- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Facing weird issue with Route based tunnels an...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Facing weird issue with Route based tunnels and traffic is getting dropped
Hello,
This is again I stuck in same issue and not sure how to troubleshoot. I built a VTI tunnel and traffic is getting dropped with below messages.
I turned off
vpn accel
fwaccel off
disabled few parameters with fw ctl set int but in vain.
Any idea how do I handle this?
PPAK 0: Get before set operation succeeded of simple_debug_filter_off
[Expert@LPCPNETCORE-FW:0]# fw ctl zdebug + drop | grep 10.255.255.1
@;3131804750;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_2];[fw4_1];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_3];[fw4_0];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_2];[fw4_1];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
@;3131804750;[cpu_1];[fw4_2];fw_log_drop_ex: Packet proto=1
10.255.255.1:476 -> 192.168.2.7:0 dropped by fw_send_log_drop Reason:
Rulebase drop - dropped due to 'drop optimization';
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
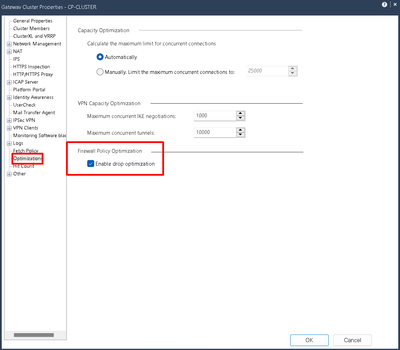
Not sure if it could be related, but maybe check below settings. If its enabled, maybe disable it and install the policy to see if it changes the behavior.
Andy
[Expert@CP-gw:0]# fw ctl get int fwkern_optimize_drops_support
fwkern_optimize_drops_support = 1
[Expert@CP-gw:0]#
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nah man - That is already done but no luck.
Drop Optimization is not enabled. In fact you and I had a previous thread on similar topic, eventually it ended or resolved on it own 😞
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One thing I find odd from the drops is that it keeps saying rulebase drop, yet, there is no rule mentioned. 192.168.2.7, thats host on the other end?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm sounds to me like the firewall expired or has otherwise lost state for the existing ICMP "connection" between 10.255.255.1 and 192.168.2.7, which was probably initiated by 192.168.2.7, However 10.255.255.1 does not know this and is still trying to use the dead connection to send replies. Because it does not match anything in the state table, a rulebase lookup occurs and column-based matching has thrown out all possible rules with an accept action thus leaving only drops, and does not bother to figure out which rule will drop it to save resources as it doesn't matter anyway, since I suspect 10.255.255.1 is not allowed to initiate pings to 192.168.2.7.
fw ctl conntab | grep 10.255.255.1 can be used to see the current idle timer for that ICMP "connection", if Aggressive Aging is enabled the connection may get expired early if the firewall is running short of resources.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well forgot to mention or not sure if that would be useful. 10.255.255.1 is a tunnel interface of peer and I have 10.255.255.2.
192.168.2.7 is my lan server. And they are initiating a connection from that peer hence 10.255.255.1 which is an egress interface of that device is being used and those are the packets getting originated from the peer.
Thats a good insight and let me try looking
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Whats the other side? AWS, Azure?
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nope a SDWAN router from versa.
Thanks and Regards,
Blason R
CCSA,CCSE,CCCS
Blason R
CCSA,CCSE,CCCS
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 10 | |
| 10 | |
| 9 | |
| 6 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter