- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: SSL inspection bypass for Signal app
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SSL inspection bypass for Signal app
Hi,
Did someone manage to configure SSL Inspection bypass for Signal app on R80.30 based on custom application?
I have ssl enhanced inspection enabled, 1 rule with custom application (textsecure-service.whispersystems.org) with action bypass, and second rule to inspect everything. Signal traffic always hits second rule.
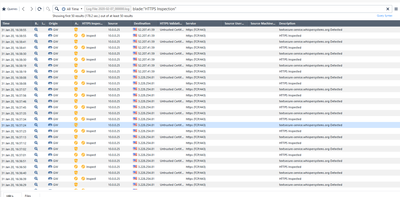
In logs I can find:
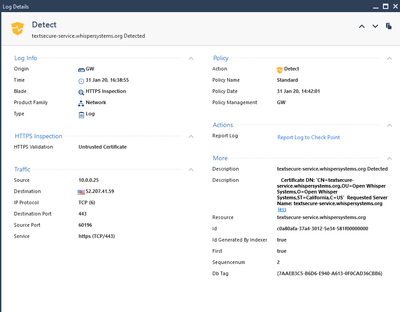
First SSL Inspection log: textsecure-service.whispersystems.org Detected
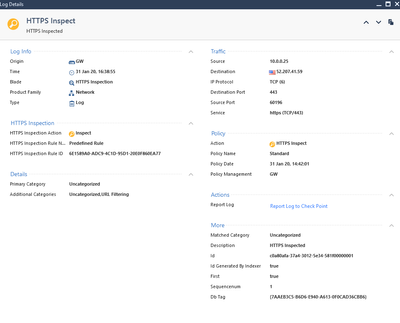
Second SSL Inpsection log: Matched Category: Uncategorized, HTTPS Inspected
So it looks that aplication (url) is detected properly but NGFW still want's to inspect it.
Best Regads,
Maciej
9 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Properly redacted screenshots of the relevant log cards and rules used will be helpful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regarding to this Signal support article you will need to bypass wildcard URLs, https and UDP.
Allowing all UDP Traffic will make your firewall vulnerable to the UDP hole punching attack.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This works fine with other URL's on our FW's.
Is your https inspection enabled? I think so.
More read here
R80.x - Performance Tuning Tip - SNI vs. https inspection
or here:
HTTPS Inspection and website categorization improvements introduced in R80.30
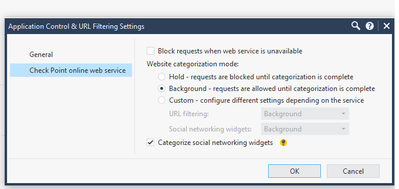
If that doesn't help! Please some pictures of the https settings.
➜ CCSM Elite, CCME, CCTE ➜ www.checkpoint.tips
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
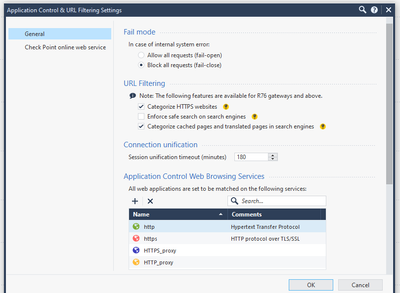
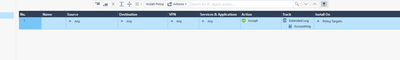
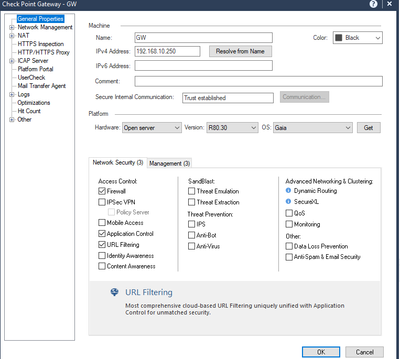
as requested adding config and logs screenshots.
Best Regards,
Maciej
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've this issue when I can't bypass by using domain names. I've to use IP:s. I guess it has to do with certificate pinning. But I might be wrong. But as soon as the traffic is intercepted the application fails. So get signals(in this case) ip-range and make a bypass rule for that. See if it works!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
There is certificate pinning. But I don't want to inspect. Bypass should work as I see certificate cn.
Yes, bypass works for IP addresses.
According to: sk104717 in R80.30 probe bypass was introduced - enabled by default.
Bypass mechanism was improved to better reflect policy and resolve the above limitations:
- Stop the inspection of the first connection to bypassed sites.
- Allow bypass of Non-Browser Applications connections.
- Allow Bypass of connections to servers that require client certificate.
- New probing mechanism eliminates the need to inspect the first connection to an IP address unless it is required by the policy.
Limitation.
HTTPS Inspection will not work for sites that require SNI (Server Name Indication) extension in the SSL "Client hello" packet. (Server Name Indication is an extension to the Transport Layer Security (TLS) computer networking protocol by which a client indicates which hostname it is attempting to connect to at the start of the handshaking process.)
There is SNI inside Client Hello, but I do not want to inpsect. I want to bypass so this limitation is irrelevant.
Best Regards
Maciej
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What if you set the category for your custom site to one you are bypassing?
Might also be worth a TAC case.
Might also be worth a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there,
I have few ideas. First of all inspection rule any any is not recommended. Please try to define source and destination.
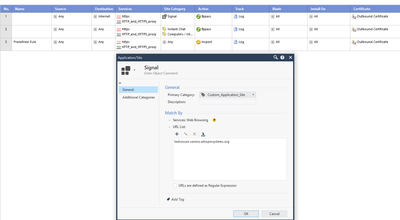
For some reason this url is not categorized as custom app but is matched as uncategorized. In custom app (signal) settings tick the box urls are defined as regular expressions and modify url to .*textsecure-service.whispersystems.org.*.
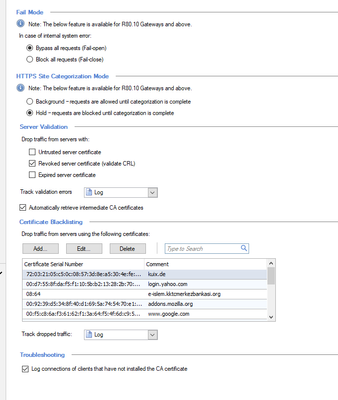
I see that server is using self-signed certificate. Try importing it to trusted CA list. I see you have drop traffic from untrusted servers unchecked, but it is quick try so worth checking.
* Server certificate:
* subject: C=US; ST=California; O=Open Whisper Systems; OU=Open Whisper Systems; CN=textsecure-service.whispersystems.org
* start date: Feb 15 17:38:17 2019 GMT
* expire date: Mar 12 18:20:20 2029 GMT
* issuer: C=US; ST=California; L=San Francisco; O=Open Whisper Systems; OU=Open Whisper Systems; CN=TextSecure
* SSL certificate verify result: self signed certificate in certificate chain (19), continuing anyway.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any news or solutions to that?
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 22 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 3 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter