- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: Meaning of Address Spoofing
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Meaning of Address Spoofing
Hello, everybody.
I have a curiosity about "Address Spoofing".
It is clear to me that when the log shows you a "DETECT" action, the traffic is "allowed", but is it important to "check" the reason for this traffic?
Having this type of logs, can give us "indications" of "Networking" problems in the network of a company?
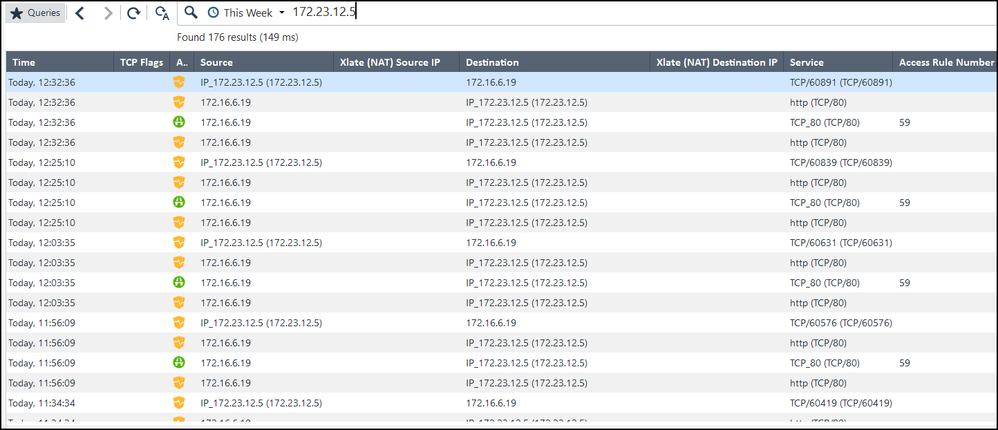
I want to communicate to IP:172.23.12.5 with IP:172.23.3.21, but there is no traffic registered in the CP.
I have policies, I have routes, I have tried with "TCPDUMP" "CPPCAP" "FW MONITOR", but none of these tools show me traffic, when traffic is generated (a simple PING, or a Telnet to any port).
When I "search" in the logs for the origin with IP:172.23.12.5, I only get irrelevant traffic to "other IPs" that have nothing to do with my target.
Could this be a routing problem?
Cheers :).
6 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Absolutely that looks like a routing problem. It appears to be the reply traffic that is triggering anti-spoofing because the source port and destination port are inverted in the logs. So a device out on bond2.303 is sending traffic with a destination of 10.10.100.1 back to the firewall. I am guessing the firewall just routed that packet with a destination of 172.23.12.5:80 out that bond2.303 interface. Could be something else going on though. Potential ICMP redirects flying around but you would see that in pcap. Could be post NAT if that packet was previously NATted.
log filters of
xlatesrc:10.10.100.1 or s_port:58432 or xlatesport:58432
or some combination of that may help you find the initial request that the packet triggering anti-spoofing is replying to, that is assuming the request went through the firewall, may be some async routing going on where the firewall is only catching that reply
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
I have a dilemma with "certain" types of traffic and Antispoofing messages.
Source: 172.23.12.5
Destination: 172.23.3.21, 172.23.3.20
Service (Test): ICMP
I have made attempts to capture traffic, with "tcpdump" "cppcap" "fw monitor" "fw ctl zdebug" and the active "Firewall" of my ClusterXL is not able to "capture" anything, when traffic is generated with a simple PING.
When I just filter in the logs, the source IP, I do get "data" but to my perception, it is "junk data", because it is nothing of what I am trying to capture.
The only thing I see "relevant" when I filter only the ORIGIN, is that all the logs I see, most of them, "emphasize" an Address spoofing issue and I am not sure, if it is an important point to take into account, for my analysis.
Greetings.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
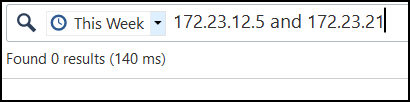
I think filter might be slightly off bro...usually people would do src:x.x.x.x AND dst:x.x.x.x
example -> src:1.1.1.1 AND dst:2.2.2.2
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
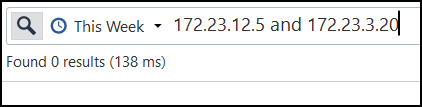
See example below. One of my lab fws is 172.16.10.249 and I was pinging google dns from it.
Andy
Best,
Andy
Andy
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What does the anti-spoofing configuration for bond2.303 look like? I would guess that bond2.303 is missing that source address 172.23.12.5 from its topology. Or that address is configured behind a different interface's topology, so the firewall does not like seeing that source address 172.23.12.5 coming inbound on bond2.303.
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 20 | |
| 17 | |
| 10 | |
| 8 | |
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter