- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: VPN daemon timed out
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
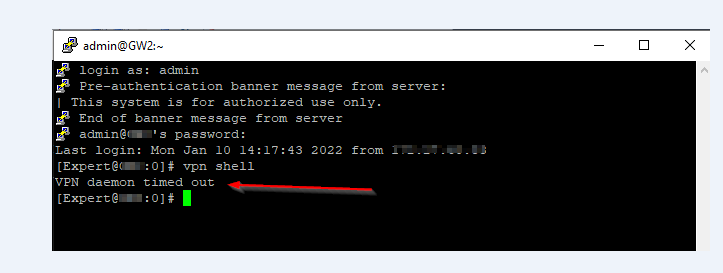
VPN daemon timed out
Hi,
one of our customer is having issue with vpn command. We are getting a Timed out
The Firewall is running on R81 Take: 44
Have you experienced such issue?
Thank you
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Take it with TAC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just curious, are you having actual S2S vpn issues, or ONLY output of this command is the concern? I guess if vpnd is a problem, then TAC may suggest some debugs for it, for sure.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, in case there is a vpn issue we'll not be able to debug. The firewall hast been updated to R81.10, however the issue has not been resolved. We've opened a TAC Case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apologies it's not clear. Is the VPN blade activated on the gateway and a tunnel configured / established?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct, if not we would have got this output below (from another Gateway without VPN Blade enabled)
# vpn shell
This is not a VPN-1 enabled module
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is very interesting...I tried it yesterday in my lab with vpn blade on and I had same issue as you, but when I ran it on customer's environment with same R80.40 version, worked fine. Now, I tested in R81.10, but let me see if I can find R81 and try. Though, Im 99.99% sure this has absolutely nothing to do with the software version.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have another customer running R80.40 and it's working fine. Would be interesting to have the result of your test.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok...got same thing in R81 as well. Let me do some testing later in my R81.10 lab, as I have latest HFA on it, so will see if I can figure it out, plus, VPN blade has been enabled on it for 2-3 months, at least.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I hate to say this, but I honestly got no clue why this happens. As @_Val_ suggested, open TAC case and have them investigate. I tried so many things in my lab to see if I can get it working (even disabled and re-enabled vpn blade as well), same thing. Tried running multiple options of that command, no luck, sorry brother : - (. Please let us know how it gets fixed, I would love to know.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for helping. The TAC case is ongoing. It seems like things have change on R81
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, but vpn debug steps should be same as before. As far as vpn shell command, that Im not positive, though when I tested In R80.xx flavors, options look the same.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As you observed @the_rock some things involving vpnd did change in R81.10. The vpnd process is very old and has a long list of responsibilities that were stuffed into it over the years which started to cause stability problems.
In R81.10 two responsibilities of vpnd were split off into two new daemons: iked and cccd. The former daemon handles IKE negotiations and the latter daemon cccd seems to be related to endpoint compliance. @GrassF it is possible that the vpn shell command you are trying to run has not been updated to reflect this change thus the timeouts, disabling the new iked process with vpn iked disable might fix your timeout issue but I'd advise against trying that, as it is not documented and may cause an outage. Please post the output of these two commands:
vpn iked status
vpn cccd status
Gaia 4.18 (R82) Immersion Tips, Tricks, & Best Practices Video Course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
Now Available at https://shadowpeak.com/gaia4-18-immersion-course
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
# vpn iked status
vpn: 'iked' is enabled.
vpn: The 'iked' process is currently running.
# vpn cccd status
vpn: 'cccd' is disabled.
vpn: The 'cccd' process is currently not running.
# fw ctl get int ike_in_separate_daemon
ike_in_separate_daemon = 1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Attention, quoting from Important security update - stay protected against VPN Information Disclosure (CVE-2024-24919)
In R81.10 we added a feature to improve VPN performance - named CCCD
This feature is disabled by default, and we know about few advanced customers who are using it.
Customers who enable CCCD are still vulnerable to CVE-2024-24919 even after installing the Hotfix!
YOU MUST DISABLE CCCD TO BECOME PROTECTED!
Instructions below and also on SK182336:
Run the command: vpn cccd status
The expected output is: vpn: 'cccd' is disabled.
If the output differs, stop the CCCD process by running the vpn cccd disable command.
More info by the link above.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter