In recent years, I have repeatedly noticed confusion regarding the following terms: KSFW, USFW, UPPAK, and KPPAK, which sometimes led to incorrect modules being switched. Therefore, I’ve written a short summary that may help you identify which firewall modules are currently active and how you can switch between them.
SecureXL Performance Pack
|
|
SecureXL is a software acceleration product installed on Security Gateways. SecureXL network acceleration techniques deliver wire-speed performance for Security Gateways. Performance Pack is a software acceleration product installed on Security Gateways. Performance Pack uses SecureXL technology and other innovative network acceleration techniques to deliver wire-speed performance for Security Gateways. SecureXL is implemented either in software or in hardware.
|
| UPPAK - User Space Performance Pack |
SecureXL runs as processes in the user space. This mode increases performance and unlocks more advanced features in SecureXL. This is the default mode on the supported Check Point appliances after you install R81.20 Jumbo Hotfix Accumulator Take 38 or above.
|
| KPPAK - Kernel Space Performance Pack |
SecureXL runs as a kernel module in the kernel space.
|
CoreXL Firewall instances
|
CoreXL is a performance-enhancing technology for Security Gateways on multi-CPU-core processing platforms. CoreXL enhances Security Gateway performance by enabling the processing CPU cores to concurrently perform multiple tasks.
CoreXL provides almost linear scalability of performance, according to the number of processing CPU cores on a single machine. The increase in performance is achieved without requiring any changes to management or to network topology.
On a Security Gateway with CoreXL enabled, the Firewall instance is replicated multiple times. Each replicated copy, or FW instance, runs on one processing CPU core. These FW instances handle traffic concurrently, and each FW instance is a complete and independent FW inspection.
|
| USFW - User Space Firewall |
|
User Space Firewall (USFW) is the infrastructure in which CoreXL Firewall instances run in the user space. This mode is available from R80.30 with Gaia kernel 3.10.
|
| KSFW - Kernel Space Firewall |
|
Kernel Space Firewall (KSFW) is the infrastructure in which CoreXLClosed Firewall instances run in the kernel.
|
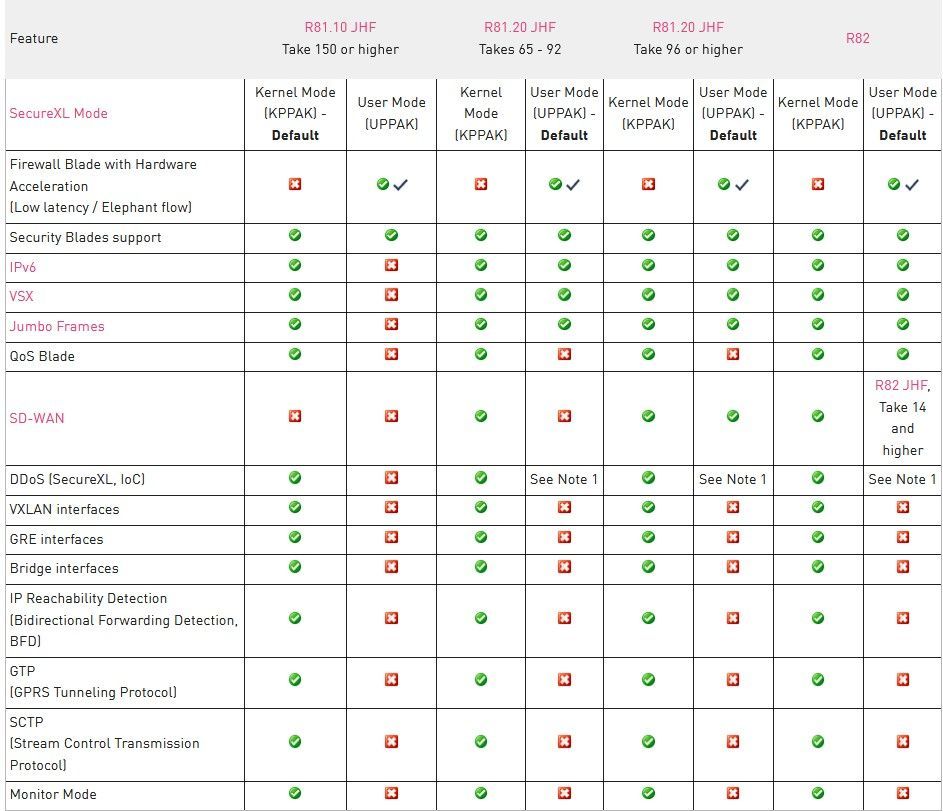
Only the following combinations are supported.
This sk179432 explains that there is a functional difference between UPPAK and KPPAK modes. Therefore, when switching between them, it’s important to carefully review the features currently in use on the firewall to ensure compatibility and avoid any unexpected behavior.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips




