- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- General Topics
- :
- Re: Any workaround for this
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any workaround for this
Currently our Guestnet (for Wifi) cannot stops people from accessing “naughty” HTTPS websites because the checkpoint can’t decrypt the outbound HTTPS traffic from non-corporate devices.
Is there any way to get around this problem? As manually forcing guest users to install our Checkpoint certificate is not feasible / not enforceable, what other options do we have? (reading my mind out aloud, if we upgrade our GWs to R80.20, will SNI fix / bypass this issue so the URL inspection / categorization can be used?)
Cheers,
Hunt
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Either upgrade to R80.20 with the recent JHF that has the SNI fix or use R80.30+ which also includes it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Adding to what PhoneBoy wrote you can also refer to sk163594 - What's new in HTTPS Inspection starting from R80.20:
"Starting in R80.20 and R80.30 latest Jumbo Hotfix Accumulators, HTTPS Inspection offers important new features in the domains of security and usability.
To take advantage of these new capabilities, upgrade to R80.20 Jumbo Hotfix Accumulator Take 118 (and higher), or R80.30 Jumbo Hotfix Accumulator Take 111 (and higher)."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hunt_Lee,
you're right, as @PhoneBoy mentioned SNI with URL-Filter is your solution without HTTPS-inspection.
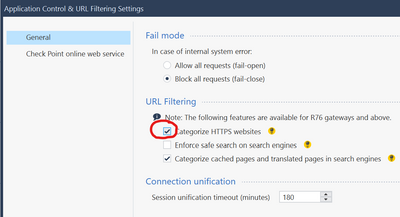
Don't forget to enable "categorize HTTPS websites"
Wolfgang
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
If i install a public CA certificate (e.g. Verisign, GoDaddy) onto my CheckPoint, and change all the outbound rules to used this new certificate for outbound traffic.
Would then my guest users traffic be able to be inspected by CheckPoint? Or would they still need to install this CA certificate manually by themselves (which is not enforceable).
Cheers,
Hunt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, that's possible. If you use an SUB-CA issued from a root CA which is trusted by your client devices everything would be fine.
Any certificate issued from a trusted CA or trusted sub CA will be trusted on you clients. All depends on the trusted root CAs on your clients. You can use the defaults from Windows, Linux, MACs, Android, IOS etc. already installed on your clients or you can install your own. But with your own you have to touch these devices.
Wolfgang.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No globally trusted Certificate Authority would issue you a sub-CA for this purpose.
Any time such certificates do manage to get out in the wild, they tend to get banned fairly quickly and generate bad press for the organizations involved.
Any time such certificates do manage to get out in the wild, they tend to get banned fairly quickly and generate bad press for the organizations involved.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No Verisign or GoDaddy alike company will give you a Sub CA as that would mean you do not need them anymore to generate certificates.
Most often used Sub-CA is from a Microsoft Certificate server. All Windows machines that trust your AD will also trust that Certificate.
The Guest users still need to trust your AD - CA, or you need to bypass their traffic from HTTPS decryption, based on source network.
Most often used Sub-CA is from a Microsoft Certificate server. All Windows machines that trust your AD will also trust that Certificate.
The Guest users still need to trust your AD - CA, or you need to bypass their traffic from HTTPS decryption, based on source network.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
If i have a *.mycompany.com.au certificate issued by Digicert, can i use this certificate as wouldn't the public users trusted the cert issued by a CA like Digicert?
Cheers,
Hunt
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The certificate used must be a Certificate Authority certificate capable of signing certificates.
What you have is a wildcard certificate, which cannot be used for outbound HTTPS Inspection.
What you have is a wildcard certificate, which cannot be used for outbound HTTPS Inspection.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hunt,
I very much apologize for misunderstanding my writing. Yes, the guys here are really right, you can't by such SUB-CA.
I have one customer they did this, but they are the owner of one of these Root-CAs.
As @PhoneBoy and @Maarten_Sjouw mentioned you have to follow their suggestions and implement your owned Sub-CA.
Wolfgang
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 17 | |
| 10 | |
| 10 | |
| 8 | |
| 7 | |
| 3 | |
| 2 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter