- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Port scan from external network
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
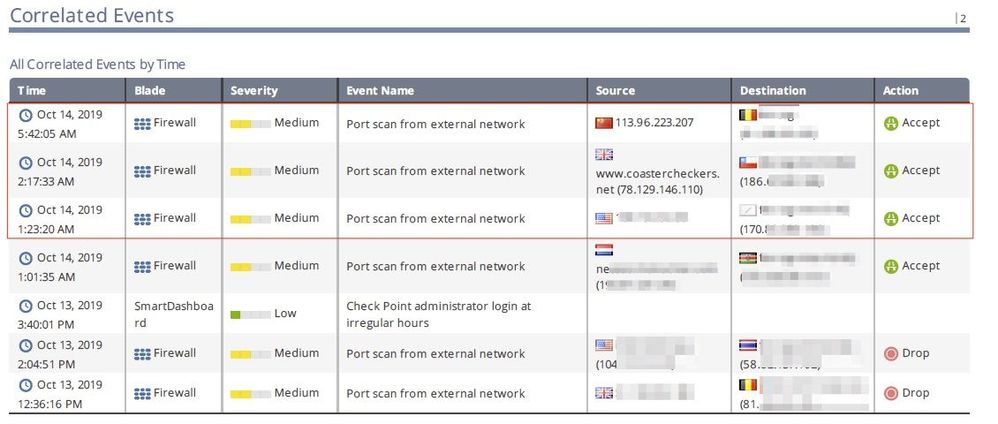
Port scan from external network
Hi guys,
We received this from our regular Global Correlated Events report and curious how to prevent the Port scan from external network. The action is Accepted and we'd like to know where to adjust this? I know this activity is very risky as obviously the source is suspicious.
Is there any way I can monitor in live the possible similar Event name?
Appreciate your idea where and how to adjust and prevent this? Thanks in advance.
Cheers!
Darius
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Theo,
IPS collects statistics on how many inactive ports were accessed during a given time. For example, if IPS detects a client attempting to access a hundred different inactive ports within a 30 second time frame, IPS will recognize this behavior as a port scan attack. It will then log the event, or notify you (depending on the Action you select in this page).
Enable IPS protection "Host Port Scan" to detect port scan on R80.X:
1) In SmartConsole under Security Policy tab, go to the Threat Prevention rule base.
2) On the bottom go to Threat Tool and choose IPS protection.
3) Go to the Search bar and look for Host Port Scan.
4) Edit the protection and choose the right Profile of the Firewall
5) Edit the profile and set the Logging setting from Log to User Alert according to the User Alert configured in the General Properties.
1) In SmartDashboard/SmartConsole, go to Policy menu - click on Global Properties...
2) Expand Log and Alerts - click on Alerts
3) Check the box Run UserDefined script (under Send user defined alert no.1 to SmartView Monitor)
4) Add an automatic SAM rule:
sam_alert -t 120 -I -src
This will set an automatic SAM rule (for all Security Gateways managed by this Security Management Server / Domain Management Server) with the Source IP address of the host that caused a hit on the IPS protection "Host Port Scan" during 120 seconds.
5) Click on OK to apply the changes
Now configure the Security Gateways to send Alerts and install policy:
1) Configure the Security Gateways to send Alerts to the Security Management Server / Multi-Domain Management server per sk114630.
2) Install policy on all managed Security Gateways.
3) Connect with SmartView Monitor to Security Management Server / Domain Management Server - go to Tools menu - click on Alerts....
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can find this within the IPS Protection settings. There, just search for: Port Scan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Danny,
Do you have idea how to prevent this? I noticed many attempts of Port scan from external network have "Accept" actions in our different gateways/site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Theo,
IPS collects statistics on how many inactive ports were accessed during a given time. For example, if IPS detects a client attempting to access a hundred different inactive ports within a 30 second time frame, IPS will recognize this behavior as a port scan attack. It will then log the event, or notify you (depending on the Action you select in this page).
Enable IPS protection "Host Port Scan" to detect port scan on R80.X:
1) In SmartConsole under Security Policy tab, go to the Threat Prevention rule base.
2) On the bottom go to Threat Tool and choose IPS protection.
3) Go to the Search bar and look for Host Port Scan.
4) Edit the protection and choose the right Profile of the Firewall
5) Edit the profile and set the Logging setting from Log to User Alert according to the User Alert configured in the General Properties.
1) In SmartDashboard/SmartConsole, go to Policy menu - click on Global Properties...
2) Expand Log and Alerts - click on Alerts
3) Check the box Run UserDefined script (under Send user defined alert no.1 to SmartView Monitor)
4) Add an automatic SAM rule:
sam_alert -t 120 -I -src
This will set an automatic SAM rule (for all Security Gateways managed by this Security Management Server / Domain Management Server) with the Source IP address of the host that caused a hit on the IPS protection "Host Port Scan" during 120 seconds.
5) Click on OK to apply the changes
Now configure the Security Gateways to send Alerts and install policy:
1) Configure the Security Gateways to send Alerts to the Security Management Server / Multi-Domain Management server per sk114630.
2) Install policy on all managed Security Gateways.
3) Connect with SmartView Monitor to Security Management Server / Domain Management Server - go to Tools menu - click on Alerts....
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Heiko,
We have implemented this exactly as described to the SK. We are Using R80.40.
But the only thing that happens is that the event is now displayed as an alarm.
The command in Global Properties does not seem to be executed.
If i check that with:
[Expert@cp-fw-01:0]# fw sam_policy get -l | grep 94.102.x.x
[Expert@cp-fw-01:0]# // there is no answer
Maybe you have a idea why sam_alert is not working ?
I am new with checkpoint and i will be very grateful for hints.
Best Regards
Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Heiko,
not working by us. We have executed as described in the SK, but the scan is not blocked.
Scan is showing as Alert but no prevention.
fw sam_policy get | grep <scanIP> will also not found in SAM.
Have you got a idea why it is not working or how i can troubleshoot this ?
Sorry but i am a newbie with checkpoint.
Many Thanks
Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Curious if you have found a solution to this issue ? I am about to implement it myself but it is same, i see the alerts but no blocking.
Br, Rickard
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hallo Durin,
be us this behaviour has been changed since we have disabled the hidden Member function.
"This is new with R80.40"
[Expert@admin]# fw ctl get int fwha_cluster_hide_active_only,
It should return with the value "1"
We had open a Ticket by CheckPoint regarding a other case, but since we have disabled this function,
the script "sam_alert -t 120 -I -src" was working now.
After some tests... shows that is not a good Solution, behause it is poorly controllable. All your Alerts where be handelt by
block with the SAM rule.
Now we working with the Thread-Policy -> This is accessible in "Logs and Monitor" -> in the left lower corner ->
there is "external Apps" and there is "Smart Event Settings and Policy"
There you can define the internal Network, with a Group Object and you can define some actions.
(quite far down ) on the left side you will see the "attacks" . There it is now possible to assign the generated actions.
(More as one is possible, for exempel: Email information and block session)
From my point of view, it's good that I don't have to block the whole IP, but only the "attack-action" with this IP.
(in case of false positive, mybe a customer will have a own test 🙂 )
Please Note: after the upgrade to R80.40, this feature was also no longer running by us for whatever reason,
so i have said, after we have disabled the hidden Member, is is running and the scan`s are prevented now.
Best Regards
Thomas
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Would it be possible to use the securexl ddos penalty box at "global settings - run userdefined script" instead of the sam rules for port-scan protection?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
Anybody can check Host port scan , we're using R81 the Action just have Accept and Inactive . Didnot have DROP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Port/Host Scan is informational only feature. It counts certain amount of connection attempts to previously unused IPs and ports.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
we have solved this regarding we use "Prevention Policy"! There is a point scan from internel and external and there you can put a drop statment and a time event. (exampl. drop for 120min)
You can find the policy in Smart Console/Logging -> left lower corner.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I had also set "scan" and "ip sweep" protection in Smartevent with automatic reaction "block IP", but i had to remove these protections.We are using R80.40.
I had more than one hundred IP to block. With 12 SG, this means more than 1 thousand sam rules in smartevent. "fwd" process goes to 100% on the management server (smart1-3050), so the SG where not able to send all their logs to the management, so they start logging locally and we were missing logs. the standy management server (without smartevent) is also affected (fwd at 100%) because the SG are not able to send their logs.... "fwd" looks to be single threaded, it's a big problem !
After some tests, with 100 sam rules, fwd jumps to 50-60%. Without sam rules fwd is at 2-5%
It would be more efficient to use the penalty box, but there is no way to set a timeout.
"scan" and "ip sweep" are really effective for us to block hundreds/thousands of packets per second. i think i will have work on a script to block them with a timeout in the penalty box.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I got this enabled on our R80.40 cluster, we enabled it since R80.20 and upgrades seem to have not affected it, in our logs I can see its creating SAM rules works fine.
following this guide
only thing I wanted to know how to change was from reject to drop ? don't seem to be able to find the option.
also is the a way to get smartevent report for just the SAM rule, I tried playing with some settings but can't seem to get it to report on it. - worked it out have to use host scan in the report that shows up and can schedule it now.
Thanks
Frank
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter