ext_commands/block_on_clearpass
#!/bin/bash
INPUT=$(cat);
CURL_OUTPUT='';
EVENT="${INPUT//[^a-zA-Z0-9 ().,:;+_-]}";
USERID=`echo "$EVENT" | sed -r "/user_name/ s/.*user_name: ([[:alnum:]_-]+).*/\1/"`;
[ ${#USERID} -ge 4 ] && [ ${#USERID} -le 20 ] && CURL_OUTPUT=`curl_cli -kX POST -H 'Content-type: application/json' --data '{"text":"Hello, World!"}' https://hooks.slack.com/services/RANDOMSTRINGPROVIDEDBYSLACK --fail --silent --show-error 2>&1`;
if [ ${#CURL_OUTPUT} -gt 0 ]; then
echo -e "User: $USERID\nCurl debug data: \n$CURL_OUTPUT" >> /tmp/block_on_clearpass;
else
echo -e "User: $USERID - Curl return code: $? - Sanitised event data:\n$EVENT" >> /tmp/block_on_clearpass;
fi
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 13 | |
| 13 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter