- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- Security Gateways
- :
- Re: How to size a firewall according to the differ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to size a firewall according to the different throughputs
Hi checkmates,
For sizing a firewall I know I have to consider many things such as max. number of concurrent connections, types of interfaces, throughputs and so on. According to the different kind of throughputs I have some doubts. Let's take 5600 SG appliance as an example, which has a firewall throughput of 20.4 Gbps, a NGFW throughtput of 5.1 Gbps, and a threat prevention throughput of 2.78 Gbps. As far as I know, briefly that means that if you don't use any UTM features you will have total throughput of 20.4 Gbps, but if you activate application control and IPS, you will have a throughput of 5.1 Gbps because the gateway has to scan the traffic, and if you also want to use the URL filtering and antivirus features, you will have a throughput of 2.78 Gbps, because the gateway has to do more even scan.
Then, my doubts are:
- If you don't activate any UTM features, I will have 20.4 Gbps of throughput. This considers the sum of the transmited and received traffic of all the interfaces of the firewall, right?
- If I have a users VLAN interface which uses 500 Mbps and where I want to activate URL filtering and antivirus. Will I have to consider a throughput of 2.78 Gbps?
- If I have a mix of interfaces which uses antivirus, others which uses application control and IPS, others which only use firewall rules, will I have to add the bandwitdh of all the interfaces and consider the threat prevention throughput which is the most restrictive?
- What about the VPN throughput which is 6.5 Gbps for 5600 SG appliance. Is this SSL VPN throughput? Or IPSec VPN throughput? Is this the VPN throughput if I don't activate any other UTM features or it will be decreased if I activate antivirus, IPS or other UTM feature?
Thanks in advance.
Regards,
Julián
14 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
To understand the basis of the test numbers you can review the white paper available here:
https://pages.checkpoint.com/enterprise-security-performance.html
Additional consideration should be given to the volume of SSL/TLS traffic to be inspected if enabled.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
H Chris,
Interesting article, however it explains the basis of the test numbers as you said but it doesn’t address my doubts. But if we take the appliance sizing tool and manual sizing, the tool has two key inputs: gateway total throughput and number of users. I am surprised why the utility ask for the number of users instead of number of concurrent connections. And by the other hand, what number do we have to type for the gateway total throughput? The sum of all the gateway interfaces’ bandwidth? The Internet bandwidth?
Regards,
Julian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The tool is intended to be simple to use, from the number of users provided we can derive the other data for a typical use case based on some assumptions.
If you have advanced requirements please discuss those with your local SE who can if necessary liaise with Solution Center for a detailed sizing analysis based on a current appliance model. For concurrent connections memory population is typically the concern.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
1. Up to the stated datasheet figure depending upon your installed version, configuration and traffic profile/mix.
2. Possibly higher and approaching the NGFW firewall figure in some cases, again depending on your unique deployment scenario and if things like deep archive scanning or SSL inspection are enabled (impacts performance).
3. Reference the threat prevention performance metrics in such as case. Technologies such as "fast accel" can assist with extracting the most performance for specific trusted flows.
4. IPSec VPN throughput with AES-128 (AES-NI compatible algorithms are used for optimal results.)
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There's one more thing you need to consider - all those numbers are MAX when CPUs have been pushed to the limit. In your daily life you don't want your appliance running 99% CPU and having no headroom for any "bumps". Half the numbers for realistic approach.
To give you real life example from the same series - 5900. We run all blades but threat extraction and box at 100% CPU probably would meet the datasheet numbers roughly 7Gbps. But I would never allow to go that far. Normally we start planning upgrades at 50% CPU as it gives us sufficient time to plan and implement.
Pure FW throughput - I actually never seen any of appliance getting anywhere near advertised numbers in real life I'm afraid. We have bunch of mid and high end appliances and at best I would say we could squeeze out about half of advertised FW throughput.
With Checkpoint it is a big "guestimation" when it comes to sizing. All depends on traffic mix you have and your own experience / gut feeling. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you guys for your answers! Much more clear 😊
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
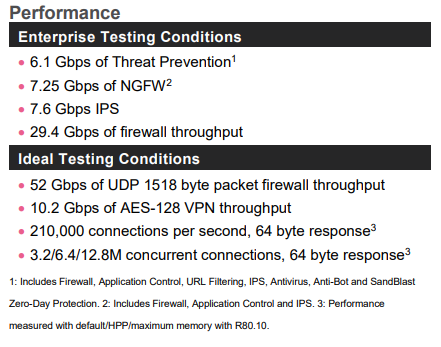
This is an excerpt of the 5900 series datasheet:
Why does Check Point give the values under Ideal Testing Conditions if they are not very useful? Why the connections per second and concurrent connections parameters values are only give under Ideal Testing Conditions and not under more realistic Enterprise Testing Conditions like the others?
Regards,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The values are often used for paper based comparisons with other vendors products where similar logic is used.
If a detailed sizing is required please consult with your SE as the data will likely also have changed with optimizations in more recent software versions.
CCSM R77/R80/ELITE
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Then that’s a good point, but I still think it would be nice they give the max current connections and max connections per second under Enterprise Testing Conditions.
On the other hand, generally in real enterprise networks, what limits more the firewall performance, current connections or throughput?
Regards,
Julian
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From what I know the max concurrent connections is just limited by RAM of the machine. The connections per second are such a theoretical thing and depend on so many factors that you can't really give a number. I bet you will never ever be somewhere near the 200k connections for that appliance in a real environment. With many enabled blades a 6 Core VM (GCP in my case) is nearly at max utilization with around 3000-5000 connections per second and just 200MBit/s of traffic. With low connections it can also handle 3GBit/s of throughput.
Your last question really depends where your Firewall is located. It it handling internet access for many users with Anti Virus, https Inspection etc. you will clearly hit the limit with the connections per seconds first rather than throughput. In other cases you can easily be limited by throughput.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks for the answer. I thought the number of current sessions was given by the traffic the users are generating, and not by the security features the firewall is using for that traffic (AV, App Control, etc.). Am I wrong?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Concurrent sessions mean (if I'm not wrong) the number of connections in the Firewall Table so it's just limited by RAM on does not depend on activated features. On our external Firewall (Internet Access for Users) we have the following stats to give you an idea:
80000 concurrent connections
1500 connections per second
1,5GBit/s throughput
Nearly all blades are enabled, https inspection only for about 10% of the connections (but no Threat Emulation)
Our 16 Core Open Server (HPE DL360 Gen10) has an average load of about 25-30% with that setup.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's ok, I only misunderstood when you said "It it handling internet access for many users with Anti Virus, https Inspection etc. you will clearly hit the limit with the connections per seconds first rather than throughput.". Thanks for the clarification.
Regards,
Julián
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Im no Sales person, but I can tell you from my experience, 6200 and 6400 are fantastic even for bigger size companies, they perform really well.
Best,
Andy
Andy
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 21 | |
| 17 | |
| 11 | |
| 8 | |
| 7 | |
| 4 | |
| 3 | |
| 3 | |
| 3 | |
| 3 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter