- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
Quantum SD-WAN Monitoring
Watch NowCheckMates Fest 2026
Watch Now!AI Security Masters
Hacking with AI: The Dark Side of Innovation
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: VPN tunnel down issue
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
VPN tunnel down issue
Hi All,
I am facing issue with VPN tunnel between Check Point firewall and AWS between Check Point firewall and AWS there is multiple tunnel and that is getting down when not in use multiple time i need to reset tunnel after that its working fine is there any idea we create script through API can send continuous icmp traffic towards AWS tunnel to keep tunnel UP and i no need to reset the tunnel again and again.
Currently our setup is running on distributed 2 GW in cluster manage by MGMT server and all are running on R80.10 with take 189 hotfix.
16 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The SKs that talk about configuring a VPN with AWS mention using Dead Peer Detection--are you using it?
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You need to enable Permanent Tunnel in Tunnel management on the vpn community.
Regards, Maarten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Not sure that option works with 3rd party vendors though...I only seen it work cp - cp tunnels.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Phoneboy/Admin
Thanks for your response i am already using tunnel_keepalive_method dpd and check all other parameter but didn't find solution till now.
get error log packet is dropped because an ipsec sa associated with the spi on the received ipsec could not be found
Action: drop Description: ESP traffic dropped.
I will follow the sk19423 but that is not helpfull for me.
Can i disable NAT T ?? and if i disable NAT T then what is the impact of that in production??
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ramawatar and @PhoneBoy
I am also facing similar issue.
My observation is, in continuous ongoing security parameter negotiations, whenever AWS end negotiates tunnel with NAT-T (4500), tunnel shows UP but no data traverse through tunnel.
(As per few secure knowledge checkpoint only responds for NAT-T negotiation but never initiate negotiation with NAT-T)
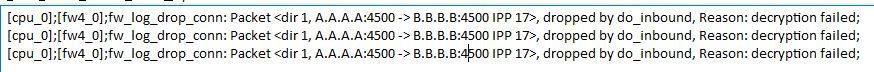
fw ctl zdebug + drop | grep <AWS_gateway> gives decryption failed. (A = My End. B= AWS End.)
I am using BGP protocol to control routing.
BGP TCP handshake not getting complete when IKE negotiation shown IKE NAT-T (4500).
But fw monitor shows my end try to send bgp messages through tunnel and even initial packet comes through aws end but TCP complete connection not happening.
[vs_0][fw_22] eth3-01:i[60]: 169.254.A.A -> 169.254.B.B (TCP) len=60 id=10285
TCP: 45645 -> 179 .S.... seq=2ab5fb15 ack=00000000
[vs_0][fw_22] vpnt6:O[60]: 169.254.B.B -> 169.254.A.A (TCP) len=60 id=0
TCP: 179 -> 45645 .S..A. seq=808ca7b8 ack=2ab5fb16
[vs_0][fw_3] vpnt6:e[60]: 169.254.B.B -> 169.254.A.A (TCP) len=60 id=0
TCP: 179 -> 45645 .S..A. seq=808ca7b8 ack=2ab5fb16
[vs_0][fw_3] eth3-01:E[60]: 169.254.B.B -> 169.254.A.A (TCP) len=60 id=0
TCP: 179 -> 45645 .S..A. seq=808ca7b8 ack=2ab5fb16
When I am doing manual tunnel reset, checkpoint initiating tunnel, where it negotiating on 500 UDP and data starts traversing through tunnel.
Tunnels remain UP, till negotiation not happening through IKE 4500.
Currently I am experimenting to tune below gateway specific parameters to ensure negotiation of IKE 4500 should not happen. (There is no NAT device between my end and AWS)
IKE_SUPPORT_NAT_T
offer_nat_t_initator
offer_nat_t_responder_for_known_gw
force_nat_t
Advanced NAT-T Configuration
These variables are defined for each gateway and control NAT-T for site-to-site VPN: Item |
Description |
Default Value |
offer_nat_t_initator | Initiator sends NAT-T traffic | true |
offer_nat_t_responder_for_known_gw | Responder accepts NAT-T traffic from known gateways | true |
force_nat_t | Force NAT-T even if there is no NAT-T device | false |
Checkpoint team ( @PhoneBoy ) through my above observations please highlight and resolve any interoperability through NAT-T between checkpoint and other vendor device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You're seeing "decryption failed" messages in zdebug, which would suggest a configuration mismatch of some sort.
You'll need to debug it to see where the mismatch is, using something like: https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solut...
Also recommend engaging with the TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Uttam_Ghole
I am experiencing the same issue. Did you manage to resolve it after modifying gateway specific parameters?
Regards,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Aroma2118 We are facing Issue with AWS tunnel only, now working fine we disable NAT T from for all security gateway & set tunnel_keepalive_method DPD
To enable DPD monitoring:
On each VPN gateway in the VPN community, configure the tunnel_keepalive_method property, in GuiDBedit Tool (see sk13009) or dbedit (see skI3301). This includes 3rd Party gateways. (You cannot configure different monitor mechanisms for the same gateway).
In GuiDBedit Tool, go to Network Objects > network_objects > <gateway> > VPN.
For the Value, select a permanent tunnel mode.
Save all the changes.
Install policy on the gateways.
For best practice Use Respective Gaia Version VPN Administration Guide.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i have this same issue with static routes. could you please tell, did you manage to resolve this issue. kindly let us know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Is DPD still needed for permanent tunnel checks in R81.20. Also, is guiDB still needed to enable it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
DPD is still used for permanent tunnels.
In fact, from R81, DPD is set as the default for newly created Interoperable Objects.
If I understand Scenario 5 of sk108600 correctly, unless you've changed the setting from the previous default, it should be changed upon upgrade to an R81+ release automatically.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, We had heaps of VPN issues with AWS. This all got sorted when we upgraded firmware to R80.20.
Have you tried doing that.
We also have a script running that check tunnel ping and then resets tunnel if needed.
Could try those steps.
Sajid
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Sajid_Abbas yes it's resolve in R80.20, we also already upgraded our infra from R80.10 to R80.20
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Was it related to sk142355 VPN tunnel goes down after policy push, must be reset to bring it up?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sajid_Abbas,
We are in need of a script to reset the tunnels every time they go down (we check by ping). Can you share it with us? Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Sajid_Abbas,
We also need automatic ping check and tunnel reset, can you share with us the script you have? Thank you so much!
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 37 | |
| 25 | |
| 11 | |
| 10 | |
| 8 | |
| 7 | |
| 7 | |
| 5 | |
| 5 | |
| 4 |
Upcoming Events
Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Tue 10 Feb 2026 @ 03:00 PM (CET)
NIS2 Compliance in 2026: Tactical Tools to Assess, Secure, and ComplyTue 10 Feb 2026 @ 02:00 PM (EST)
Defending Hyperconnected AI-Driven Networks with Hybrid Mesh SecurityFri 13 Feb 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 43: Terugblik op de Check Point Sales Kick Off 2026Thu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter