- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SmartMove
- :
- Re: SonicWall Migration
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SonicWall Migration
Has anyone had any experience in migrating SonicWall policies into Check Point? How do this as easily as possible, and lessons learned. I understand that SmartMove will not work.
Thank you.
10 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Larry,
I have migrated configuration from SonicWalls into Check Point firewalls and the process I went through consisted of the following steps:
1) Export the configuration from the SonicWalls.
2) Break up the data into distinctive sections (i.e. policies, nat rules, objects etc.).
3) Sort out the data in Excel and save the resulting files in csv format.
4) Bulk import everything via the management api.
I can appreciate that the above list is only a "crude" way of going about it but that is the process I went through in the absence of SmartMove compatibility. I'm happy to provide you with more information about each step if you like and I would be more than happy to hear a better method to follow with regards to the migration in question.
I hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Nick,
I'm about to get involved in a similar activity, and I found this post.
I'd appreciate it if you could give a few more details, especially regarding the "breaking up the data into distinctive sections". Also if you happen to maybe have a script, in order to automate this task, it would be greatly appreciated.
Thanks a lot
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Xterminator,
Of course, no problem 🙂
May I ask what is the version of the Check Point manager and firewall you are working with?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nick, thanks for your availability. 🙂
At the moment I'm working with an R80.30 management server with a dedicated log server. It manages a VSX environment with various clusters, running the same version.
Thanks a lot,
Alessandro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
as an ex SonicWALL employee I'd say - don't do that!
I tried many times and always ended up doing things again from scratch. there is no simple path for it it is a painful way via XLS/CSV files and XLM imports. Not worth it. SMB vendors won't cope well with Enterprise one. Trust me on that!
I tried many times and always ended up doing things again from scratch. there is no simple path for it it is a painful way via XLS/CSV files and XLM imports. Not worth it. SMB vendors won't cope well with Enterprise one. Trust me on that!
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Jerry, thanks for your input. I'm not afraid to do things the "hard way": I just wanted an input on how to do this migration as better as possible, if there were an automated approach, the better 😉
Thanks and Regards,
Alessandro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi Alessandro, I was actually replying to the original post from Larry 🙂 But I do appreciate where you coming from.
Best of luck.
Best of luck.
Jerry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Alessandro,
Please find below the documentation I created and followed a while ago in order to assist a customer with their migration from a SonicWall to a Check Point estate:
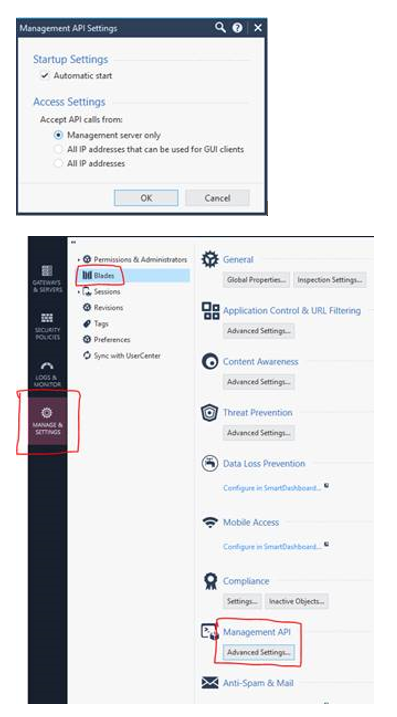
Preparing the Management API
Since the bulk of the migration will be carried out via Check Point’s api, the status of the api console will need to be confirmed.
1) Connect to the command line of the SMS (Security Management Server).
2) Log in to Expert mode.
3) [Expert@HostName]# api status (it should say “API readiness test SUCCESSFUL”).
4) Ensure that the machine you have accessed the SMS from is a trusted client by navigating to Manage & Settings >> Blades >> Management API >> Management API Settings and select the appropriate option followed by “OK”.
5) Ensure that there are no other api tasks currently running to avoid any conflicts by running the command below:
[Expert@HostName]# mgmt_cli -r true show tasks status "in-progress" (it should say “total:0”).
Transferring the Migrated Data
With a tool such as WinSCP, please transfer the CSV files provided to the Security Management Server.
Importing the Objects
To import the objects, please run the following commands in the order written below:
[Expert@HostName]# mgmt_cli add host --batch host-objects.csv
[Expert@HostName]# mgmt_cli add network --batch network-objects.csv
[Expert@HostName]# mgmt_cli add security-zone --batch security-zones.csv
[Expert@HostName]# mgtmt_cli add address-range --batch address-range-objects.csv
[Expert@HostName]# mgmt_cli add group --batch group-objects.csv
[Expert@HostName]# mgmt_cli add service-tcp --batch service-objects.csv
Importing the Firewall Policy
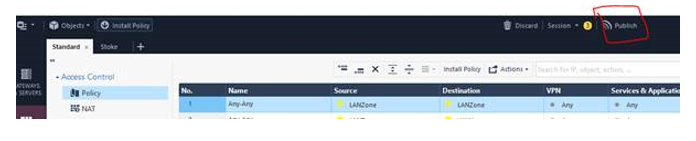
It is important to note that the previous commands must not return any errors during the import process. Any errors encountered have to be addressed before proceeding further as the firewall policies will not be imported successfully. To that end, please publish the changes now:
Assuming the previous steps have been followed without any issues, please run the following command:
[Expert@HostName]# mgmt_cli add access-rule –batch firewall-policy.csv
Importing the NAT Policy
[Expert@HostName]# mgmt_cli add nat-rule –batch nat-policies.csv
Creating the RemoteSite Policy Package
[Expert@HostName]# mgmt_cli add package name "RemoteSite"
Importing the RemoteSite Objects
[Expert@HostName]# mgmt_cli add host --batch host-objects-rs.csv
[Expert@HostName]# mgmt_cli add network --batch network-objects-rs.csv
[Expert@HostName]# mgtm_cli add address-range --batch address-range-objects-rs.csv
[Expert@HostName]# mgmt_cli add group --batch group-objects-rs.csv
[Expert@HostName]# mgmt_cli add service-tcp --batch service-group-objects-rs.csv
Importing the RemoteSite Firewall Policy
It is important to note that the previous commands must not return any errors during the import process. Any errors encountered have to be addressed before proceeding further as the firewall policies will not be imported successfully. To that end, please publish the changes now:
[Expert@HostName]# mgmt_cli add access-rule –batch firewall-policy-rs.csv
Importing the RemoteSite NAT Policy
[Expert@HostName]# mgmt_cli add nat-rule –batch nat-policies-rs.csv
Migrating Interfaces
SonicWall interfaces begin with the 'X' character in their names. To make the migration possible, the 'X' character has been replaced with Check Point's counterpart naming convention (eth) across all data.
1) Connect to the command line of the GW.
2) Log in to Expert mode.
3) Transfer the headoffice-interfaces file provided to the GW.
4) Convert the transferred plain-text file from DOS format to UNIX format:
[Expert@HostName]# dos2unix /some_path_to/file_with_configuration
5) Import the configuration from the plain-text file:
[Expert@HostName]# clish -s -f /some_path_to/file_with_configuration
6) List the interfaces configuration:
[Expert@HostName]# clish -c "show configuration interface"
7) Save the configuration:
[Expert@HostName]# clish -c "save config"
Post-Migration Tasks
1) Change the port numbers and protocol types of all custom services. Based on the data provided, it was unknown what port number and what protocol type (tcp, udp, etc.) each service was initially associated with.
2) Since the migrated rule bases are based on Security Zones, the workflow below will have to be followed from Step 2 onwards:
- Define Security Zone objects. Or, use the predefined Security Zones.
- Assign Gateway interfaces to Security Zones.
- Use the Security Zone objects in the Source and Destination of a rule. For example:
Source | Destination | VPN | Service | Action |
|
InternalZone | ExternalZone | Any Traffic | Any | Accept |
|
3) Based on the data provided, it was unclear for us to determine which firewall rules in particular should have logging enabled. As such, ALL firewall rules will have logging enabled.
4) Based on the data provided, it was unclear which services should be members of the service groups involved. As such, all service groups should be checked and populated correctly.
5) Identify which objects have not been migrated (if any).
Troubleshooting
Should you encounter any errors while trying to execute one of the api commands, please re-direct the output to a text file.
For instance, if you get an error when running the command below,
[Expert@HostName]# mgmt_cli add service-tcp --batch service-group-objects.csv
Run it again like so:
[Expert@HostName]# mgmt_cli add service-tcp --batch service-group-objects.csv > errors.txt
And then provide us with the errors.txt file.
References
https://sc1.checkpoint.com/documents/latest/APIs/index.html#introduction~v1.1%20
I hope this helps.
Let me know if you have any questions.
Nick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nick,
Thanks so much for your explanation and your level of detail, which I appreciate a lot. Luckily, having the APIs at my disposal makes the job A LOT easier 🙂
A couple more questions, if it's not too much to ask:
1) I see that during the imports of the objects/rulesets a CSV file is being used, but do you have a hint on how to generate this file?
I extracted a XML file from the SonicWall firewall, which appears to contain all the objects and rulesets (from the "Diagnostics"/"Download Report" section): may I work starting from this file? From this, I believe I could create a script which isolates all objects, networks, rulesets, etc...
2) Maybe it's a trivial question (if so, sorry for asking), but what is the point of importing the objects, groups, services, etc... 2 times into the management server? (one of them is listed as RemoteSite).
Thanks a lot again for all your effort,
Alessandro
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Nick. I am currently working on a similar migration. Your steps make sense, but I would like to know if it would be possible to obtain the scripts you used to generate the various CSVs. Thank you for your assistance.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 7 | |
| 4 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter