- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Register HereCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
MVP 2026: Submissions
Are Now Open!
Overlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Getting Started Managing Multiple Gateways
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Getting Started Managing Multiple Gateways
Hi All,
We have just purchased a couple of smaller security gateways for remote offices (cool!). I have a 12400 series appliance on site at our main office here, along with a management server, etc.
I am starting to read up and plan for configuring these new gateways, and I am trying to find some information on managing multiple gateways from a single management server, and how I would create and apply policy. This is of course assuming that using a single management server is realistic? The remote offices are small with only a handful of users at each, so I am not worried about moving lots of logs or anything; I am mostly just curious about designing and deploying policy.
Any tips / advice would be greatly appreciated! (Sorry, still using R77.30, and I wasn't sure where else to post!)
~David
Labels
- Labels:
-
Policy Installation
-
SmartConsole
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a fine place to post your question ![]()
Unified management is definitely the way to go here, it will make your life simpler in the end. There's a couple of approaches you can take in terms of building policy:
1. One policy to rule them all. Create a single policy that applies to all your gateways. You can create gateway-specific rules that are only applied on specific gateways (using the Install-On column). This is not an approach I see regularly and I think it makes the policy more complicated overall. It's not what I would recommend.
2. Create a different policy package for your Branch Offices. If you want to use your existing policy as a basis, you can do a File > Save As and create a new Policy Package (after saving other changes you might have made). One thing you definitely want to do to ensure the wrong policy isn't installed on the wrong gateways is go to Policy > Policy Package Installation Targets and specify the specific gateways the Policy Package applies to.
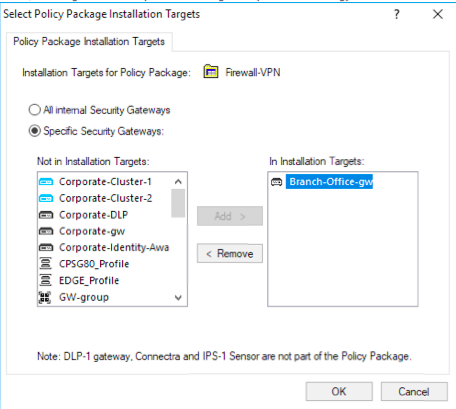
The downside to #2 is that you will have to duplicate rules (particularly App Control/URL Filtering rules) across your two policy packages, but the resulting policies should be simpler to manage.
When you upgrade to R80.10+, you can have both policies use the same App Control/URL Filtering rules using the same inline layer.
I realize this will probably result in more questions, but it should be enough to get you started.
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is a fine place to post your question ![]()
Unified management is definitely the way to go here, it will make your life simpler in the end. There's a couple of approaches you can take in terms of building policy:
1. One policy to rule them all. Create a single policy that applies to all your gateways. You can create gateway-specific rules that are only applied on specific gateways (using the Install-On column). This is not an approach I see regularly and I think it makes the policy more complicated overall. It's not what I would recommend.
2. Create a different policy package for your Branch Offices. If you want to use your existing policy as a basis, you can do a File > Save As and create a new Policy Package (after saving other changes you might have made). One thing you definitely want to do to ensure the wrong policy isn't installed on the wrong gateways is go to Policy > Policy Package Installation Targets and specify the specific gateways the Policy Package applies to.

The downside to #2 is that you will have to duplicate rules (particularly App Control/URL Filtering rules) across your two policy packages, but the resulting policies should be simpler to manage.
When you upgrade to R80.10+, you can have both policies use the same App Control/URL Filtering rules using the same inline layer.
I realize this will probably result in more questions, but it should be enough to get you started.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon Welch Abernathy wrote:
The downside to #2 is that you will have to duplicate rules (particularly App Control/URL Filtering rules) across your two policy packages, but the resulting policies should be simpler to manage.
When you upgrade to R80.10+, you can have both policies use the same App Control/URL Filtering rules using the same inline layer.
With R80 and R80.10 Management, you can change the application control & URL filtering layer to a shared layer and reuse that layer across your multiple policies - see https://community.checkpoint.com/thread/1091 .
The ability to share the same set of rules is a Management-Only feature, therefore you can start by just upgrading your Management to R80.10, use this feature, and later plan your Gateway migration.
If I could recommend on best practices for policy organization, I would start by upgrading the Management server so you can start enjoying some of the benefits of layers. Later you could also upgrade your gateway and segment your rule sets into smaller chunks, which can give you the better ease of management.
hope this helps
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks to you both for the responses - I appreciate the guidance on separate policy packages and layers, etc.
So, I hadn't thought about just upgrading the management software up to R80.10... I am trying to get enrolled in a CCSA / CCSE class - I was initially thinking to go with a R77.30 class, but maybe I will go to 80.10.
Thanks again!
~D
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Personally, I think if you're just learning about Check Point now, it's best to learn on the most recent version as there are some significant differences between R80+ and R77.x.
Even if you keep your gateways at R77.30 for the time being, there will be significant benefit to upgrading your management to R80+.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dameon,
Thanks so much - and I agree. I have been going back and forth on it... but R80 it is ![]()
Best,
~D
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I know this is an old post but I'm sure it still mostly applies. With R81, assuming I have a cluster (2 sec gateways) at each site to manage - does this require a separate multi-domain management license?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would start with user and application policy awareness.
SDP : Software-Defined Protection (SDP) | Check Point Software
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the comment Ofir!
Just to keep things simple - SDP is just an approach to applying Check Point's software, yes? This is not another product / blade / service, per-se?
Thanks!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SDP describes a security architecture, it is not a product or service.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 11 | |
| 9 | |
| 7 | |
| 6 | |
| 4 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationTue 27 Jan 2026 @ 11:00 AM (EST)
CloudGuard Network Security for Red Hat OpenShift VirtualizationFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


