- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- traffic doesn't go to the right interface
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
traffic doesn't go to the right interface
Hello all,
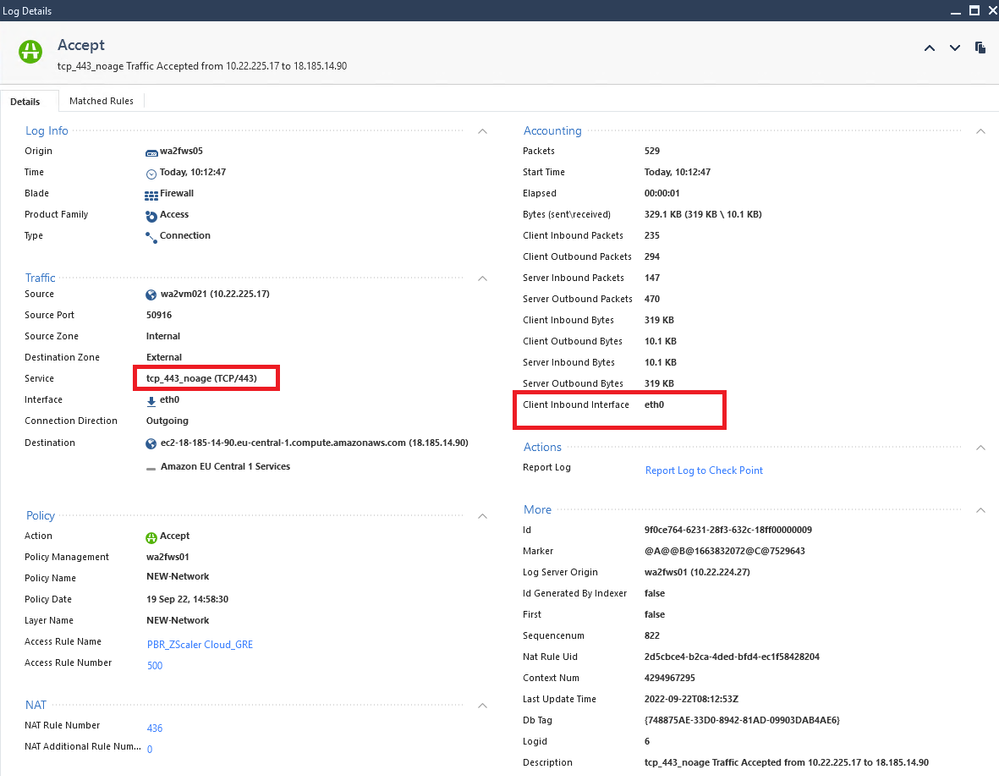
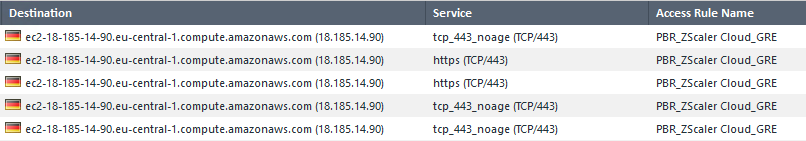
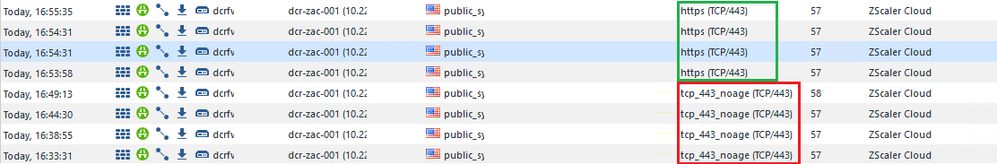
we have GW R81.10 and some PBR. We've just found that from time to time some traffic doesn't go to the right interface - GRE for Zscaler. The strange thing is that sometimes traffic goes where it should. This is a good traffic:
this is a bad traffic:
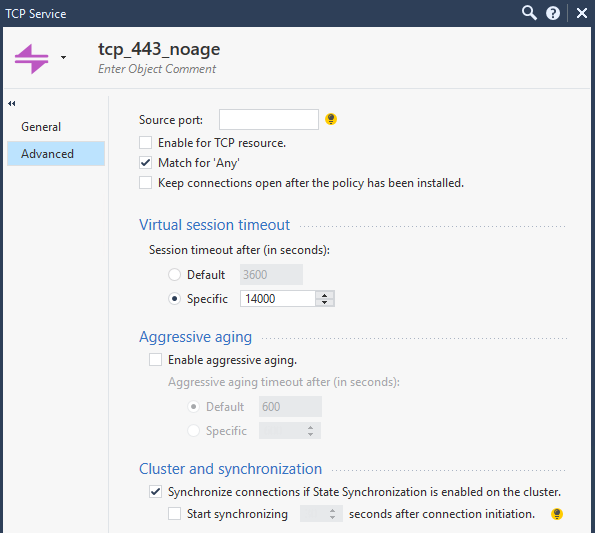
as you can see the difference is only the port definition. It is always 443, but different objects. tcp_443_noage has the following settings (unfortunately, I do not know the purpose of this object, but it is used by some rules for VMWare and veeam):
What could be wrong and how to fix it?
Thank you!
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R81.30 is not a version that exists yet, do you mean R80.30?
What do your PBR rules look like?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
it is R81.10, I've correted this information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
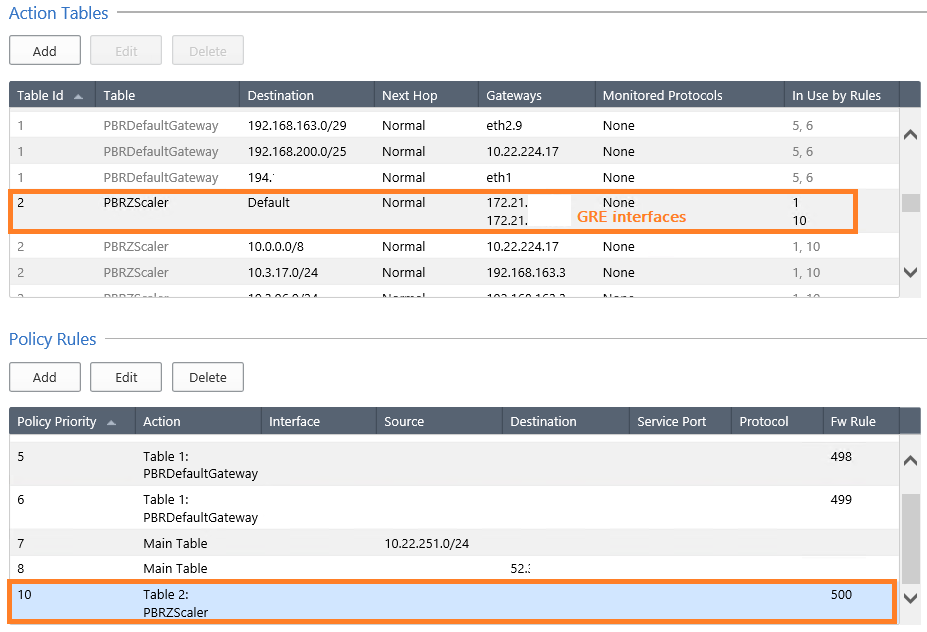
oh, I was not aware you can attach PBR table based on FW rule number. How would that work if you add another rule above and the whole thing shifts?
As per port definition, it is probably some workaround for backup team with long running backups etc. I would suggest for regular user traffic sticking with standard https object.
I believe there was major PBR redesign some time ago - at least that's what I understood from release notes. We still have some incorrectly performed routing by PBR too, but on R80.40.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
after adding a new rule the number in the PBR is also changed. And yes, this is not only one problem with PBR... We have another case with CP Support where we have workaround (adding disabled rule before impacted rule) but we can't use it in my case.
the non-standart port is not defined in the Rule for Zscaler and appears only in the logs. How FW decides which object to use?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Run ip r g and then IP address as a destination and verify it is indeed correct (from expert mode).
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
this looks good, since eth1 is the external interface through which the gre tunnel naturally goes:
ip r g 18.185.14.90
18.185.14.90 via 194.xxx.xxx.xxx dev eth1 src 194.yyy.yyy.yyy
cache
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A “different” service could be necessary if, for instance, you want certain HTTPS traffic to have a different timeout than the default.
I suspect there may be some issue with PBR, in which case you will probably need TAC assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the problem exists for a long time already. in some cases we managed to solve it, but in this case not. We have already opened a Ticket with the Support, but they havent't found a reson and solution yet...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
The PBR matching depend on your fw rule, so it would be usefull a capture to see how it looks like. Only one object with port TCP/443 should have the option Match for Any enabled, https object has this, so disable the option on one of the objects. On the rule are using specific service objects or any? I have found that using only the FW rule as condition can be quit problematic, in some cases, the reply packets are also routed trought the destination interface instead of sending it back to the internal interface. I would try to add another condition, for example the internal interface or source IP network.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
we have two rules:
100 source_A destination_B tcp_443_noage
500 source_C destination_D any
for Rule 500 we configured PBR
thanks for advice for additional condition!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
On rule 500, you are using service ANY. In that case, any service or service-range with option "Match for ANY" can match here. In the case of port TCP/443 you have two objects with this option enable, https and tcp_443_noage. According to sk150553 "it is highly recommended not having any conflicting or overlapping services with Match for 'Any' on."
I think the easiest way to fix this is disabling this option in tcp_443_noage. But if you need to keep the option enabled on this object so just use specific service objects on your rule 500, it would be https plus any other port you want. With that the matching traffic should always use https service object.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
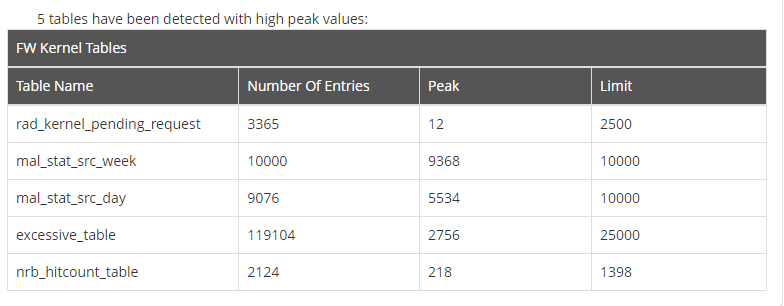
One more question. I checked the firewall health and this is what I found. What does it mean "FW Tables Limit"? this test failed on both nodes. Is there any limit for amount\number of the FW\NAT Rules?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What generated this table you provided?
In general, there isn't a limit on the number of rules you can have.
That said, there can be issues on the management when you're managing a policy with several thousand rules or more.
Due to the mechanisms we provide such as groups, multiple sources/destination/service per access rule, Access Roles, and others, you shouldn't actually need that many rules.
Most policies I've seen that are thousands of rules can often be reduced substantially through an optimization exercise.
What does have limits are some of the kernel tables that we use to keep track of the various traffic going through the gateway.
The "peak" refers to the "high water mark" for the number of entries in the specified table.
Whether this points to an actual problem or not remains to be seen.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
that was HealthCheckPoint: hcp -r all --include-wts yes
There is an Update: one branch just got the same problem, but not GRE interface related. I've created a rule before the existing rule and only for affected traffic and port 443 - it did help!!! How is it possible?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter