- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: IPS: Connection accepted - But why?
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
IPS: Connection accepted - But why?
Hi all,
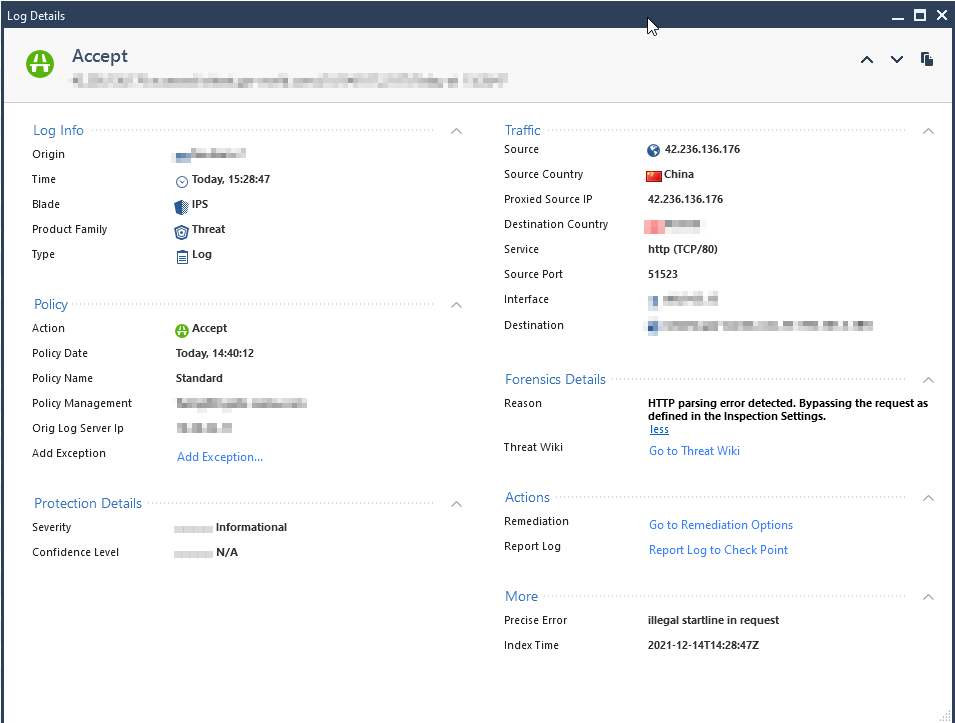
I'm trying to find out why the connection below is accepted. Forensic reason is "HTTP parsing error detected. Bypassing the request as defined in the Inspection Settings." Precise Error is "illegal startline in request"
I'm not able to add an exception -> "This protection does not support exceptions"
The inspection setting "Non compliant HTTP" is set to inactive.
Thread Prevention blade is set to Fail-open. Could this be the cause?
Running on 80.40
Any ideas welcome
Kind regards
Oliver
Labels
- Labels:
-
IPS
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
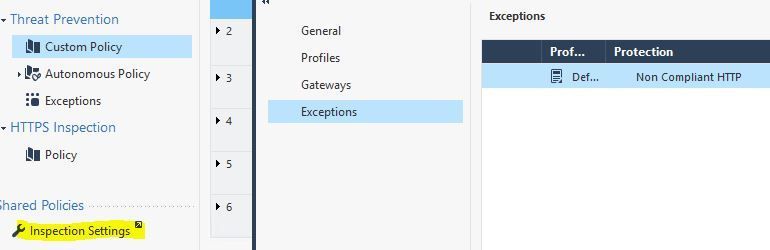
It's a bit confusing but this protection isn't directly from the IPS protections but from the general "Inspection Settings". You can add exceptions there. But keep in mind that you would have to enable this protection first and add exception for the connections you might need:
We also have it disabled as it is standard in the default profile.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Marcel,
confusing is the right word 🙂 As I've already mentioned in my post: Non compliant HTTP is already set to inactive. So why should this setting generate the log entry?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Inactive actually doesn't mean it won't be logged - this is the same behavior with regular IPS exceptions. I honestly don't know what's the difference between detect and inactive but normally you have to also set the log column no "none" in order to do nothing. As you cannot do that with those inspection settings you would have to live with that I assume.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There are four overall types of IPS-related protections that all used to be part of the IPS blade prior to R80 but got (mostly) split out separately in R80+:
1) IPS ThreatCloud Protections (shield icon)
2) Inspection Settings (wrench icon)
3) Core Activations/Protections (only 39 of these - shield w/ firewall icon)
4) Geo Policy (legacy in R81+)
Regardless of type, exceptions are processed after the actual inspection occurs looking for that protection and simply changes the final decision (Prevent/Detect/etc.). As such exceptions don't improve performance at all. The ability to specify "Inactive" in an exception is indeed misleading, it probably should be "Ignore" which would be a bit more clear and slightly different than Detect. For Inspection Settings specifically, hits against an exception there will always be logged and you can't change it. Some Inspection Settings protections are inherent to the stateful inspection process and cannot directly be set to Inactive on the protection itself, let alone an exception.
The specific log you are seeing is related to an internal inspection failure and what to do when that happens (fail open or fail closed); in your case it failed open (bypass). There is not a separate setting for Inspection Settings controlling this I'm aware of, I imagine it is keying off the Manage & Settings...Blades...Threat Prevention...Fail Mode option, even though Inspection Settings is supposed to be part of the Access Control policy. See my commentary at the start of this article.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Timothy,
thank you for clearing this up. I've already assumed that this logs are caused because of the fail-open setting. Will switch the Thread blade to fail-close and keep on monitoring.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Definitely keep an eye on things for awhile when changing from fail-open to fail-close, you may be surprised what gets broken as a result.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Seems we've been too optimistic with Fail-open / Fail-close. I've set the Thread Prevention Blade to Fail-close but these kind of logs are still being generated. Any other ideas what protection or setting causes this issue?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Probably will need a TAC case for this, as I don't see where the fail mode is controlled from for Inspection Settings, it must not be using the TP Setting.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter