- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Firewall allowing traffic without Access Polic...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Firewall allowing traffic without Access Policy
Hello,
I am new here.
I am having an Issue with an R80.30 Gateway that is allowing inbound traffic on 443 without an access policy in place.
I think it is based on NAT, I do have a DNAT in place for 443 traffic, I thought Access policy must be matched in order to allow traffic ?
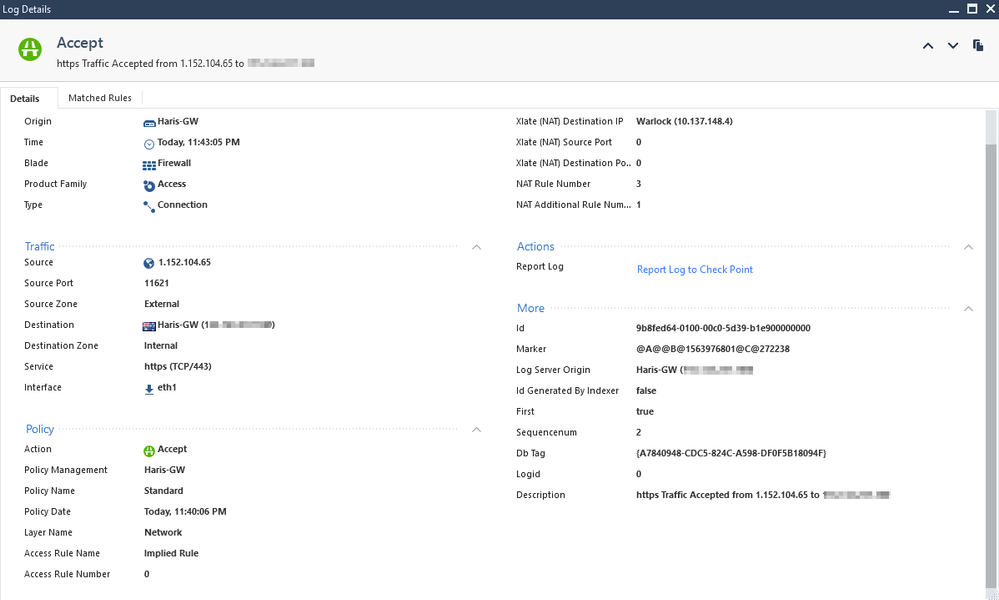
The said traffic is not showing up on any logs either.
Fw monitor I can see the traffic hit the WAN side not I cant see any other details after that. I am filtering based on source IP.
fw monitor -m iIoO -l 56 -T -e '{accept(((src=123.32.234.234,dport=443) or (sport=443,dst=123.32.234.234)),[9:1]=6);}'
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. Enable "Log Implied Rules" in Global Policy settings and install the policy on GW.
2.Change the "Cleanup rule" to log.
3. Check if your gateway managed via port 443 for WebUI.
If the answer to [3] is a "Yes", change the management port to something else in the gateway's properties and re-install the policy.
You should see the traffic in the logs at this point and see the reason for it being allowed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for that.
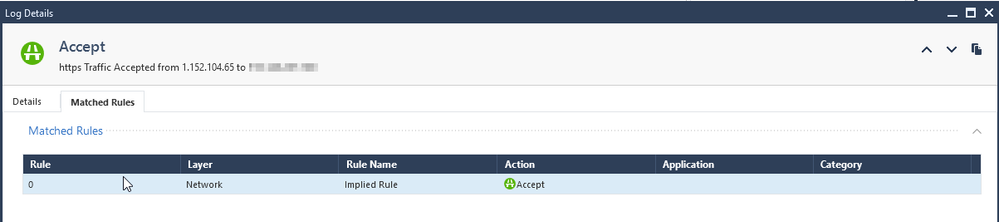
I can now see the traffic is matching the implied rule 0
I changed the default WebUI port to something other than 443. still matching an implied rule.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For Security Gateway:
In SmartConsole, perform:
- Open the Security Gateway / Cluster object and go to the "Platform Portal" pane.
- In the "Main URL" field, set the desired port (e.g., port 4434):
https://IP_ADDRESS:PORT - Click on OK to apply the changes.
- Install the security policy on this Security Gateway / Cluster object.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Another thing to check, (triple check and then check again) is your topology. A common misconception is Topology is just about anti-spoofing. Topology literally defines the Internet to the gateway. Without the correct topology, the gateway won't have a clue of what is inside or outside. If an internal subnet missing or a wrong mask it can cause really strange unexpected rule matching.
If you need to make any adjustments, do them manually, never select the get interfaces with topology option on a gateway that's in production service or more unexpected results may occur and can take you down. Also you must keep your topology up to date with any adds/changes on the inside network ongoing. If you have a route to a subnet on the Inside network, you need to add that subnet to the topology on the appropriate inside interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
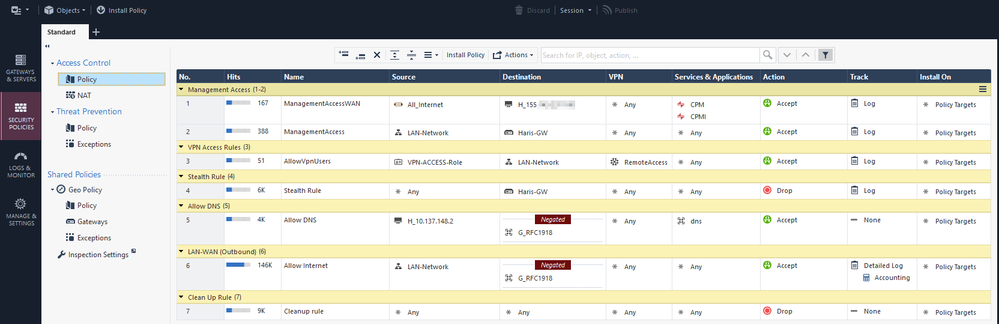
Definitely change the web port in Platform Portal as suggested previously. But at the top of your access policy rule base you need to have a couple of rules. First Rule would be to create a group for internal IP's that can access the firewall via port 443, SSH, etc.. for management. Then the 2nd rule should be Source Any to Destination firewall IP, ports = Any then set to deny and log. Also remember to place a cleanup rule at the bottom of your access control policy.
CCSE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Every,
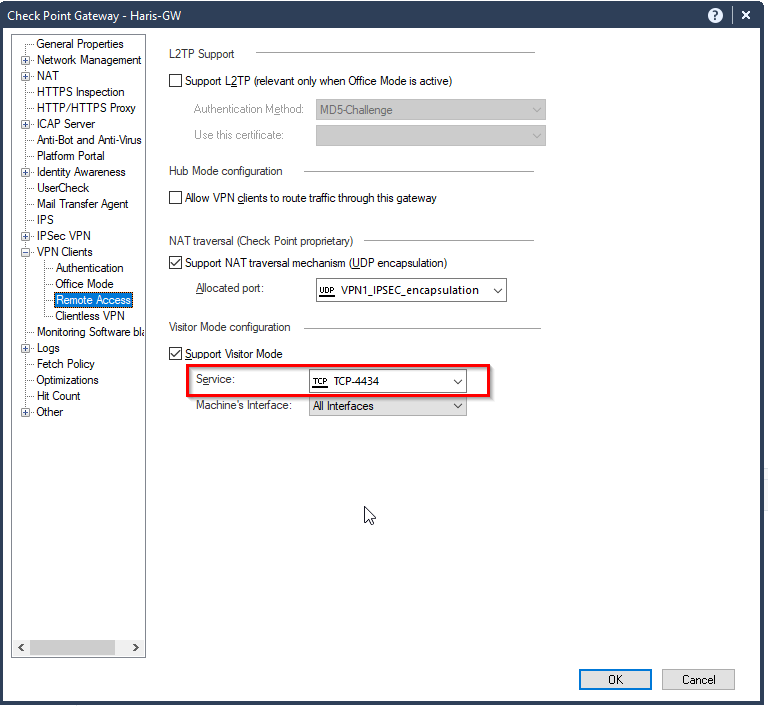
Thanks for all your help so far. I have narrowed it down to visitor mode. Even if I obscure the port for visitor mode. The implicit rule still passes https traffic through.
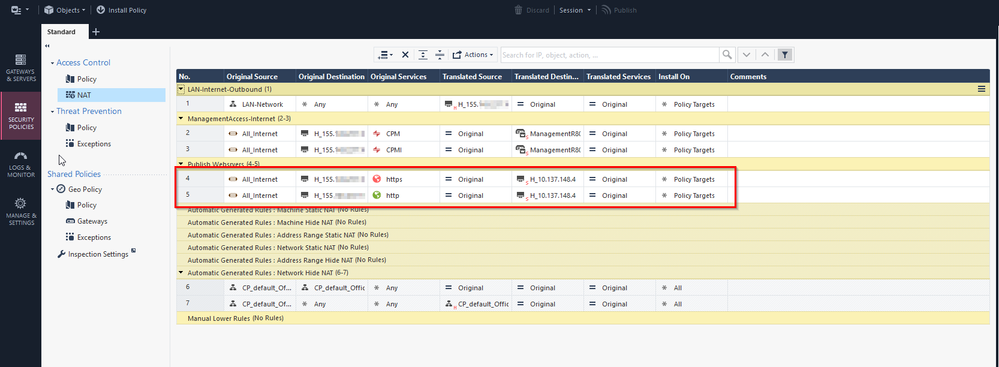
In my NAT I have a DNAT rule to NAT HTTPS/HTTP to a webserver.
In my access policy I don't have any rules to allow traffic to my Webserver located at 10.137.148.4.
Problem : As soon as I enable visitor mode (even on port 4434). My web-server is accessible from the internet because the implicit rule is matched and all HTTPS/HTTP traffic can freely hit my web-server. How do I stop this behavior.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear All
I am having the same problem.
We do not have a access control policy defined, but ping and traceroute are being allowed by the Firewall.
The Log implied rule was not enabled, I have enabled it and now I can see that the access is being allowed by the implied rule 0.
Any help on how we can solve this.
Thanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Within SmartConsole, right click your gateway object and select View. Then click Network Management and it will display your active interface Name, Topology, & IP address. What does it say in the Topology section for each interface?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can confirm the topology is correct.
Wan Interface -----》 External
Lan Interface -------》 Internal.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. Is the server on the same exact subnet as your internal interface IP or on a different subnet another internal router hop away?
2. If on a different subnet, right click the interface and view again to drill deeper, then click view in the topology section. What is selected?
If Leads To is Not Defined (internal) and your server is on a different subnet then you need to set your topology to Specific and put in a network group object with the internal subnets listed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Server is in the same subnet.
Gateway IP ( internal) is 10.137.148.1/24
Server ip is 10.137.148.4/24
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just an update, I still have not been able to solve this.
I have narrowed it down to visitor mode.
Even when I select the different port for visitor mode on the VPN side.
Port 443 is always used and hence the implied rule is always hit on Port 443.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir
Thats actually enabled.
Does it have an impact when disabled?
Thanks
Thats actually enabled.
Does it have an impact when disabled?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When enabled, it'll permit ICMP unconditionally, (i.e. Rule 0).
When unchecked, you'll have to specify rules permitting ICMP where needed.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 8 | |
| 6 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter