- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Management
- :
- Re: Block Only YouTube not Google Applications
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Block Only YouTube not Google Applications
Hi Mates,
One question please, we need block only YouTube in App Control and Url Filtering.
When we try to do that via YouTube App of CheckPoint, the Block dont work becouse Google Service is allow.
When we block Google Service, these Block Gmail and other Google Applications.
The last rule is Allow All and we are not using HTTPs Inspection.
MGMT is 80.10 and Firewall are 77.30.
Do you have any idea how to get to this solution ?
Thanks
Labels
- Labels:
-
SmartConsole
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to use HTTPS Inspection.
Google uses a wildcard certificate for many of their properties.
This makes it difficult to differentiate between them without using HTTPS Inspection.
If you use HTTPS Inspection, you can differentiate between these services and enforce the desired policy.
21 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to use HTTPS Inspection.
Google uses a wildcard certificate for many of their properties.
This makes it difficult to differentiate between them without using HTTPS Inspection.
If you use HTTPS Inspection, you can differentiate between these services and enforce the desired policy.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok I understand, HTTPs inspection is necessary but the FW are in HA (Active/StandBy), so what would be the best way to have Check Point Certificates? I mean, if we created each certificate in each FW that would not be a problem when the FW failover?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a single Certificate Authority for both gateways in the cluster, which your clients will need to be configured to trust.
This can either be an internal CA or can come from your existing enterprise CA.
Gateways generate the necessary certificates on the fly signed with this CA key as sites are visited.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dameon,
For the FW is clear now but we have too Server Management in HA (Active/Standby), when the StandBy take control What would be the recommendation with the certificate?
Many thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The CA used for HTTPS Inspection is just like any other configuration: synced between management members.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As far as I know you can put in your own trusted intermediate CA certificate in there for HTTPS inspection.
And you can use it on all gateways if you like.
<< We make miracles happen while you wait. The impossible jobs take just a wee bit longer. >>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi everyone,
I'm new in old question. When we start https inspection on for youtube, yes it blocks the connections but cannot redirect to block notification and it's a problem. Cause this time, clients start to call you about the web site failure instead that they knew they're blocked. Is there a way to resolve that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It does look like you are not inspecting HTTPS.
Are you sure it is configured properly, certificate is distributed to the clients' PCs and that the sites in question are not in bypass?
Additionally, I would recommend blocking QUIC protocol outright high-up in your access control policy in order to avoid side channel bypass of calls made by some of the browsers at some of the sites that will elude the HTTPS inspection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The only way you get the block page is to enable HTTPS Inspection.
Otherwise, it is not possible to inject the block page.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm really thankful you both Vladimir Yakovlev and Dameon Welch Abernathy for accurate answers and guidance.
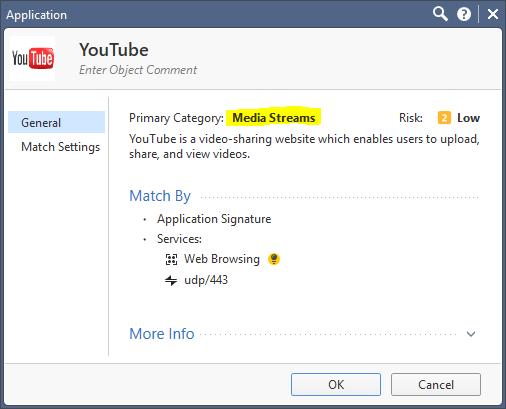
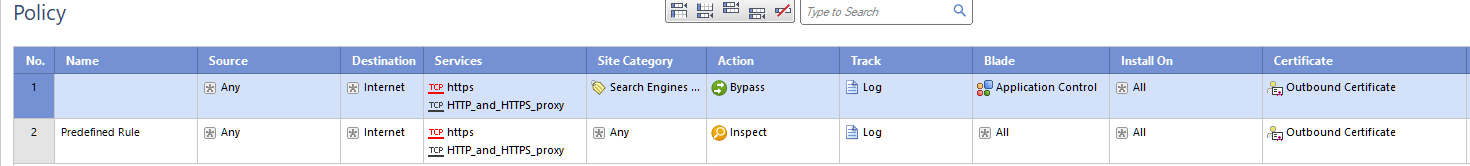
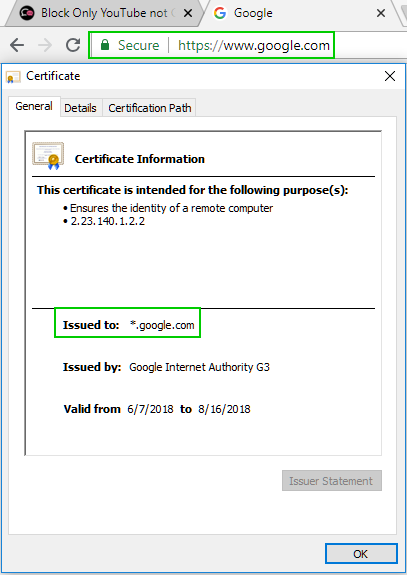
Unfortunately I do inspect youtube int HTTPS inspection as you see my policy rule below. But I think the problem is again the certificate which both google search and youtube are using the same.
In my case Google Search is not in bypass rule but the Youtube is. So, somehow GW is messing up when the URL is youtube.com and the certificate is Google. But when I start the inspect both (which is totally stupidity to inspect google search or search engines category) everything works fine. I tried to prevent the problem and "redirection" to work properly by adding a custom rule that contains all youtube URLs just before the bypass cleanup rule but again no success, cause I think the HTTPS bypass inspection is working before the URL inspection.
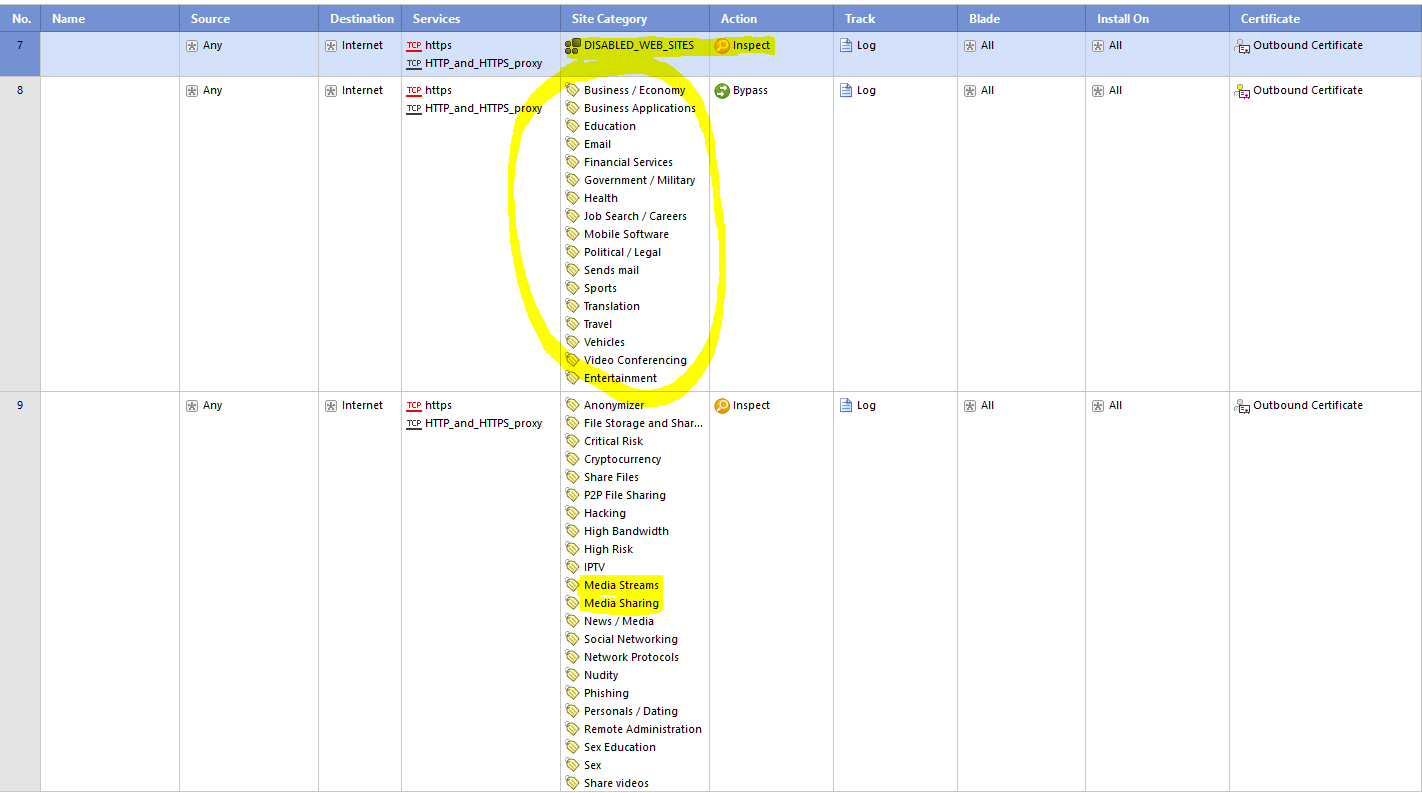


This is a difficult situation:
cause according the my HTTPS inspection rule base;
1) Google Search or Search Engines category are both NOT in bypass rule which is 8th in my rule base.
2) Media Streams that includes Youtube IS INSPECTED by rule number 9
3) Rest is bypassed by CLEANUP RULE number 10
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The HTTPS Inspection policy only supports URL Filtering categories.
It does not support App Control categories or custom ones.
Which means your Rule 1 has no effect.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May be it makes sense to restrict the use of the objects that shall not be used in the context of the dashboard?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, the fact those objects are allowed to be used in SmartDashboard is...problematic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would you mind passing it onto R&D?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sure Tomer Sole is paying attention to this thread ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Vladimir,
I put that rule -just in case- and thought maybe it works. But apparently not ! ![]()
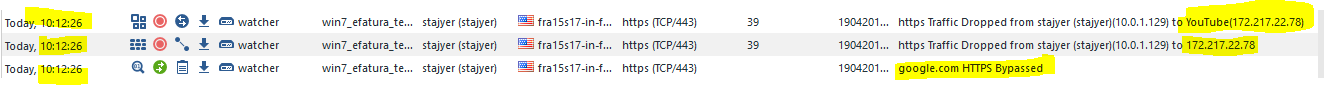
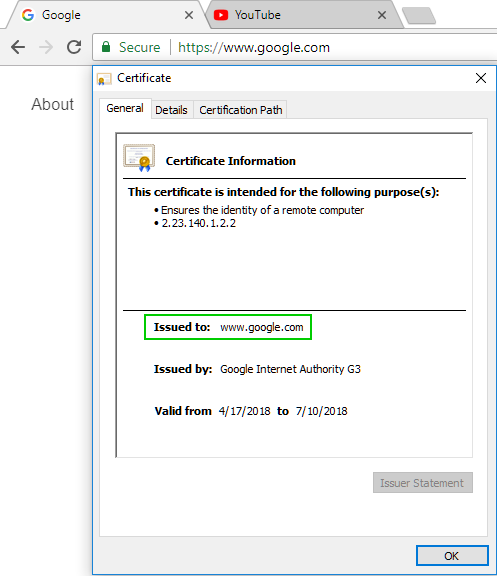
I deleted rule 7 and replaced the inspection rule 9 (now 8) with bypass rule 8(now 7), nothing changed. https://www.youtube.com/ is still recognized as google.com and bypassed due to CLEANUP Rule 9 by HTTPS Inspection.
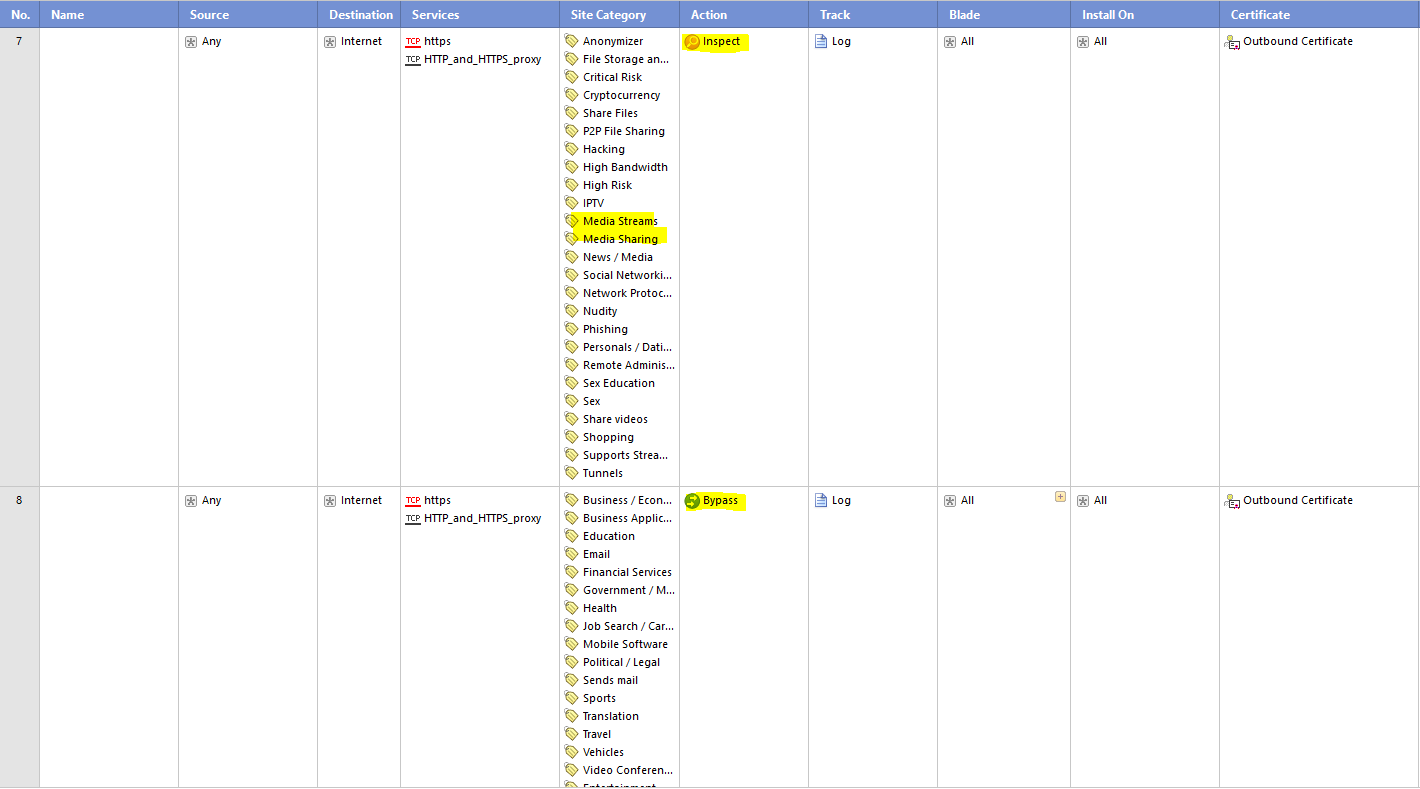


It keeps creating https bypass and Application Control drop logs in an endless loop, cause it does not redirect to the block page and end the connection:

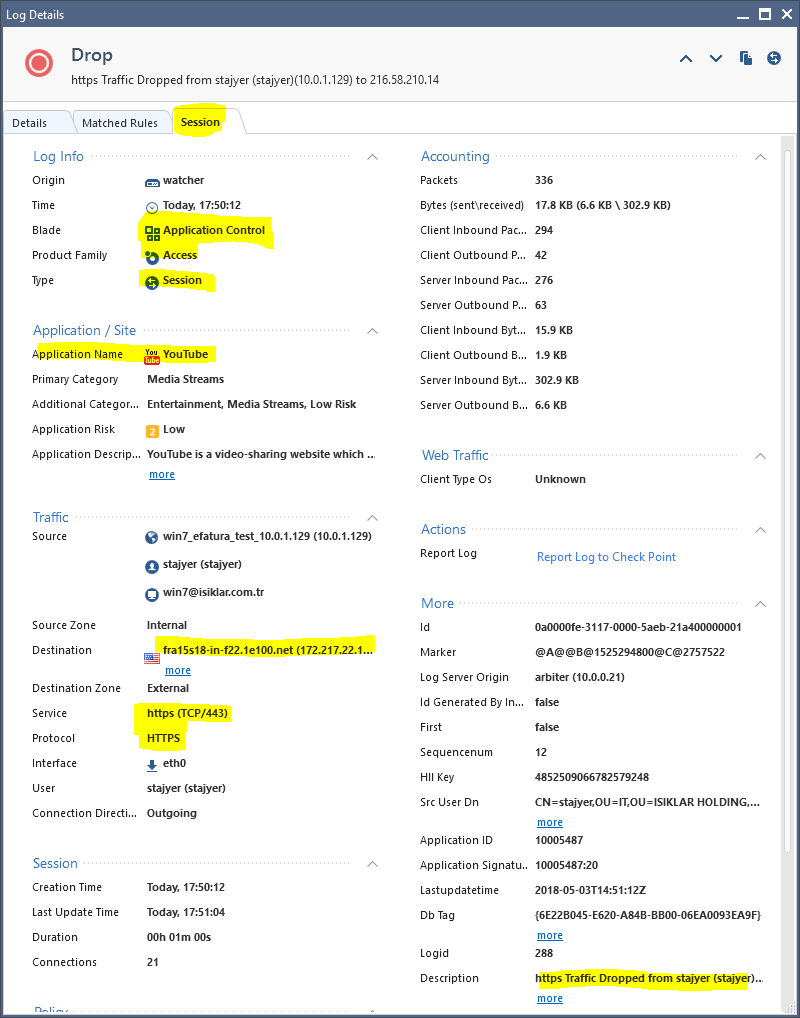
Browser snapshot is much more funny:
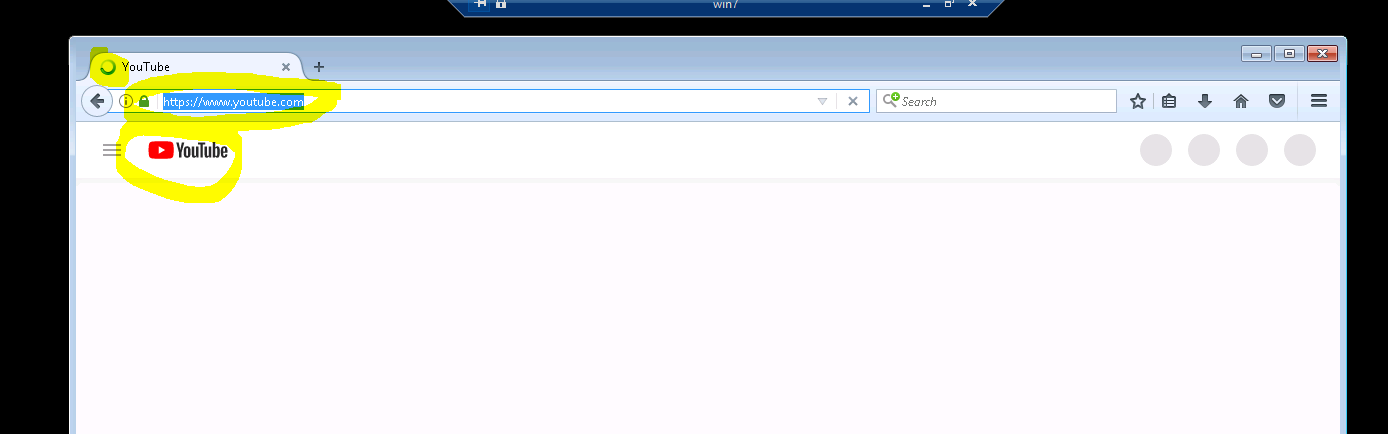
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you post the screenshot of the actual access control policy segment that controls access to these applications?
We are looking at the inspection and bypass rules of the HTTPS policy, but I have no idea what the rules that are trying to enforce the access actually are.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Works perfectly fine if:
1. You are inspecting all traffic
2. You are blocking access to youtube in your Access Policy rules
3. You have ICA certificate installed on your PC to get the UserCheck page displayed correctly

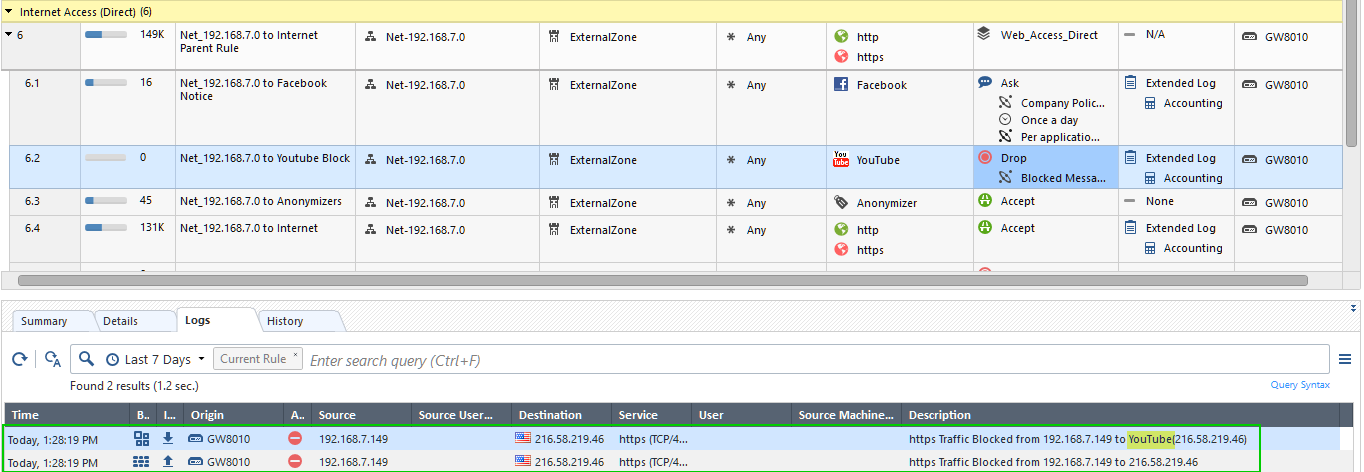
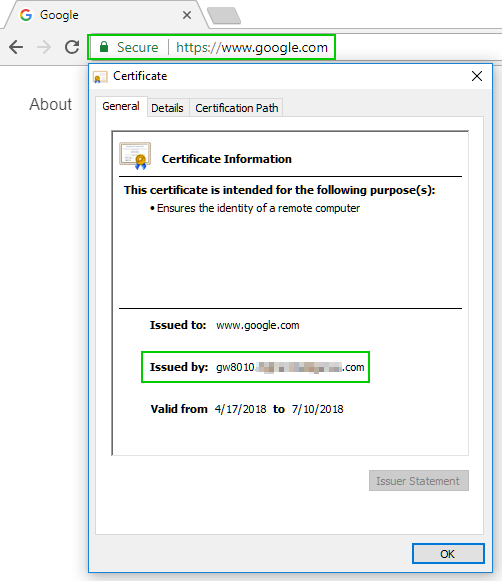
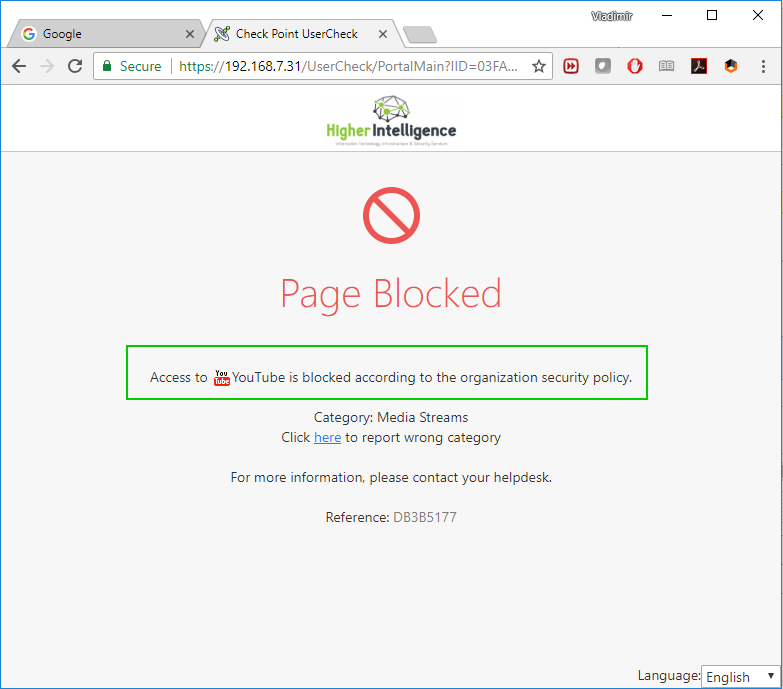
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
With bypass for search engines configured in HTTPS, I am seeing same thing as you are:
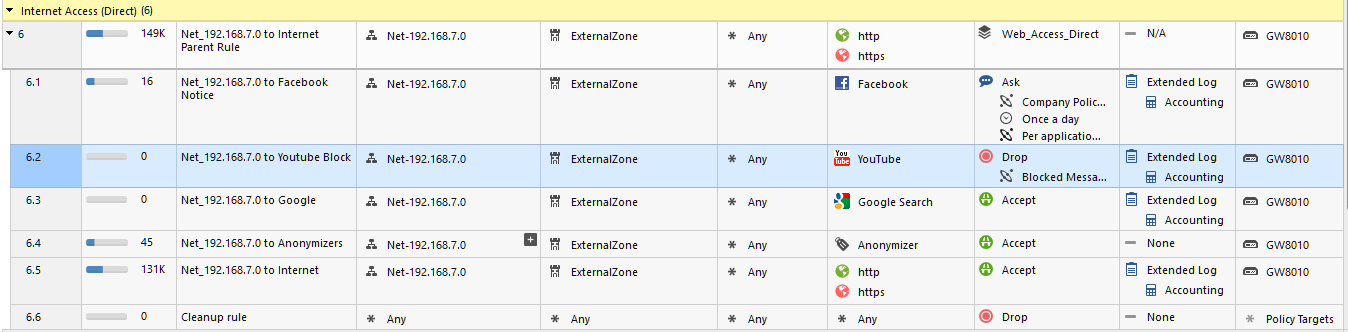
With connection being dropped without UserCheck:
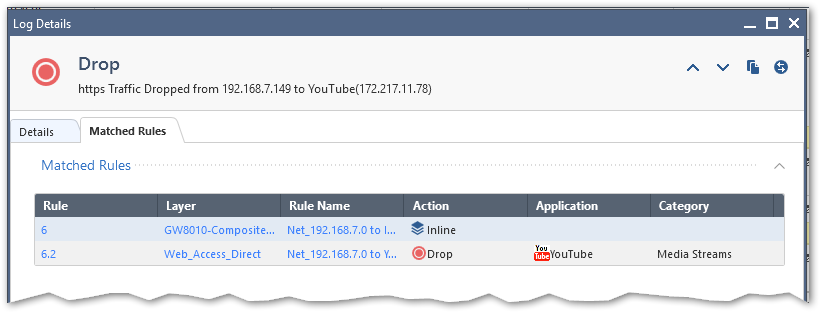
And the difference in logs looking like this:

The green section was block with redirect (no bypass).
The red section is block with No UserCheck (bypass for search engines with Application Control Blade in HTTPS inspection policy).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Vladimir thank you a lot for paying much attention. I'm glad someone came to my conclusion at last...
The point is:
If you inspect All Traffic or Search Engines (so google.com can be included) (to do so are both madness according to my opinion!) you may block and redirect youtube requests.
If you DO NOT inspect All Traffic or Search Engines (so google.com can be included) you may block youtube (with tens of logs per connection) but impossible to redirect to block page.
SO,
Isn't there a way to work this on. I mean inspecting Search Engines or All Traffic must not be the one and only way to do so...
I really appreciate for your time and interest on this matter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Evren,
Generally speaking you do want to inspect majority of the traffic, search engines included.
It only makes sense to exclude categories due to legal requirements, (i.e. banking, healthcare), trusted software update services and the sites that are broken by inspection.
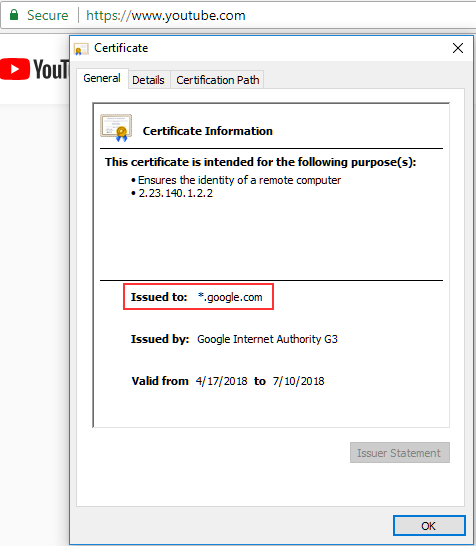
Because Google using a wildcard certificate for all of its services, you cannot differentiate the context before decryption:
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 23 | |
| 15 | |
| 13 | |
| 6 | |
| 6 | |
| 5 | |
| 5 | |
| 5 | |
| 4 | |
| 4 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


