- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: New build of VSX cluster
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
New build of VSX cluster
Hello all
I am building a new VSX cluster. Is the recommendation to get as much topology in place before or after the conversion to VSX?
Should I be converting it straight away after the first time wizard, or getting as much done as possible beforehand?
Thanks in advance
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all
Thanks very much for all of your replies. This is a great forum!
The issue is resolved and it was nothing overly complicated in the end.
We are adopting Cisco's ACI and one of the filters written by our vendor had a typo. The port name was "tcp-18208" but the actual value was tcp/12808. It resulted in there being an issue part way through which must be why it was complaining of a SIC issue part way through the build.
I have 18208 here as:
tcp/18208 | FW1_CPRID - Check Point Remote Installation Protocol | Remote Installation of packages in SmartUpdate from Security Management Server / Customer Management Add-on (CMA) / Domain Management Server (by CPRID daemon) to Security Gateway |
Once that was corrected it just worked and I now have a VSX cluster!
Thanks for all the engagements on this.
11 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Install a physical GW, set up management interface only and management routing, then convert to VSX and build VS topology on the VS level.
If you use bonded interfaces, define bonds before conversion.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks
I have been trying to get this set up but the VSX cluster keeps ending with errors... it says there is no SIC connectivity to the two gateways, however, part of this set up process was to initialise SIC (it replied back Trusted).
What could I be missing here? The gateways do not exist in smart console yet, I am adding them as part of the process of creating a VSX cluster.
THanks in advance
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any screenshots and/or video of the process?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, sorry, I can't owing to the environment classification (I'll get in trouble) but, if I elaborate, there may be a step I have missed out. Currently the Manager is the only device visible in Smart Console.
Both gateways are reachable and I have previously had them registered as normal gateways in Smart Console, SIC is possible. There's no policies in Smart Console yet.
When they registered in Smart Console I have tried to create 2 new VSX gateways using the Checkpoint Gateway Installation WIzard. It gets all the way to the end but then throws a SIC error. This doesn't make sense given they have already been through SIC in that process and it has stated that trust is initialised.
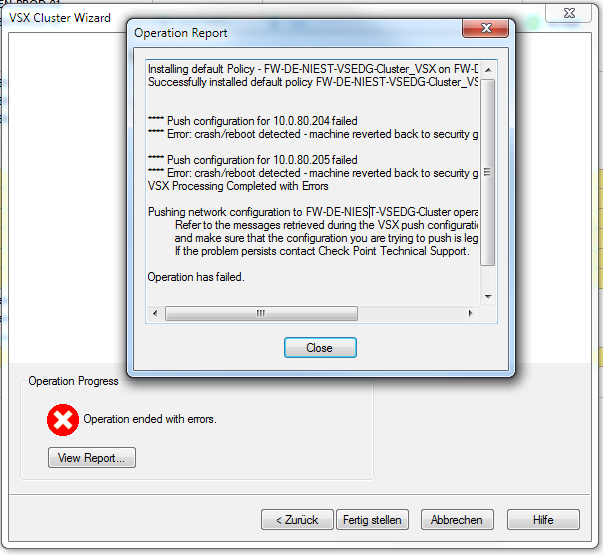
Anyway, this is a copy of the screenshot (lifted from google images) of what I got when I just tried to create a VSX cluster, introducing the gateways to Smart Console at the same time.
[I WILL POST AN IMAGE IN A SUBSEQUENT MESSAGE - THE FORUM IS NOT HAPPY WITH ME 🙂 )
Owing to it failing I cancelled however it has already converted the gateways to VSX and I can no longer access them by SSH, but I can still SIC to them. They currently do NOT appear in Smart Console as I cancelled the wizard. Even though I can SIC to them I can't introduce them to the manager again as VSX gateways because they still say:
"Installing default policy - [policy name] on [gateway name]
Policy installation failed on gateway. Cluster policy installation failed: See SK125152)
Failed to install default policy on... etc. etc
"
It then lists reasons why a policy install might fail.
I haven't manually created a policy, however, the VSX Gateway wizard creates one to push as part of the add wizard.
Sorry for all the waffle, if I could share screenshots I would.
I hope this is a bit more informative but if not, no problem. I will get hold of our support vendor... was just looking here for an answer if possible. I know it's difficult to expect with limited information. Sorry.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the image I wanted to share after finally getting to reply... I was being told off for duplicate posts for some reason. Probably down to the corporate browsing infrastructure!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK. Just take the VSX admin guide and follow it, you are obviously doing it wrong.
There are two possibilities:
1. Install clean, do not initialize SIC, use GW wizard to setup a VSX GW/cluster.
2. Install as a regular GW and then convert to VSX. Personally, I would not recommend this approach in the first place.
You are trying to use something in between, and that is why it is not working for you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have looked at the SK article and it doesn't seem relevant.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have previously connected the gateways to smartconsole, then you will need to reset SIC on the gateways themselves.
Enter cli on each firewall, type 'cpconfig' into clish and choose the option to reset 'Secure Internal Communication'
It will ask you to type a new SIC key, do this, and then it will cpstop and cpstart.
Wait til all processes are back up, head back to smartconsole and try add the gateways again using the new key.
As mentioned above, do bonded interfaces first before conversion if you have bonds.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
not sure if its to any help, i made a few VSX videos that are available on youtube.
https://www.youtube.com/playlist?list=PL4Jm1LJEII4ZiVFkjtB1zMyOzn0LUVP21
Regards
Magnus
https://www.youtube.com/c/MagnusHolmberg-NetSec
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all
Thanks very much for all of your replies. This is a great forum!
The issue is resolved and it was nothing overly complicated in the end.
We are adopting Cisco's ACI and one of the filters written by our vendor had a typo. The port name was "tcp-18208" but the actual value was tcp/12808. It resulted in there being an issue part way through which must be why it was complaining of a SIC issue part way through the build.
I have 18208 here as:
tcp/18208 | FW1_CPRID - Check Point Remote Installation Protocol | Remote Installation of packages in SmartUpdate from Security Management Server / Customer Management Add-on (CMA) / Domain Management Server (by CPRID daemon) to Security Gateway |
Once that was corrected it just worked and I now have a VSX cluster!
Thanks for all the engagements on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oof. This is the big reason I don't like putting port numbers and such in object names. It means a quick read of the policy can lie to you. Searches also lie to you, since they give you the match without telling you it only matches in the name, not in the actual data which means anything.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 19 | |
| 17 | |
| 8 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter