- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Enable FIPS mode
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Enable FIPS mode
I have searched all over and have found no information on how to enable FIPS mode. Needing to do some testing but can't find documentation on how to enable it.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here you can find it, a switch called called ext_fips: sk98252: List of Role-Based Access features in Gaia OS
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
62 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here you can find it, a switch called called ext_fips: sk98252: List of Role-Based Access features in Gaia OS
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here an older discussion with more information: FIPS mode operation and some manual configurations
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not very clear what to look for in that article once you are in /bin and check fips file...if you search for ext_fips, does not find anything.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
no none of it is very clear. I did find the switch to turn it on, but this was very obscure when trying to hunt it all down.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Agree 100%.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Did you read FIPS mode operation and some manual configurations ?
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have been looking through that Doc yes. Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the problem I think that is still happening is that when FIPS mode is enabled on the gateway the management station immediately loses connectivity to the gateway. This is what appears to be very poorly documented as to how to complete the full configuration and keep communication established to the gateways from the management server once fips mode is turned on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I guess I can't say it loses all connectivity. SIC claims that it is still communicating. but policy can no longer be installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
please take this with TAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I can confirm that when I run 'fips on' in an R81.20/R81.10 environment, I do NOT lose SIC connectivity on the gateways.
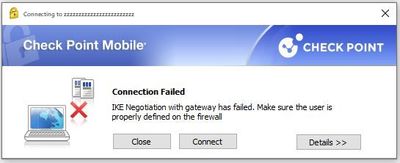
I do lose the WebUI (443 or 4434), SSH, SSL VPN (SSL VPN works), and remote access IPSEC VPN (see screenshot).
However I can still install policy on the gateways in FIPS mode.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Whats the command you ran to enable it? I want to try it in the lab tomorrow.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
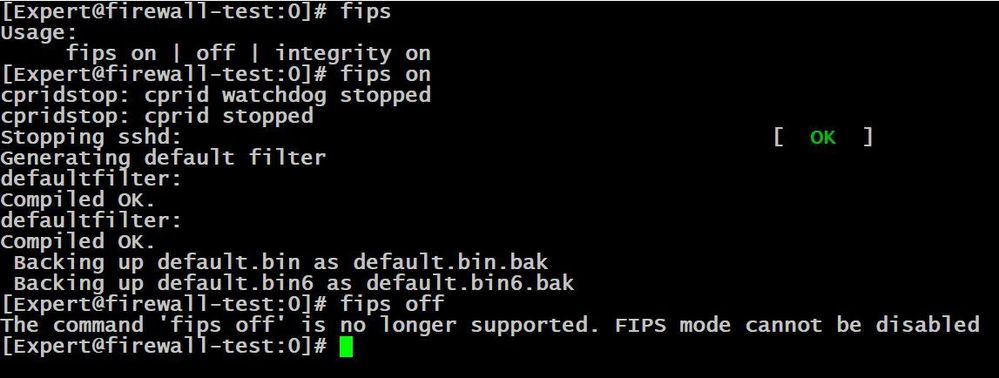
I ran just the basic 'fips on'. BTW make sure to snapshot the image, because 'fips off' is no longer supported (despite what the documentation might say). You will not be able to back out of FIPS once you enable it on the gateway.
Or
[Expert@firewall-test:0]# fips
Usage:
fips on | off | integrity on
[Expert@firewall-test:0]# fips on
cpridstop: cprid watchdog stopped
cpridstop: cprid stopped
Stopping sshd: [ OK ]
Generating default filter
defaultfilter:
Compiled OK.
defaultfilter:
Compiled OK.
Backing up default.bin as default.bin.bak
Backing up default.bin6 as default.bin6.bak
[Expert@firewall-test:0]# fips off
The command 'fips off' is no longer supported. FIPS mode cannot be disabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wow, thats crazy. Ok, I got lots of R81.20 lab fws, so will try on one tomorrow and update.
Thank you!
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yup, got EXACT same result...wow, thats truly disappointing. I hope it gets changed at some point.
Andy
[Expert@CP-TEST-ONLY-FW:0]# fips on
cpridstop: cprid watchdog stopped
cpridstop: cprid stopped
Stopping sshd: [ OK ]
Generating default filter
defaultfilter:
Compiled OK.
defaultfilter:
Compiled OK.
Backing up default.bin as default.bin.bak
Backing up default.bin6 as default.bin6.bak
initial_module:
Compiled OK.
initial_module:
Compiled OK.
[Expert@CP-TEST-ONLY-FW:0]# fips off
.bash_history .bash_profile .clish_history 1
.bash_logout .bashrc .toprc last_dump.log
[Expert@CP-TEST-ONLY-FW:0]# fips off
The command 'fips off' is no longer supported. FIPS mode cannot be disabled
[Expert@CP-TEST-ONLY-FW:0]#
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Btw, if you want couple minutes, web UI does come back.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I corrected my post above. After running 'fips on'
- SSL VPN portal page does come up and allows login
- SSH: disabled (expected)
- GAIA WebGUI on 4434: disabled (expected)
- Check Point Mobile client sees "Ike negotiation with gateway failed" (not expected)
- Site-to-site VPN not tested yet
Lab Environment:
R81.20 SMS w Jumbo 10
R81.10 gateway w Jumbo 110
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are my results on R81.20 jumbo 26:
web UI on port 443 failed initially after enabling FIPS, but then worked 2 mins later
ssh failed
S2S failed
AFTER reboot web UI also failed.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you still have a problem with remote access please open a ticket. That way it will be looked at. If it was resolved, please report here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yep, I opened a ticket last week. Support was able to confirm the IKE issue for the Check Point Mobile client once 'fips on' is run. I will post here if there is a fix.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please keep us posted.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks, can you share the reference?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Instructions for enabling FIPS mode are included in the Security Policy that is published by NIST under the certification listing together with the certification certificate https://csrc.nist.gov/projects/cryptographic-module-validation-program/certificate/4264
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In my mind, if fips can be enabled, option should be there to disable it...lol
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Features are disabled by enabling FIPS mode. In R80 there was “fips off” that was set a value registry. Changing the value (from on) is not enough to enable all the features. It it not a supported feature.
We plan to enable SSH and WebUI in FIPS mode limited to using the FIPS approved ciphers. Maybe this will answer why you wish to disable FIPS mode?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is my HONEST feedback
Fips gets disabled, features dont work...ok, fine, not perfect, but I guess thats expected
Fips can NOT be re-enabled...I find that odd and in my mind, that should be FIXED 🙂
Cheers mate.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think you mean when fips mode is enabled, features are disabled and this is sort of fine.
What you are asking for is a way to back-out so the fips mode can be disabled.
What is the reason why you want to disable fips mode? Will enabling use of webui and ssh in fips mode help?
Technically fips mode is defined in the registry, but there are also changes in setting fips mode that may not be reversed if only the registry entry is changed. There are also considerations regarding the ability to create keys when not in fips mode as they may not be fips compliant. When not in fips mode non-approved cyphers are available, and the default is not to use fips approved entropy. KAT tests also operate differently when not in fips mode, and that could be a problem. Not having fips off removes these and maybe other considerations.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, put yourself in customers' place for a second. IF you enable a feature and you dont like it, would you not want to have an option to disable it? : - )
Anyway, you pretty much got exactly what I was implicating...
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have not provided the need for a customer to disable fips mode.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 15 | |
| 11 | |
| 6 | |
| 3 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 2 | |
| 2 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter