Hi Alessandro,
Please find below the documentation I created and followed a while ago in order to assist a customer with their migration from a SonicWall to a Check Point estate:
Preparing the Management API
Since the bulk of the migration will be carried out via Check Point’s api, the status of the api console will need to be confirmed.
1) Connect to the command line of the SMS (Security Management Server).
2) Log in to Expert mode.
3) [Expert@HostName]# api status (it should say “API readiness test SUCCESSFUL”).
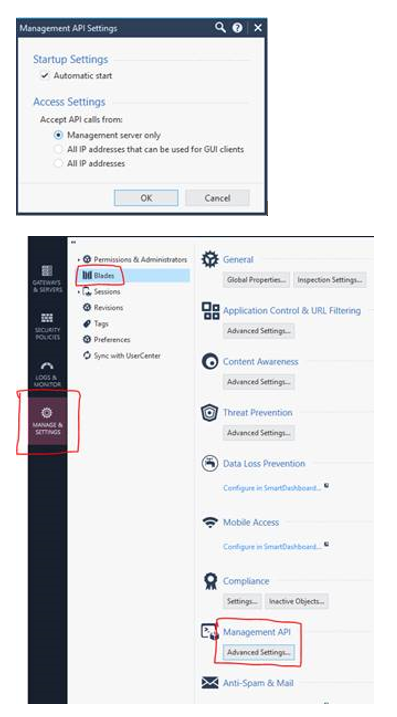
4) Ensure that the machine you have accessed the SMS from is a trusted client by navigating to Manage & Settings >> Blades >> Management API >> Management API Settings and select the appropriate option followed by “OK”.
5) Ensure that there are no other api tasks currently running to avoid any conflicts by running the command below:
[Expert@HostName]# mgmt_cli -r true show tasks status "in-progress" (it should say “total:0”).
Transferring the Migrated Data
With a tool such as WinSCP, please transfer the CSV files provided to the Security Management Server.
Importing the Objects
To import the objects, please run the following commands in the order written below:
[Expert@HostName]# mgmt_cli add host --batch host-objects.csv
[Expert@HostName]# mgmt_cli add network --batch network-objects.csv
[Expert@HostName]# mgmt_cli add security-zone --batch security-zones.csv
[Expert@HostName]# mgtmt_cli add address-range --batch address-range-objects.csv
[Expert@HostName]# mgmt_cli add group --batch group-objects.csv
[Expert@HostName]# mgmt_cli add service-tcp --batch service-objects.csv
Importing the Firewall Policy
It is important to note that the previous commands must not return any errors during the import process. Any errors encountered have to be addressed before proceeding further as the firewall policies will not be imported successfully. To that end, please publish the changes now:
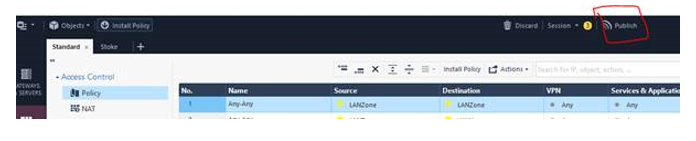
Assuming the previous steps have been followed without any issues, please run the following command:
[Expert@HostName]# mgmt_cli add access-rule –batch firewall-policy.csv
Importing the NAT Policy
[Expert@HostName]# mgmt_cli add nat-rule –batch nat-policies.csv
Creating the RemoteSite Policy Package
[Expert@HostName]# mgmt_cli add package name "RemoteSite"
Importing the RemoteSite Objects
[Expert@HostName]# mgmt_cli add host --batch host-objects-rs.csv
[Expert@HostName]# mgmt_cli add network --batch network-objects-rs.csv
[Expert@HostName]# mgtm_cli add address-range --batch address-range-objects-rs.csv
[Expert@HostName]# mgmt_cli add group --batch group-objects-rs.csv
[Expert@HostName]# mgmt_cli add service-tcp --batch service-group-objects-rs.csv
Importing the RemoteSite Firewall Policy
It is important to note that the previous commands must not return any errors during the import process. Any errors encountered have to be addressed before proceeding further as the firewall policies will not be imported successfully. To that end, please publish the changes now:
[Expert@HostName]# mgmt_cli add access-rule –batch firewall-policy-rs.csv
Importing the RemoteSite NAT Policy
[Expert@HostName]# mgmt_cli add nat-rule –batch nat-policies-rs.csv
Migrating Interfaces
SonicWall interfaces begin with the 'X' character in their names. To make the migration possible, the 'X' character has been replaced with Check Point's counterpart naming convention (eth) across all data.
1) Connect to the command line of the GW.
2) Log in to Expert mode.
3) Transfer the headoffice-interfaces file provided to the GW.
4) Convert the transferred plain-text file from DOS format to UNIX format:
[Expert@HostName]# dos2unix /some_path_to/file_with_configuration
5) Import the configuration from the plain-text file:
[Expert@HostName]# clish -s -f /some_path_to/file_with_configuration
6) List the interfaces configuration:
[Expert@HostName]# clish -c "show configuration interface"
7) Save the configuration:
[Expert@HostName]# clish -c "save config"
Post-Migration Tasks
1) Change the port numbers and protocol types of all custom services. Based on the data provided, it was unknown what port number and what protocol type (tcp, udp, etc.) each service was initially associated with.
2) Since the migrated rule bases are based on Security Zones, the workflow below will have to be followed from Step 2 onwards:
- Define Security Zone objects. Or, use the predefined Security Zones.
- Assign Gateway interfaces to Security Zones.
- Use the Security Zone objects in the Source and Destination of a rule. For example:
Source | Destination | VPN | Service | Action | |
InternalZone | ExternalZone | Any Traffic | Any | Accept | |
- Install the Access Control Policy.
3) Based on the data provided, it was unclear for us to determine which firewall rules in particular should have logging enabled. As such, ALL firewall rules will have logging enabled.
4) Based on the data provided, it was unclear which services should be members of the service groups involved. As such, all service groups should be checked and populated correctly.
5) Identify which objects have not been migrated (if any).
Troubleshooting
Should you encounter any errors while trying to execute one of the api commands, please re-direct the output to a text file.
For instance, if you get an error when running the command below,
[Expert@HostName]# mgmt_cli add service-tcp --batch service-group-objects.csv
Run it again like so:
[Expert@HostName]# mgmt_cli add service-tcp --batch service-group-objects.csv > errors.txt
And then provide us with the errors.txt file.
References
https://sc1.checkpoint.com/documents/latest/APIs/index.html#introduction~v1.1%20
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
https://sc1.checkpoint.com/documents/R80.20_GA/WebAdminGuides/EN/CP_R80.20_SecurityManagement_AdminG...
I hope this helps.
Let me know if you have any questions.
Nick




