- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Required Rules for Gateway and SMS? Implied Ru...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Required Rules for Gateway and SMS? Implied Rules Question.
Hey all, we have a Smart-1 appliance/2 SG 6000 appliances clustered.
Our system has been updated at least twice from older hardware with existing rules.
Looking over a few rules, I'd like to clean our rules up to what is necessary to unify sec/app layer.
Are there any articles for what is needed to for the management and security gateways on R81.10?
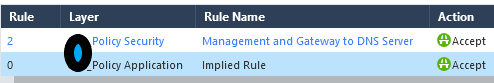
For example, I'm looking at deleting a rule 2 for our SMS/SGs (Source) -> Internal DNS Servers (Destination) / udp&tcp 53 ->Accept.
Logs for that rule look like this. Rule 0 under a different layer is saying its Implied.
I've disabled Rule 2, but wondering now I'm wondering if I move to a unified layer and delete the Application layer will DNS stop working? If a log exists lists an rule 0 - Implied Rule, would that be safe to determine we do not need a rule (after verifying logs are not hitting any other rules of course).
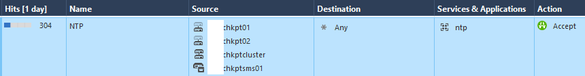
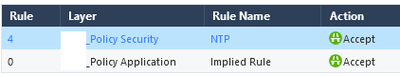
Another log example. Would this be safe to determine to delete if it is implied? I'm not seeing a difference between my Security/App layer Implied Rules. (I'm not sure if they're the same or not?)
If you have any Policy cleanup tips that would be great too. I have rules that are too permissive that I'd like to clean up to have our network more secure.
Thanks!!
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
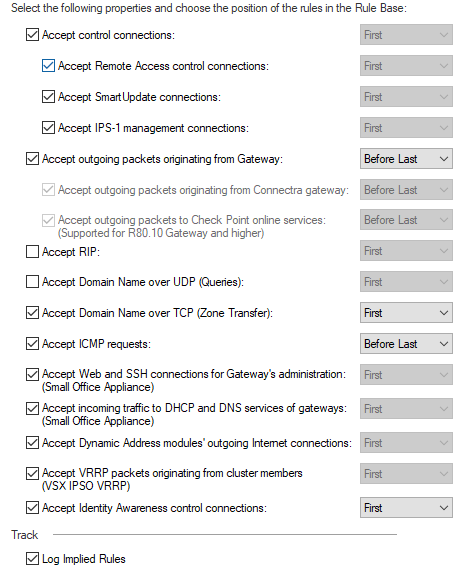
All of the Implied Rules should be shown here.
See also: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
DNS has implied rules.
NTP is not covered under Implied Rules (at least the ones shown here).
However, if traffic were purely being accepted based on these implied rules, it would be accepted that way for both layers.
Which means...this "Implied Rule" is probably something different.
I'm assuming your Application layer only has App Control/URL Filtering active and not Firewall?
That might be the reason for the implied rule as DNS and NTP are handled in the Firewall, not App Control.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Below post should be helpful:
Now, you cant disable any implied rules from GUI (as you should NOT anyway), but you can modify based on below (if need be)
As far as rules cleanup, I would look for disabled/0 hits rules and take care of those.
Cheers,
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Andy. That thread was helpful.
DO you know if there is Gateway & SMS -to-> External requirements like NTP/DNS/CheckPoint Updates KB?
Can't seem to find the article.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
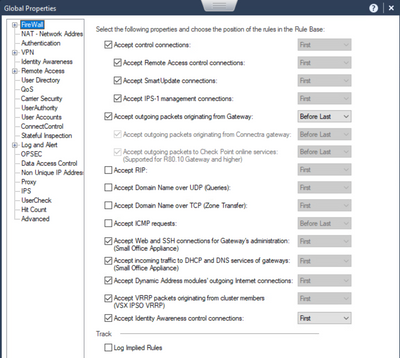
Not sure if below is what you need, but this is the only one I know of. Now, this is ONLY needed if you disable option in global properties as indicated. I personally never in 15 years dealing with CP met or talked to anyone who did this, but, in all fairness, with much better handling of updatable objects, I guess it might not be so unusual to see customers do it now days.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for this. I wonder if at one point we that did have unchecked, and whoever administrated the FW at the time created explicit rules for updates.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Most likely, you must have, because Im 99.99% sure the only time anyone would have explicit rules for updates in the policy would have been if that option in global properties was off.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Unless there is a serious security based argument, I would advise you to keep the default implied rules.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Val,
I'm not interested in modifying the implied rules. I'm trying to understand them since we have rules created that seem like they are already covered under the Implied Rules. Duplicate rules?
Like if we have a rule for CheckPoint updates to 'x' destination. Is that necessary if I see logs below that rule that it is implied?
Hope I am explaining that right.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
All of the Implied Rules should be shown here.
See also: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
DNS has implied rules.
NTP is not covered under Implied Rules (at least the ones shown here).
However, if traffic were purely being accepted based on these implied rules, it would be accepted that way for both layers.
Which means...this "Implied Rule" is probably something different.
I'm assuming your Application layer only has App Control/URL Filtering active and not Firewall?
That might be the reason for the implied rule as DNS and NTP are handled in the Firewall, not App Control.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks PhoneBoy. I'll go over that article as well.
You are correct! That makes sense to me, I THINK.
--
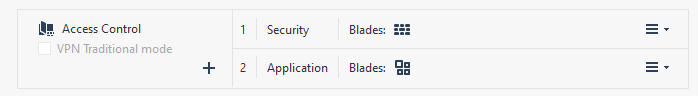
I'm assuming it is required to have the Security layer enabled with Application & URL Filtering in order to achieve a unified policy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In a Unified Policy, you'd have a single layer with the relevant blades enabled (Firewall and App Control in this case).
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 14 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter