- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: Is it possible to block by User Agent or Clien...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
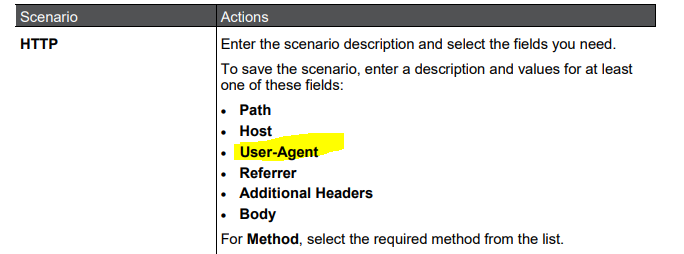
Is it possible to block by User Agent or Client Type?
We see requests going through our Checkpoint firewall from various Client Types e.g:
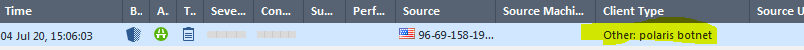
Other: polaris botnet
Other: Abbyy.Internet
Example log:
We wonder if it's possible to block by User Agent or Client Type.
Any ideas?
We are on 80.30 with all features except DLP and Threat Extraction/Emulation
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
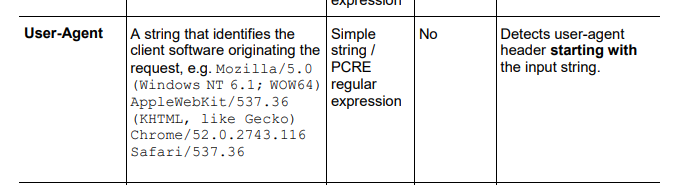
Should not have additional performance impact (the user-agent inspected already as its displayed in your log), I didn't try OR command, but PCRE have it (maybe best to try in lab 1st)
In your screenshot IPS was already triggered on this traffic, depends on the signature, its worth to set it on prevent (or detect at first to understand which additional traffic falls under it) - this might be the simplest way for your end goal.
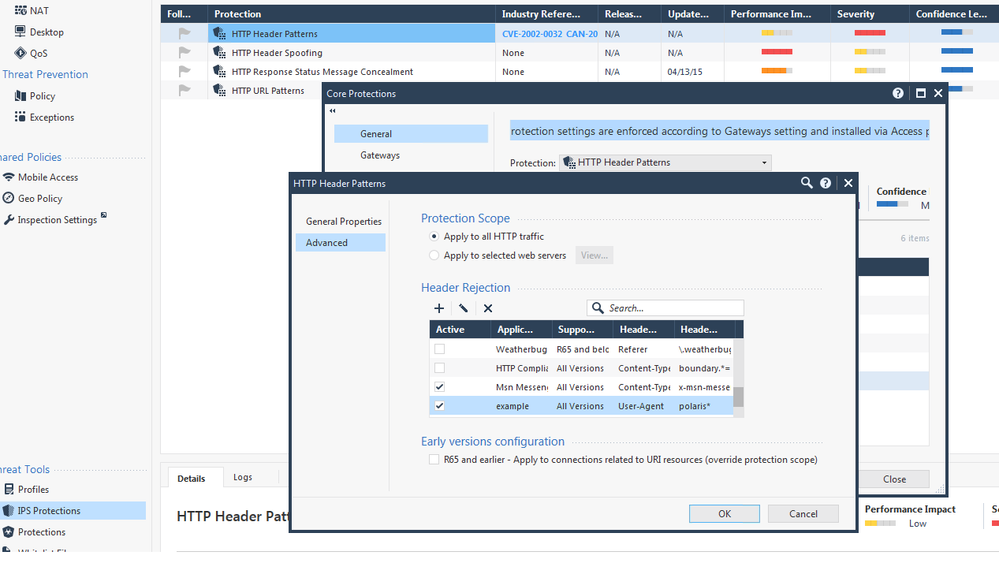
btw, IPS have ability to reject traffic by specific header too as below:
hth,
Roman.
7 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
There is built in application for verity of browsers that can be used in the rule base as additional ordered layer of parent rule for inline layer, as result you can allow/block specific Browsers and still maintain general control of other apps.
For generic/custom user-agents its possible to create custom app with a defined specific user-agent.
For custom app, use the Signature Tool for custom Application and URL. (sk103051)
Kind regards,
Roman.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks!
Will use the signature tool for this.
Just wondering whether this is CPU intensive as I wanted to block several User Agents.
Also, any idea on how I can use OR statement to add multiple User Agents in one custom signature? I am not familiar with PCRE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should not have additional performance impact (the user-agent inspected already as its displayed in your log), I didn't try OR command, but PCRE have it (maybe best to try in lab 1st)
In your screenshot IPS was already triggered on this traffic, depends on the signature, its worth to set it on prevent (or detect at first to understand which additional traffic falls under it) - this might be the simplest way for your end goal.
btw, IPS have ability to reject traffic by specific header too as below:
hth,
Roman.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, this is great.
For some reason I couldn't get it to work using IPS headers. Will check out more on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A couple notes about these IPS protections:
1. They are "Core" protections, meaning changes to them require an Access Policy installation instead of a Threat Prevention policy installation.
2. These protections may not work with HTTPS traffic, even if HTTPS Inspection is enabled (at least as reported by the community).
Might be better to use the Application Control Signature Tool instead if that's the case.
1. They are "Core" protections, meaning changes to them require an Access Policy installation instead of a Threat Prevention policy installation.
2. These protections may not work with HTTPS traffic, even if HTTPS Inspection is enabled (at least as reported by the community).
Might be better to use the Application Control Signature Tool instead if that's the case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have been toying a bit with client types for blocking unwanted bits of traffic and potential malware for http/https traffic to the internet. Here is what my rule looks like:
As you can see I tried a 'drop what doesn't match' type rule, so I have negated what I wish to allow to drop everything else. 'Good client types' are applications I have created based on User-Agent, some windows BITS and other agents for windows CRL checks etc.
Things I've noticed:
1) Traffic that is bypassed by HTTPs inspection doesn't match the rule and gets dropped, so Categories like 'Financial Services' and 'override categorization' sites need to be allowed before this rule.
2) Traffic that doesn't contain User-Agent header or that Checkpoint can't determine a client type for, gets dropped.
I spent quite a bit of time checking to see whether this kind of approach would work ok in a user to internet type environment, but unfortunately I have a feeling I will need to drop the User Agent approach for filtering noise and malware. The biggest issue I find is with allowing traffic that doesn't carry a User Agent header, or that Checkpoint can't locate client type for.
If anyone has attempted anything like the above can they advise on their approach?
Thanks,
A
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Antonis,
Allowing traffic solely by user-agent is a very strict/limiting approach. this is mostly used to Block specific user agents.
Kind regards,
Roma.
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter