I'm just not finding references to unhiding additional fields when calling a custom correlation rule, as detailed here:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_LoggingAndMonitoring_AdminGuide/To...
I essentially have a script which will simply log all input passed to it:
[Expert@checkpoint-management:0]# cat $RTDIR/bin/ext_commands/block_on_clearpass
#!/bin/bash
EVENT=$(cat)
echo $EVENT >> /tmp/block_on_clearpass
This in turn yields the following data being collected:
[Expert@checkpoint-management:0]# tail -n 1 /tmp/block_on_clearpass
(StartTime: 20Dec2022 11:10:26; Uuid: deadbeef-dead-beef-dead-beef00000000; rowid: ENdeadbeef-dead-beef-dead-beef00000000; id_generated_by_indexer: false; first: true; sequencenum: 1; log_id: 2000; DisplayName: IP_Block_from_DNS_Trap; Category: User Defined Events; cu_rule_id: DEADBEEF-DEAD-BEEF-DEAD-BEEFDEADBEEF; is_correlated: 1; num_of_updates: 0; is_last: 0; event_start_time: 1671534625; detection_time: 2022-12-20T09:10:26Z; time_interval: 60; max_num_count_detected: 2; cu_log_count: 2; cu_detected_by_hostname: checkpoint-management; cu_detected_by: 172.254.254.23; users_repetitions: 2; aba_customer: SMC User; source_repetitions: 2; origin_repetitions: 2; destination_repetitions: 2; service_repetitions: 2; Severity: High; type: Correlated; ProductName: VPN-1 & FireWall-1; product_family: Access; Destination: (hostname: ******; countryname: Israel; IP: 62.0.58.94; repetitions: 1) ; Origin: (IP: 0; hostname: redacted-fw01; repetitions: 1) ; Service: (port: 443; protocol: 6; servicename: https; repetitions: 1) ; Source: (user_name: ******; IP: 172.254.254.23; machine_name: ******; repetitions: 1) ; logid: 392281947) ;
PS: I understand the importance of sanitising input variables, is this possibly simply a safety mechanism so that people can be warned about the dangers?
The logs themselves do contain user identities:
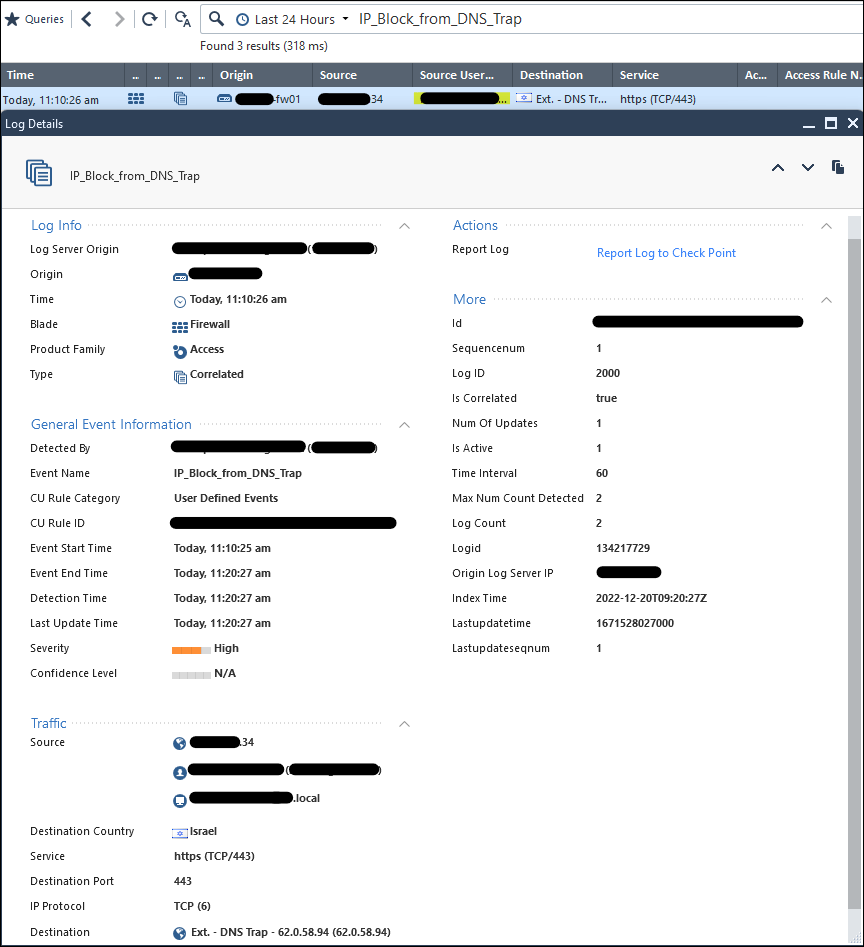
SmartEvent is configured as follows:
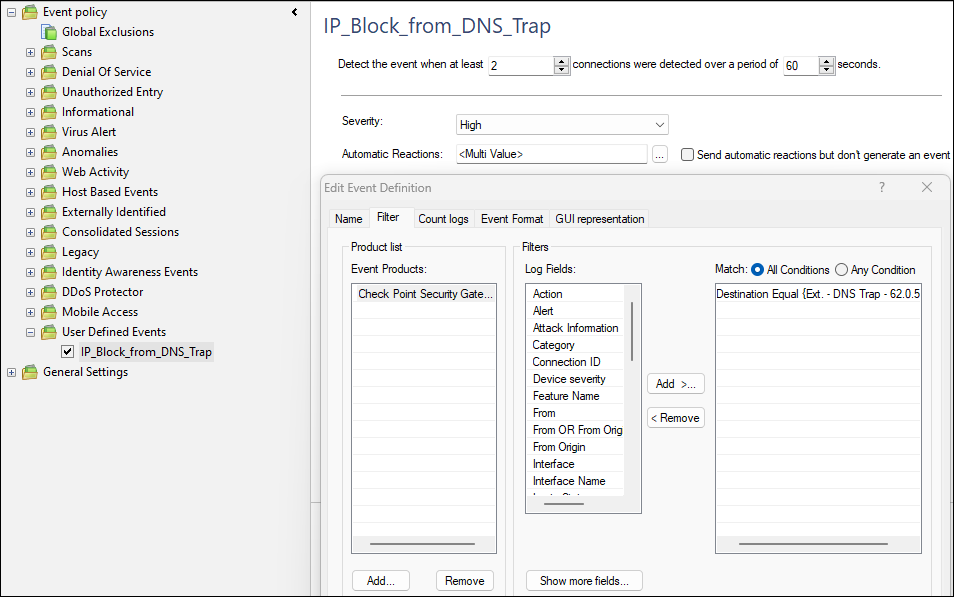
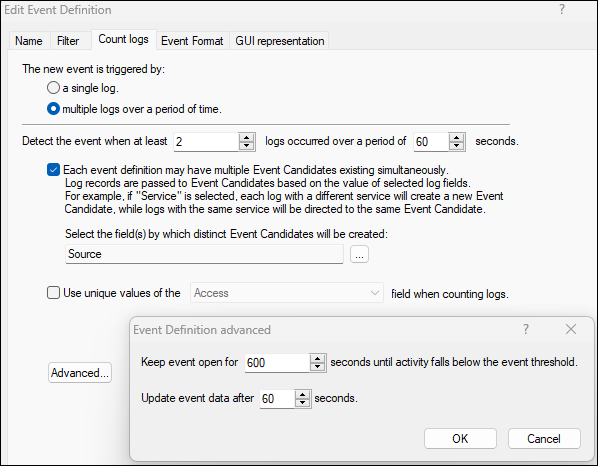
We did add the 'Users' event field with the 'src_user_name' field:
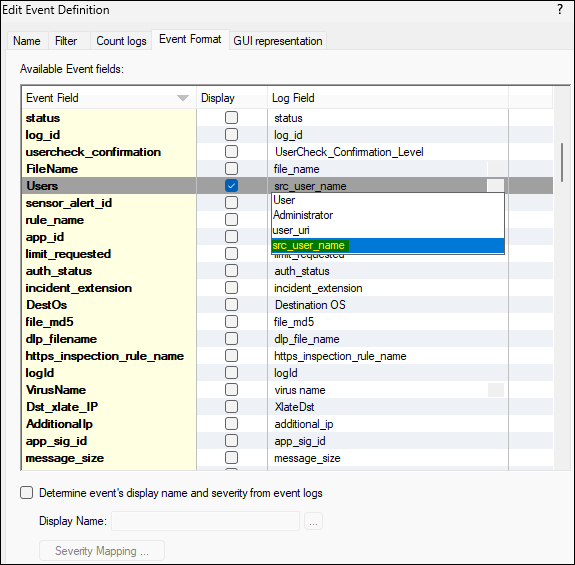
This then has two actions, the first to drop traffic from that source:
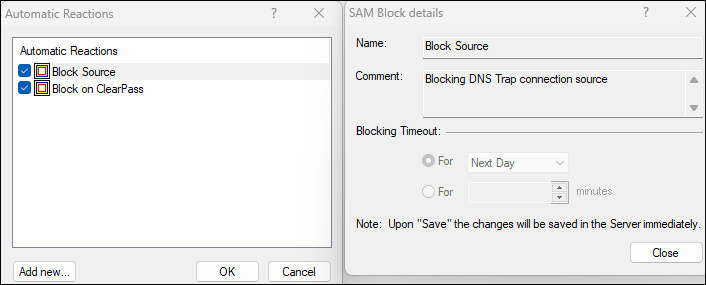
And the 2nd to stop the device being able to communicate with other devices in the same subnet. For now I'm simply calling the custom script detailed above:
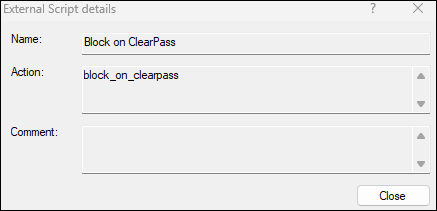
Regards
David Herselman








