- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- O365 + HTTPS Inspection + Bypass
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
O365 + HTTPS Inspection + Bypass
Hi All,
This issue has been discussed before in
but I have a few questions about this issue
I am running App control + HTTPS Inspection in R80.20.
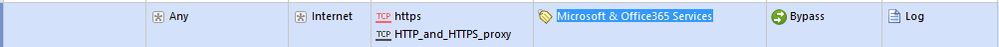
In the HTTPs Inspection policy, I bypassed Microsoft and Office365 services category as in the below rule but traffic to office365 is still inspected by https inspection
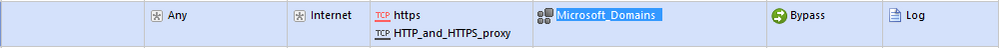
So in order to mitigate it, I had to create a custom category with all Office365 and MS domain
My questions are:
1. Is the fact that the "Microsoft & Office365 services" category do not resolve Microsoft & Office365 URL/domains is a bug in R80.20?
2. is there a way to make it work in R80.20 without adding all Microsoft Domains to the bypass rules (and without waiting for R80.40)? (sk104564 discuss adding manual domains but it refers to R70.20 only. if it is relevant to R80.20 as well, please update the SR)
3. It is discussed that activating "enhanced_ssl_inspection" can help this issue. What is this exactly and how it can be achieved?
13 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are you on JHF 117 or above?
You need that for SNI support, which should make the simple “easy” rule work.
You need that for SNI support, which should make the simple “easy” rule work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
H PB,
I didn't upgrade yet to JHF 117 but I am willing to try. Is there an SK or any documentation about it?
Whitelisting all MS domains is tedious. They have 20 different domains for each service they offer.
I didn't upgrade yet to JHF 117 but I am willing to try. Is there an SK or any documentation about it?
Whitelisting all MS domains is tedious. They have 20 different domains for each service they offer.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There's not much on it other than what's said in the R80.30 release notes.
Basically it enhances the certificate matching used for "light" inspection to also include support for SNI.
Basically it enhances the certificate matching used for "light" inspection to also include support for SNI.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
PhoneBoy hinted towards it but the reality needs a stronger statement (IMHO): upgrade to R80.30 - it properly fixes this!
I have O365 on various sites and it's been pretty much impossible to do anything with an expectation of 100% success other than a complex exclusion from HTTPS inspection using the Microsoft IP subnet based destinations as a HUGE group of networks which we update weekly from the published Microsoft list of O365 subnets just like you have had to do.
....until R80.30!
The SNI and other really effective changes Check Point have made from R80.20 to R80.30 in HTTPS inspection make it a genuinely realistic option...make sure you're sitting down here...to do HTTPS inspection on Office 365 traffic!
The enhanced_ssl_inspection parameter is now (at r80.30 level) completely irrelevant and ignored by the kernel.
For example, I support a site with HTTPS fully enabled, we're rolling out O365 and all I have done is allow the Application Microsoft & Office365 Services for all users. I have tested quite thoroughly for all of the main applications and everything works, with the exception of file transfer within a Teams chat (which never used to be able to work in Skype with HTTPS inspection either - I'm guessing it's a similar issue) but most corporates are not at all bothered that this particular backdoor is closed, albeit accidentally.
I have a major issue with the ability to access personal outlook.com and I'll be posting separately about that but for your needs, once upgraded to R80.30 you can drop loads of HTTPS inspection overrides and expect success! Do expect to have to keep HTTPS inspection overrides for Dropbox and Box (there's a full list in usercenter) which use sticky certificates and craplicaitons by such companies as Fedex and DHL which just break if you look at them in the wrong way.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In our HTTPS Inspection Best Practices sessions we've done in local user groups, we make exactly this point. 😁
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is really good news as I hate MS / O365 network requirements - pls don't proxy us, pls don't intercept, but do filter on URLs with wildcards... Worst security setup ever
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi john
regarding your implementation, is the picture below, similar to what you implemented?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Good info put here John!
It is sufficient reason upgrade to R80.30
I wish there was an SK with all services which have issues with HTTPS inspection. I guess it is impossible to test all but at least put a list of high usage apps like box/dropbox/O365 that can break using HTTPS inspection and how to bypass them
It is sufficient reason upgrade to R80.30
I wish there was an SK with all services which have issues with HTTPS inspection. I guess it is impossible to test all but at least put a list of high usage apps like box/dropbox/O365 that can break using HTTPS inspection and how to bypass them
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
good stuff.
So if I get it correctly, HTTPS Inspection bypass is working on R80.30 with the pre-defined apps mentioned in the SK?
and on R80.20 and lower versions, I have to create a custom app with domain names to do the HTTPS Inspection Bypass?
So if I get it correctly, HTTPS Inspection bypass is working on R80.30 with the pre-defined apps mentioned in the SK?
and on R80.20 and lower versions, I have to create a custom app with domain names to do the HTTPS Inspection Bypass?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hope you are doing fine. Would you mind pointing which SKs do you used to do proper overrides on applications? Do you use the bypass action?
There are some applications that i still have issues with even in R80.30, the only way to make them work is probe bypass but... 🙂
I think that the real killer will be the granular HTTPS inspection policy on R80.40
____________
https://www.linkedin.com/in/federicomeiners/
https://www.linkedin.com/in/federicomeiners/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So, I have read through this entire thread, and I'm a but confused as the "Microsoft & Office365 Services" Tag does not appear to be working for me. I have created a separate custom App/Site list made from my own observations of the logs and from Microsoft's website of addresses and IP's that need to be allowed. My list works, but the built in "Microsoft & Office365 Services" does not.
I'm using R80.40. Any ideas why this might be a problem?
Thanks.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
in R80.40 you can use updatable object for o365 services for that. There are several updatable objects all related to different Microsoft services so maybe you have to figure out which one you use and pick the right one.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 10 | |
| 8 | |
| 4 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter