Hi @Dale_Lobb,
Active Streaming (CPAS) - Check Point Active Streaming active streaming allow the changing of data, we play the role of “man in the middle”. CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.).
General overview:
- CPAS breaks the connection into two parts using our own stack – this mean, we are responsible for all the stack work (dealing with options, retransmissions, timers etc.)
- An application is register to CPAS when a connection start and supply callbacks for event handler and read handler.
- On each packet, CPAS send the application the packet data with cpas_read, allow the application to change the data as it like, and send the data forward with cpas_write.
- CPAS server side stack negotiates the TLS version with the web server. If the highest version of TLS 1.3 is used by the web server, CPAS will try to negotiate a lower TLS version for example TLS 1.2 or TLS 1.1 if the Web server supports this.
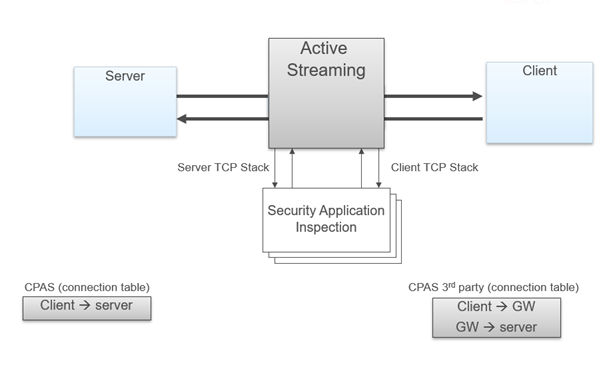
Active Streaming – https content step by step:
Packets of SSL handshake are passed to the SSL engine to exchange keys. When the connection and the SSL handshake is fully established, an hook will be register for this connection to handle the decrypt / encrypt of the packets. When a packet arrive to CPAS, a trap will be sent and the SSL engine will receive the encrypted packet, decode the packet and return it to CPAS. The packet will enter the receive queue and the application will be able to work on it, once he done he will send it to the write queue. The packet will pass to the SSL engine for encryption and pass to the other side (Client, Server).
More read here:
R80.x - Security Gateway Architecture (Content Inspection)
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips



