- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Updatable Objects for MS Teams matches Github
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Updatable Objects for MS Teams matches Github
Hello Folks,
just stumbled over a possible MS Teams problem a customer is fighting for months ...
sometime the Updatable Objects IP matches on a different category ... then of course the policy doesnt match anymore, resulting in a drop.
dynamic_objects -ip 52.113.83.112
The following objects contain IP 52.113.83.112
Object name: CP_MS_Skype
Object type: Updatable Object
Object name: CP_Azure_Azure
Object type: Updatable Object
Object name: CP_GH_GITHUB
Object type: Updatable Object
so IP 52.113.83.112 should be an IP from the O365 MS Teams Range 52.122.0.0/15
https://learn.microsoft.com/de-de/microsoft-365/enterprise/urls-and-ip-address-ranges?view=o365-worl...
this results in a drop on my policy:
@;81095432.634111613;[vs_0];[tid_19];[fw4_19];fw_log_drop_ex: Packet proto=6 10.10.42.68:57203 -> 52.113.83.112:3478 dropped by fw_send_log_drop Reason: Rulebase drop - on layer "POLICY" rule 922;
did anybody notice this already as well?
i was always thinking this Updatable Objects are quite reliable ... but why this IP can matche on sometimes totally different categories? CP_GH_GITHUB & CP_MS_Skype
12 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I assume you mean 52.112.0.0/14 and not 52.122.0.0/15 , 52.113.83.112 matches the first subnet.
The issue is that Microsoft states it belongs to them and Github does the same, that it belongs to Github.. Since Github uses more specific subnet I would pick them. But anyway there is something strange going on, outside reach of Check Point. Check Point uses 3d party info to fill the tables. And if both tables claim the ip is for them what can you do 🙂
Here you can find that Github uses 52.113.83.0/24
-------
Please press "Accept as Solution" if my post solved it 🙂
Please press "Accept as Solution" if my post solved it 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
from my experience in the case of MS products AppCtr definitions seems to be more accurate than UO.
Microsoft has lots of those networks to use:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you run command -> dynamic_objects -uo "whatever name of github updatable object"
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
well yes:
the thing is ... both Updateable Objects contain both subnets ... based on my policy it sometimes matches the subnet on "Microsoft Teams Worldwide" then on "GitHub Services"
[Expert@XXXXXXXXXXXX:0:ACTIVE]# dynamic_objects -uo "GitHub Services" | grep 52.113
range 1037 : 52.113.9.0 52.113.9.255
range 1038 : 52.113.12.0 52.113.12.255
range 1039 : 52.113.16.0 52.113.31.255
range 1040 : 52.113.37.0 52.113.63.255
range 1041 : 52.113.69.0 52.113.69.255
range 1042 : 52.113.83.0 52.113.83.255
range 1043 : 52.113.85.0 52.113.86.255
range 1044 : 52.113.112.0 52.113.127.255
range 1045 : 52.113.129.0 52.113.130.255
range 1046 : 52.113.135.0 52.113.151.255
range 1047 : 52.113.160.0 52.113.191.255
range 1048 : 52.113.198.0 52.113.199.255
range 1049 : 52.113.205.0 52.113.206.255
range 1050 : 52.113.208.0 52.113.223.255
[Expert@XXXXXXXXXXXX:0:ACTIVE]# dynamic_objects -uo "Microsoft Teams Worldwide" | grep 52.1
range 0 : 52.112.0.0 52.115.255.255
range 1 : 52.122.0.0 52.123.255.255
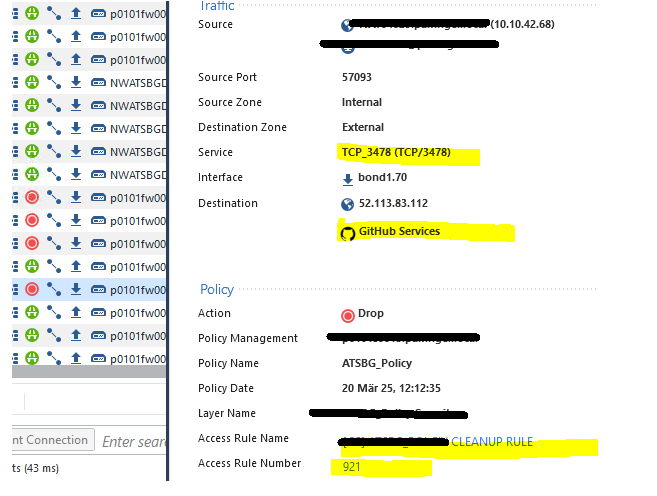
when it matches on Github it results in a drop ... because the existing Github Rule does not contain the services used for MS Teams and the packet matches again on the CleanUP rule ... sure i could move around some rules ... but i consider this as a flaw ..
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I totally agree, it is flaw in my view as well. Did you contact TAC about it?
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I also tried grepping for teams with that command, but nothing came up, but those IPs definitely match.
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well yes, i bet its time to contact TAC.
i will keep you informed...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks so much Thomas, Im also super curious about this.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We use the information provided by the relevant vendor for our Updatable Objects.
If there are errors in that data...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Guys,
well i see NO reason to change any rules, because the policy matching, or lets say, which Updateable Object the FW chooses for policy matching is changing from session to session.
take a look:
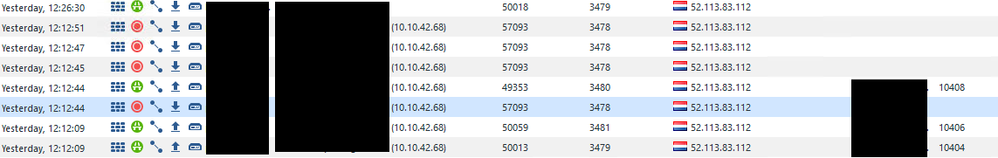
my logging resulsts, during a MS teams call.
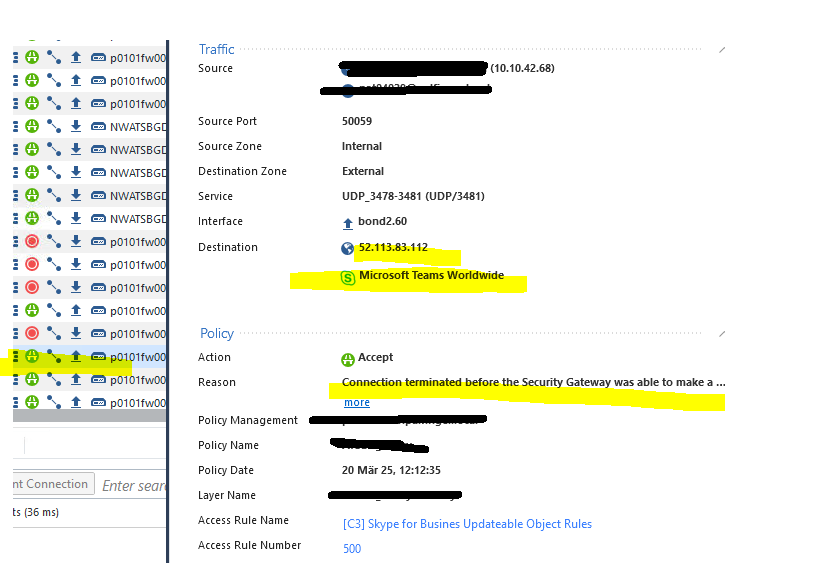
SRC: 10.10.42.68 and DST: 52.113.83.112
sometimes accept, sometimes drop.
fist the accept, it matches on MS Teams ...
then the drop:
same SRC & same DST. just new SRC port, so lets say a new connection ...
but is says Github this time ...
lets see what TAC can do here, since the firewall changes its match on the DST IP from time to time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I agree with you, rules look fine.
Andy
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 18 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter