- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Standalone to Full HA Member (VLANs, Cluster o...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Standalone to Full HA Member (VLANs, Cluster on different subnets, VPN, etc involved)
Hello everyone.
We currently have a Check Point 4200 device installed and operating in Standalone mode in our company. With respect to Security Management, it has activated the most common Blades (Firewall, IPSec VPN, URL Filtering, etc.) with basic policies of internet connection for the internal network, access to the servers from the Internet and the clean up policy.
For the Security Gateway, the eth0 (LAN) port is configured with 10 VLANs (/24), the eth1 port for a VPN (/29) and the eth2 port for the Internet (a /30).
Under the above scenario, I must configure another Check Point 4200 so that it operates in HA with the previous one. These are my questions:
- How do I configure the IP of the internal cluster having the eth0 port 10 VLANs?
- The eth1 port will be released and the VPN and Internet will be coming in different VLANs on the same cable, is the configuration the same as in the previous case?
- What effect would it have on policies to apply the sk104699 to add the operational Check Point to a cluster in Full HA?
For the external network I planned to use the sk32073.
Thank you in advance.
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
More details are good ![]()
The primary and secondary members need to have unique IP addresses configured per subnet.
Which means, for eth1.x VLAN you'll have 10.10.x.251 on your primary and 10.10.x.252 on your secondary.
The cluster IP for that subnet will be a third IP (maybe 10.10.x.253?) which you will configure in the cluster object in SmartConsole.
Since you need three IPs per subnet for the cluster alone and a /30 only allows for two IPs, you will need bigger subnets for the eth3 VLANs.
For eth3 (non-VLAN) where the public IP currently resides, you will need to create a different private subnet as described in sk32073.
This subnet will be used for the cluster on that interface.
The public IP address will be configured in the cluster object in SmartConsole.
Does that help?
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Basically in a cluster, the members should be on the same subnets.
When VLANs are involved, the VLAN configuration on both members should match (IPs on each VLAN should be on the same subnet).
If you're replacing eth1 with VLAN ports, that same logic applies.
The policy rules should be more or less the same unless of course you're disabled some of the implied rules that allow modules to talk to one another.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, considering that the internal IP of the cluster is on a different subnet, and after having both members configured with IPs on the same subnet of each VLAN, should routes be created from that subnet to the IP of the cluster?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you're talking about the rest of the networking around the cluster, yes, you will configure the routing so that routes point to the Cluster IP for the relevant interface.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm sorry Dameon Welch Abernathy, I'm not getting the point. If I may, I want to show you the scenario I'm working on so that you could help me with some specific questions. The Standalone has it's eth1 port currently configured as follows:
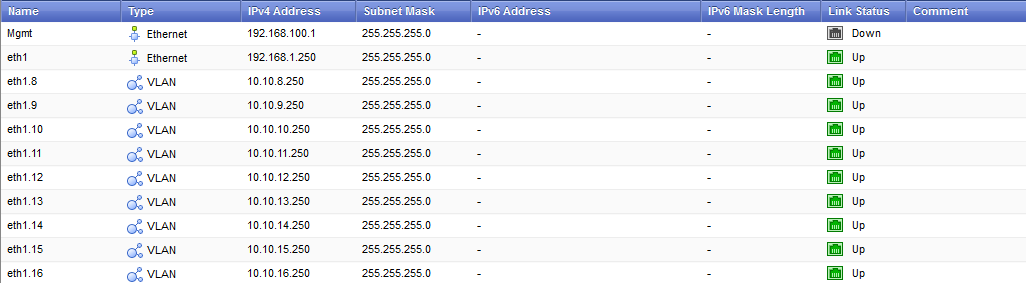
Considerenig that I want to use the 192.168.1.250 IP as the cluster's internal IP (because it is currently my default gateway), do I have to:
- set an IP for the eth1 port from the 192.168.1.0/24 subnet? For example 192.168.1.251 for the primary member and 192.168.1.251 for the secondary member.
- set an IP for the eth1.x VLAN from the 10.10.x.0/24 subnet? For example 10.10.x.251 for each VLAN of the primary member and 10.10.x.252 for each VLAN of the secondary member.
Furthermore, the Standalone has it's eth3 port currently configured as follows:
- eth3: Type Ethernet, IPv4 Address -Public IP-, Subnet Mask 255.255.255.252, Link Status Up.
- eth3.100: Type VLAN, IPv4 Address 10.0.x.x, Subnet Mask 255.255.255.252, Link Status Up. (There's a VPN over this VLAN).
- eth3.200: Type VLAN, IPv4 Address 10.x.x.x, Subnet Mask 255.255.255.252, Link Status Up. (There's an IPSec VPN over this VLAN that must not be routed to the internet).
Considering that I want to use the -Public IP- as the cluster's external IP, how do I set the eth3 port, eth3.100 and eth3.200 VLANs for both members?
Thank you in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
More details are good ![]()
The primary and secondary members need to have unique IP addresses configured per subnet.
Which means, for eth1.x VLAN you'll have 10.10.x.251 on your primary and 10.10.x.252 on your secondary.
The cluster IP for that subnet will be a third IP (maybe 10.10.x.253?) which you will configure in the cluster object in SmartConsole.
Since you need three IPs per subnet for the cluster alone and a /30 only allows for two IPs, you will need bigger subnets for the eth3 VLANs.
For eth3 (non-VLAN) where the public IP currently resides, you will need to create a different private subnet as described in sk32073.
This subnet will be used for the cluster on that interface.
The public IP address will be configured in the cluster object in SmartConsole.
Does that help?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It helps a lot! Don't know why, but I thought I could only have one cluster IP per interface (I used to consider ethx with it's VLANs as one interface). Now I know that it is possible to set each VLAN to it's own cluster IP just like any other interface. Thanks again!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Each VLAN is basically it's own interface as far as the Security Gateway is concerned.
Likewise, when you bond two or more physical interfaces together, the Security Gateway treats it like a single interface (unless it has VLANs, of course).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Dameon Welch Abernathy.
Since the last time we talked, I tried to apply what you had taught me. But after configuring the ports and VLANs, upon reaching step 6 of the sk104699 procedure, to configure a Standalone machine to become a part of a Full HA cluster, the SmartDashboard crashes and throws me the attached error.
Thanks in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If SmartDashboard is crashing, I would engage with the Check Point TAC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I managed to find the error and fix it. Now, on my test lab, I have configured each cluster member as follows:
- Cluster member 1:
Cluster member 2:
And the cluster is up and running with current configuration:
But there's a problem, I can't acces the internet. It's there something wrong with my configuration? I've checked SmartView Tracker for droped packages, but every single connection is accepted as line 2 policy states.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
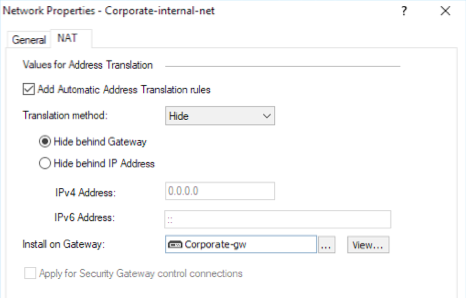
You can see in the NAT rulebase the little "S" on Rule 4.
That implies a Static NAT rule, which will not work since you only have one public IP.
You need to change this to a HIDE NAT, which can be done in the object.
You'll probably want to use the "Hide behind Gateway" option, shown here:
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 18 Dec 2025 @ 10:00 AM (CET)
Cloud Architect Series - Building a Hybrid Mesh Security Strategy across cloudsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter


