- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Certain options missing under action column in...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
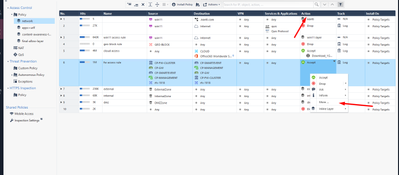
Certain options missing under action column in management policy
Hey guys,
Hope someone might be able to help me with this, as Im totally stumped what might be "missing". So I was helping client with unrelated issue and realized that in their environment, when they click option more under policy action column, they do NOT get anything I see in my lab (below), except action and captive portal.
I verifed policy layer editor and they have exact same things selected , along with same blades, as I do in my lab.
Any idea whats missing? They also cant see ask and inform like I do in 1st screenshot.
Things we tried:
-made sure smart console is updated, reinstalled R81.20 smart console
-tested a different PC
-rebooted the mgmt
Version is R81.20 jhf 89.
Tx as always.
Andy
Best,
Andy
Andy
3 Solutions
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
An actual screenshot from their environment might help.
You should also check the blades enabled in the relevant policy layer as that will impact what shows in the Track column.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As @PhoneBoy suggested these options will be shown only if the Layer Editor has Applications & URL Filtering or Content Awareness enabled.
With just Firewall there is no need for them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey gents @Lesley @Amir_Senn @Chris_Atkinson @Tal_Paz-Fridman @PhoneBoy
I figured it out, always learn something new every day, hehe 🙂
So, turns out their policy editor was not exactly same as mine, apologies, I missed something yesterday. Technically, if you ONLY have fw blade enabled inside policy layer, you will NOT see extra options, as I dont see them in final allow layer in my lab where I have fw blade enabled only and I do see those options in first 3 layers.
Thanks guys as always for the help and I attached few screenshots showing this.
Andy
Best,
Andy
Andy
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is identity awareness completely configured?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is. In my lab, I only have IC configured and works fine. Btw, this is R81.20 jumbo 89, both mgmt and cluster.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do they see the same for a rule where the services column is populated rather than set to any?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey Chris,
Thats correct, its exactly the same.
Best,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To confirm the blades are enabled in the gateway object itself, what about for a rule where the destination is ' Internet' ?
(Your post already indicates you checked the policy layer/package editor blades portion)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, blades are enabled. Its same issue even where Internet is the dst object. Literally, no matter what rule swe try this on, result is always the same.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
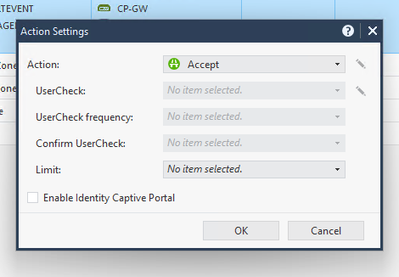
Compare the user check settings under the fw gateway object in smart console.
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for that @Lesley , I was going to do that tomorrow as the next step, as I cant think of anything else that might be missing.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
An actual screenshot from their environment might help.
You should also check the blades enabled in the relevant policy layer as that will impact what shows in the Track column.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, will get that tomorrow.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As @PhoneBoy suggested these options will be shown only if the Layer Editor has Applications & URL Filtering or Content Awareness enabled.
With just Firewall there is no need for them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@the_rock I thought from your original post you had checked this part already, please confirm when able. 🙂
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, thats the first thing I checked 🙂
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All the heavy cannons are here gladly helping=)
Since everyone wrote the answer, I will just add that enabling APPI/URLF as part of the policy is not enough in case of inline layer inside the policy. So if the client is missing those action, maybe the inline layer is not defined as APPI/URLF.
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey @Amir_Senn
Thanks for your input, always appreciated man! Hey, thinking about all this, I truly believe that what @Lesley said makes most sense to me, so will verify that with the customer today and update you guys.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
UC is on the GW side, the option to mark this is related to policy package. I managed to see the desired actions without any UC blades.
If UC definitions were the way to go it means by removing specific blades it will change setting on policy / make it invalid.
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, I see what you mean @Amir_Senn , thats also totally logical. But then Im not sure at all why customer does not see them, as their policy editor layer settings are EXACTLY SAME as mine.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One additional question for you, if you dont mind, please. So, customer mentioned to me last week and I cant for the life of me find where to do this in smart console or if its even possible. I found below thread, but dont believe its what they need.
Any idea? Essentially, say they want to block IP 10.10.10.50 (just as an example) to ONLY be able to access certain thing internally 100 times in 1 hour, thats it.
Possible?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
mmm.... not sure if this is the best solution (IDK the IPS attached) but probably possible with SmartEvent correlated event or even newer and better - Playblocks.
Kind regards, Amir Senn
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
k thank you!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hey gents @Lesley @Amir_Senn @Chris_Atkinson @Tal_Paz-Fridman @PhoneBoy
I figured it out, always learn something new every day, hehe 🙂
So, turns out their policy editor was not exactly same as mine, apologies, I missed something yesterday. Technically, if you ONLY have fw blade enabled inside policy layer, you will NOT see extra options, as I dont see them in final allow layer in my lab where I have fw blade enabled only and I do see those options in first 3 layers.
Thanks guys as always for the help and I attached few screenshots showing this.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 16 | |
| 8 | |
| 6 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter