There are four overall types of IPS-related protections that all used to be part of the IPS blade prior to R80 but got (mostly) split out separately in R80+:
1) IPS ThreatCloud Protections (shield icon)
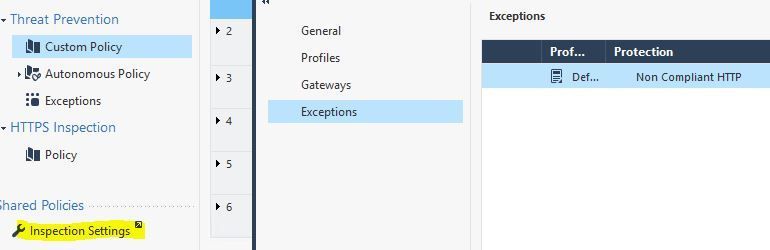
2) Inspection Settings (wrench icon)
3) Core Activations/Protections (only 39 of these - shield w/ firewall icon)
4) Geo Policy (legacy in R81+)
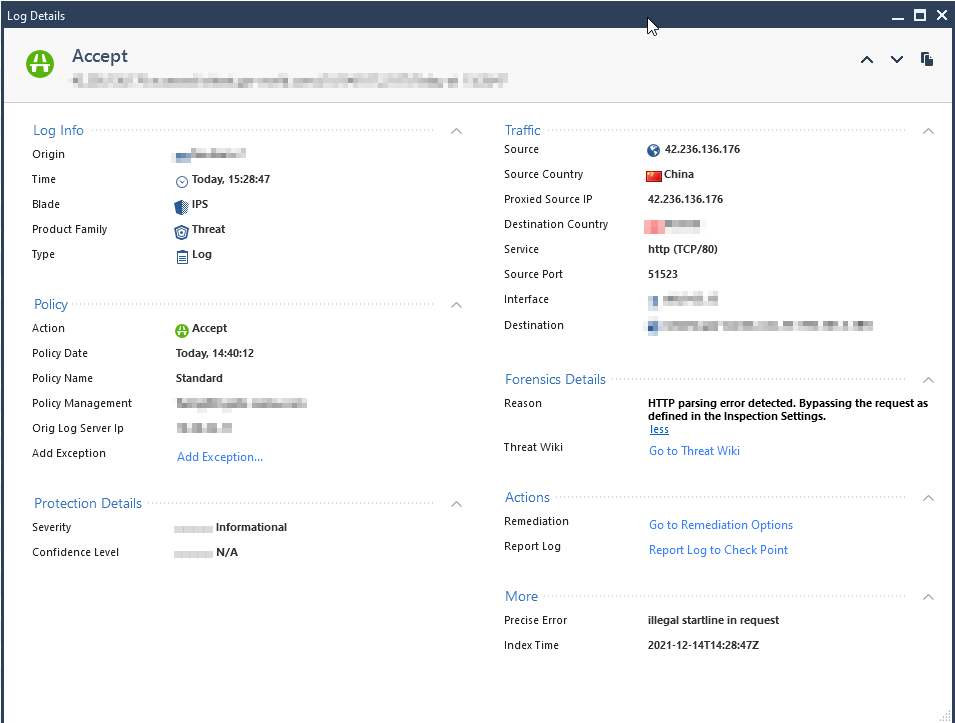
Regardless of type, exceptions are processed after the actual inspection occurs looking for that protection and simply changes the final decision (Prevent/Detect/etc.). As such exceptions don't improve performance at all. The ability to specify "Inactive" in an exception is indeed misleading, it probably should be "Ignore" which would be a bit more clear and slightly different than Detect. For Inspection Settings specifically, hits against an exception there will always be logged and you can't change it. Some Inspection Settings protections are inherent to the stateful inspection process and cannot directly be set to Inactive on the protection itself, let alone an exception.
The specific log you are seeing is related to an internal inspection failure and what to do when that happens (fail open or fail closed); in your case it failed open (bypass). There is not a separate setting for Inspection Settings controlling this I'm aware of, I imagine it is keying off the Manage & Settings...Blades...Threat Prevention...Fail Mode option, even though Inspection Settings is supposed to be part of the Access Control policy. See my commentary at the start of this article.
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course