- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
R82.10 and Rationalizing Multi Vendor Security Policies
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Querying routing table in a ClusterXL
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Querying routing table in a ClusterXL
Hello, everyone.
I have a query.
What is the best way to query a specific route within a ClusterXL?
I have noticed differences when using the command "route -n", and "ip route get <IP Destination>", because when I query a route for example for the destination 10.120.1.77, if I do it with the command "route -n" it tells me that I reach it through the interface eth1-02.139 which is a VLAN, but if I query it with the command "ip route get <IP>", it tells me that I reach it through the interface eth1-02 (without vlan).
Can you clarify the doubt, please?
Thank you.
Which of the 2 commands is more "reliable" when I want to query the route for a destination?
Labels
- Labels:
-
ClusterXL
-
Gaia
-
Open Server
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, everyone.
Our reported problem with the SecureXL atypical pulling connections from a source to a destination has been fixed for the moment by upgrading the JHF package to version 173 of R80.40.
Thanks to all for the support.
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What version/JHF?
And I’m not clear what you mean by query here.
The full CLI command entered might be helpful.
Also there are clish commands that may be more appropriate here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, my friend.
Thanks for your prompt reply.
I understand, that the routes when working with a ClusterXL, must be identical in both members. Is this correct?
Based on this theory, is that I expose my doubt.
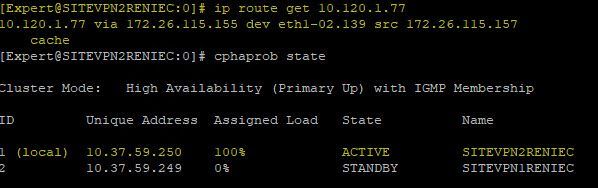
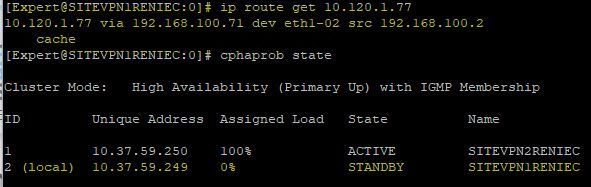
In the images that I share here, you can see that when I make the query to both members with the command "ip route get 10.120.1.77 the result I get is different.
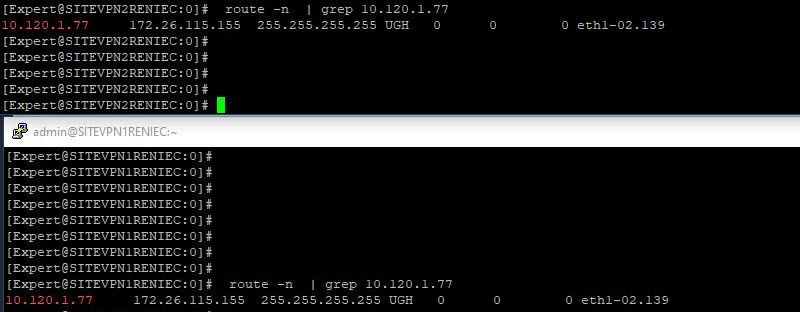
However, when I query both members, using the command "route -n | grep 10.120.1.77", the result is the same in both members.
Is this behavior normal?
From the CLI expert mode of both Firewalls, which of the two commands is more "reliable" to query the route table?
route -n, or ip route get <IP DST>?
The SITEVPN2RENIEC unit has the JHF 102 and the SITEVPN1RENIEC unit has the JHF 161.
Thanks for any comments.
Regards.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The routes don't need to be identical between members, no. Cluster members can have "non-monitored, private" interfaces which don't participate in clustering, and which can have unique configuration per member. This generally isn't a good idea, but it is possible.
'route -n' and 'ip route get' are asking the system two different questions.
'route -n' requests that it show you the routes in its FIB. This is showing you an input to the routing decision. If you want to predict the routing decision which would be made, you then must interpret the data and the other inputs to the routing decision.
'ip route get' asks the system to evaluate the FIB for a destination and tell you what interface and next hop it would use to reach it. This is showing you the output of the routing decision. Since this involves getting the result from the FIB, it is not subject to human misinterpretation. It doesn't tell you why it made a given decision, though.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In your screenshot we don't see the eth1-02 (without VLAN) output?
To help set a baseline, is this cluster running only with static routing or also dynamic (ospf / bgp / ecmp)?
Are all interfaces connected/up on both systems?
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Sorry, the images did not load completely.
I am loading the image with respect to the other FW that is part of my ClusterXL.
In the image, you can see, that to reach the same IP, the FW has as reference only eth1-02 (No VLAN).
This behavior does not seem normal to me.
But when I make the query, using the command "route -n", the result I get in both FW is the same, it means that both FW reach that destination through the interface that is tagged with the VLAN 139.
Therefore, I want to know which of the two commands is the one that Checkpoint refers to as "reliable" to query the routing table from the CLI.
This problem is causing that the IP 10.120.1.77, can not consume a service that is within our network, and everything seems to indicate that it is due to routing problems.
Do you have any opinion that can help me?
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Bob_Zimmerman Provided an answer above, further insights require additional information such as the version/JHF level, routing protocols used and interface status on each member as requested above.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Chris.
Thanks for your reply.
Currently we are only working with static routes (we do not work with dynamic routing).
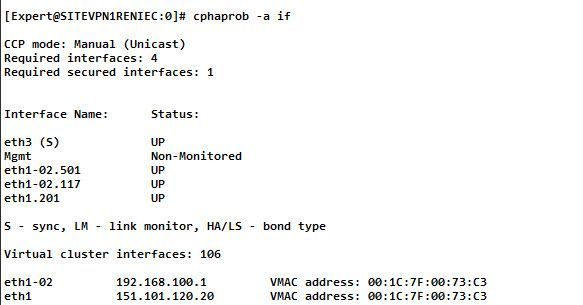
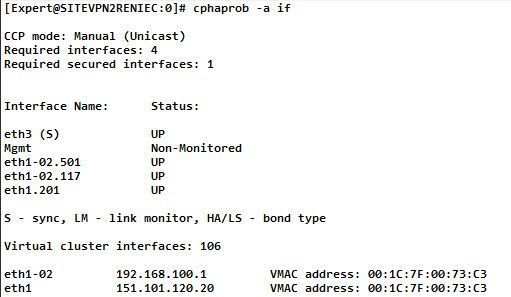
The status of the interfaces, I think you mean the output of "cphaprob -a if" command on each cluster member, right?
I share with you some images regarding the output of this command in each GW.
The problem exists when Member1 (SITEVPN1RENIEC), works as ACTIVE within the Cluster.
Currently Member2 (SITEVPN2RENIEC) is working as ACTIVE as a corrective measure we have taken.
I think that the communication problem, from IP 10.120.1.77 to Real IP 151.101.180.146 (which has a NAT IP 192.168.100.37), when we try to work with MEMBER1, is due to a routing problem, but I am not sure of my theory.
Thanks for your help and participation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Check & compare the configuration/outputs between the nodes.
If the outputs match and forwarding is contrary to what's configure please consult TAC further who can provide guidance based on your specific version/JHF level. (Maybe also try removing and adding again the route on the standby/problematic gateway).
- show configuration static-route
- show route static all
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Chris.
After having reviewed my case in depth once again.
We found the following problem.
Firewall Policies -> OK
NAT -> OK
Routing -> OK
The problem is apparently focused on the SecureXL of MEMBER 1 of my Cluster.
When the SecureXL is left by default (Active) in the GW, the IP 10.120.177, it cannot get to open the port 1414 of the 192.168.100.37 (This IP is actually a NAT IP, which translates to an IP 151.X.X.X.X).
So, when I disable SecureXL on the GW completely, the traffic works fine.
Is it normal that SecureXL is giving me problems for a single traffic flow, on 1 single member of my Cluster?
On MEMBER 2, everything works fine, I have no need to disable SecureXL.
What solutions can I have in this case?
Thanks for your support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No this generally wouldn't be considered normal, which version & JHF is used on the gateway?
To expedite resolution please investigate it further with TAC.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If disabling SecureXL solves a problem, then it generally points to a bug.
That requires a TAC case.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
Currently the GW are as follows.
Member 1 -> Take 161
Member 2 -> Take 102
Indeed, a TAC staff, has recommended us, to align both GW to the JHF Take 173, to check if this behavior improves.
We are going to perform the activity in a window, and I will be reporting the results.
Thanks for your support.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sorry I hadn't noticed that you had already supplied the JHF level info above else would have asked why they were different...
Please update us with the results. 🙂
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, Chris.
Initially, the 2 members had the JHF 102, but the problem of communication between IP -> 10.120.x.x to IP -> 192.168.x.x.x started to show up.
The case was reported to TAC at that time, and the Engineer who helped us told us at that time that we should upgrade the JHF to Take 161.
Our customer out of fear only decided to upgrade the Take of Member 1, because when we did it the communication problem persisted (that is the reason why now both members are now uneven).
We had to reopen a case with the TAC recently, and we found out that the problem is because of the SecureXL of member 1.
TAC has again asked us to update the Hotfix package to version 173.
This is how our scenario looks like.
I will update the packages, and I will be notifying the news.
Thanks for the help.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, everyone.
Our reported problem with the SecureXL atypical pulling connections from a source to a destination has been fixed for the moment by upgrading the JHF package to version 173 of R80.40.
Thanks to all for the support.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 11 | |
| 8 | |
| 7 | |
| 6 | |
| 5 | |
| 5 | |
| 4 | |
| 4 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldFri 09 Jan 2026 @ 10:00 AM (CET)
CheckMates Live Netherlands - Sessie 42: Looking back & forwardThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2026 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter