- Products
- Learn
- Local User Groups
- Partners
- More
Call For Papers
Your Expertise, Our Stage
Ink Dragon: A Major Nation-State Campaign
March 11th @ 5pm CET / 12pm EDT
AI Security Masters E4:
Introducing Cyata - Securing the Agenic AI Era
The Great Exposure Reset
AI Security Masters E3:
AI-Generated Malware
CheckMates Go:
CheckMates Fest
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
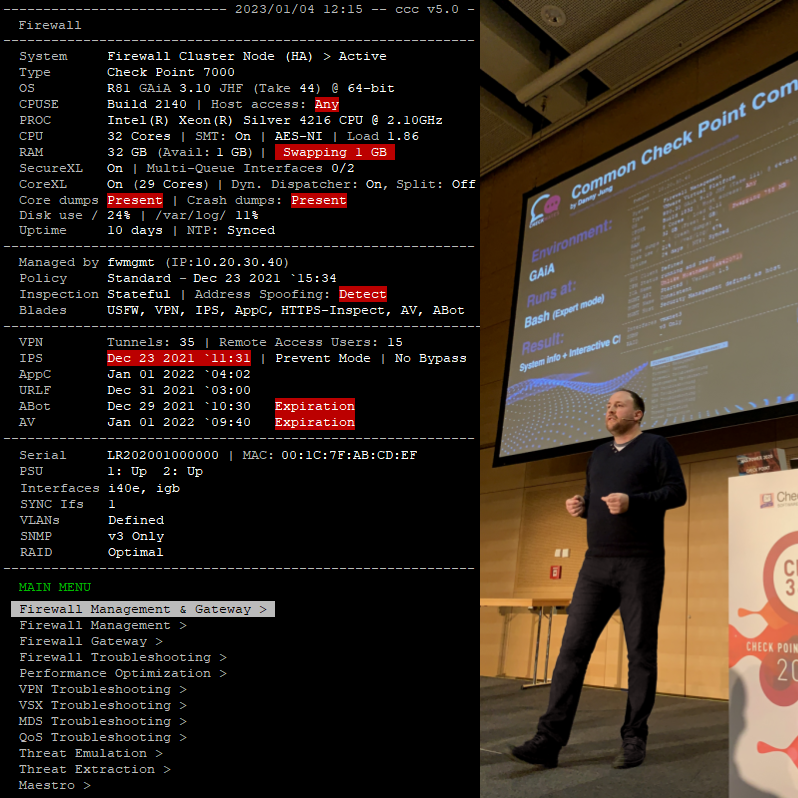
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle.crt https://dannyjung.de/ccc|zcat > /usr/bin/ccc && chmod +x /usr/bin/ccc;. ~/.bashrc
🏆 Code Hub Contribution of the Year 2018!
🎓 Featured in official Maestro courseware!
👍 Endorsed by Check Point Support!
📕 Books: Max Power, FW Admin
▶️ YouTube: Intro
ccc script to run CLI tasks & show system info.
curl_cli $(if [[ `grep proxy:ip /config/active` ]];then echo -n '--proxy ';grep proxy:ip /config/active|cut -f2 -d' '|tr -d '\n';echo -n :;grep proxy:port /config/active|cut -f2 -d' ';fi) --cacert $CPDIR/conf/ca-bundle
Version 1.7 seems to have a typo in the main menu: Two entries for Cluster XL Troubleshooting, although second entry goes to VPN troubleshooting as expected. Otherwise, great tool. Thanks to all the contributors.
[ MAIN MENU ]
Firewall-Management & Gateway >
Firewall-Management >
Firewall Gateway >
ClusterXL Troubleshooting >
ClusterXL Troubleshooting >
Multi-Core Performance Tuning >
VSX Troubleshooting >
MDS Troubleshooting >
Standalone Firewall & Management >
Threat Emulation >
Threat Extraction >
Version 1.7 seems to have a typo in the main menu: Two entries for Cluster XL Troubleshooting, although second entry goes to VPN troubleshooting as expected. Otherwise, great tool. Thanks to all the contributors.
[ MAIN MENU ]
Firewall-Management & Gateway >
Firewall-Management >
Firewall Gateway >
ClusterXL Troubleshooting >
ClusterXL Troubleshooting >
Multi-Core Performance Tuning >
VSX Troubleshooting >
MDS Troubleshooting >
Standalone Firewall & Management >
Threat
Not entirely sure what you mean by disabled interfaces, but it seems to include interfaces clish believes are off.
MyFW2> show configuration
...
set interface eth1-08 state off
set interface eth2-01 state off
set interface eth2-02 state on
add bonding group 1 interface eth2-02
...
[me@MyFW2 Standby]# ifconfig -a | egrep "^[^ ]"
...
eth1-08 Link encap:Ethernet HWaddr 00:1C:7F:__:__:__
eth2-01 Link encap:Ethernet HWaddr 00:1C:7F:__:__:__
eth2-02 Link encap:Ethernet HWaddr 00:1C:7F:__:__:__
...
[me@MyFW2 Standby]# fw ver
This is Check Point's software version R77.30 - Build 137
[me@MyFW2 Standby]# installed_jumbo_take
R77.30 Jumbo Hotfix Accumulator take_159 is installed, see sk106162.
You would obviously have to use awk (or cut, colrm, or some other text manipulation, I guess) to get just the interface name without the extraneous stuff. This was just on a lab firewall I happened to have handy. Off the top of my head, there are a few other ways to get the interface names.
ip link show | egrep "^[^ ]" | awk '{print $2}' | sed -r 's#^([^@:]+)[@:].*#\1#'
netstat -i | tail -n +3 | awk '{print $1}'
With all of them, you should probably include "egrep -v " and an expression defining what to exclude. "^(lo|bond)", for example.
Not entirely sure what you mean by disabled interfaces, but it seems to include interfaces clish believes are off.
MyFW2> show configuration
...
set interface eth1-08 state off
set interface eth2-01 state off
set interface eth2-02 state on
add bonding group 1 interface eth2-02
...
[me@MyFW2 Standby]# ifconfig -a | egrep "^[^ ]"
...
eth1-08 Link encap:Ethernet HWaddr 00:1C:7F:__:__:__
eth2-01 Link encap:Ethernet HWaddr 00:1C:7F:__:__:__
eth2-02 Link
...;Thanks for your input. It is much appreciated. I tried your commands which are leading to different results. If seen various situations where ifconfig shows different results when interfaces had no link, werenot configured or were simply shut down (state: off). The current solution via cpstat os -f ifconfig accompanied by our one-liner can of course be much more optimized. Personally I'd prefer one sorted result instead of two resulting tables in different layouts. Maybe you'd like to come up with a better solution?
Thanks for your input. It is much appreciated. I tried your commands which are leading to different results. If seen various situations where ifconfig shows different results when interfaces had no link, werenot configured or were simply shut down (state: off). The current solution via cpstat os -f ifconfig accompanied by our one-liner can of course be much more optimized. Personally I'd prefer one sorted result instead of two resulting tables in different layouts. Maybe you'd like to com
...;I just tested results with this:
ifconfig -a | egrep "^[^ ]" | awk '{print $1}' | sort > ifconfigA.txt
ip link show | egrep "^[^ ]" | awk '{print $2}' | sed -r 's#^([^@:]+)[@:].*#\1#' | sort > ipLinkShow.txt
netstat -i | tail -n +3 | awk '{print $1}' | sort > netstatI.txt
I then used 'diff' to compare the outputs. ifconfigA.txt and ipLinkShow.txt were exactly the same. netstatI.txt was missing interfaces with clish state off. The interfaces on this system in state off are not physically connected to anything, so they have no link. ifconfig definitely shows interfaces with no link:
[me@MyFW2 Standby]# ifconfig -a | egrep "^[^ ]" | awk '{print $1}' | egrep -v "^(lo|bond)" | xargs -n 1 ethtool | grep Link
Link detected: yes
Link detected: no
Link detected: yes
Link detected: yes
Link detected: yes
Link detected: no
Link detected: yes
Link detected: yes
Link detected: yes
Link detected: no
Link detected: no
Link detected: yes
Link detected: no
Link detected: yes
'ip link show' is significantly faster than ifconfig:
[me@MyFW2 Standby]# echo "ifconfig -a | egrep '^[^ ]' | awk '{print \$1}' | egrep -v '^(lo|bond)'" > ifconfigA.sh;chmod +x ifconfigA.sh;time ./ifconfigA.sh >/dev/null;rm ifconfigA.sh
real 0m0.117s
user 0m0.009s
sys 0m0.114s
[me@MyFW2 Standby]# echo "ip link show | egrep '^[^ ]' | awk '{print \$2}' | sed -r 's#^([^@:]+)[@:].*#\1#' | egrep -v '^(lo|bond)'" > ipLinkShow.sh;chmod +x ipLinkShow.sh;time ./ipLinkShow.sh >/dev/null;rm ipLinkShow.sh
real 0m0.005s
user 0m0.002s
sys 0m0.007s
I verified the output of both commands before redirecting STDOUT to /dev/null. The overwhelming majority of the time spent is on the initial command (ifconfig or 'ip link show'). All the egrep, awk, and sed after is basically free:
[me@MyFW2 Standby]# time ifconfig -a >/dev/null
real 0m0.126s
user 0m0.005s
sys 0m0.121s
[me@MyFW2 Standby]# time ip link show >/dev/null
real 0m0.003s
user 0m0.000s
sys 0m0.004s
Note that these numbers are for a single run. I haven't done a large set and averaged them yet.
It's also worth noting cpstat os -f ifconfig takes much longer than either:
[me@MyFW2 Standby]# time cpstat os -f ifconfig >/dev/null
real 0m0.264s
user 0m0.101s
sys 0m0.003s
I just tested results with this:
ifconfig -a | egrep "^[^ ]" | awk '{print $1}' | sort > ifconfigA.txt
ip link show | egrep "^[^ ]" | awk '{print $2}' | sed -r 's#^([^@:]+)[@:].*#\1#' | sort > ipLinkShow.txt
netstat -i | tail -n +3 | awk '{print $1}' | sort > netstatI.txt
I then used 'diff' to compare the outputs. ifconfigA.txt and ipLinkShow.txt were exactly the same. netstatI.txt was missing interfaces with clish state off. The interfaces on this system in state off are not phys
...;This would cause a huge latency increase on script start while I'm looking to decrease the current delay. Instead of calling external applications I'd prefer grepping some files' content instead, because it's much faster.
As I understand, mgmt_cli and API works only on Management server and only in R80.10. I thought that the question was how to check that on a gateway itself, like what rules are used on it. Maybe I misinterpreted it.
But anyway, there is a separate thread for this question.
As I understand, mgmt_cli and API works only on Management server and only in R80.10. I thought that the question was how to check that on a gateway itself, like what rules are used on it. Maybe I misinterpreted it.
But anyway, there is a separate thread for this question.
;Even on the gateway it is possible by looking into the $FWDIR/state/local/FW1 directory as described several times in this community.
Even on the gateway it is possible by looking into the $FWDIR/state/local/FW1 directory as described several times in this community.
;Here is a linear-log plot of the execution time of commands to find the interface names. In green, we have 'ip link show', in orange, we have 'ifconfig -a', and in blue, 'cpstat os -f ifconfig'. All include the necessary text processing to get down to just a list of interface names with no additional information. I ran them each 1000 times to collect the data. The X axis is the time taken, and the Y axis is the number of times the command took that long. 'ip link show' took 0.004 seconds 940 out of 1000 times.
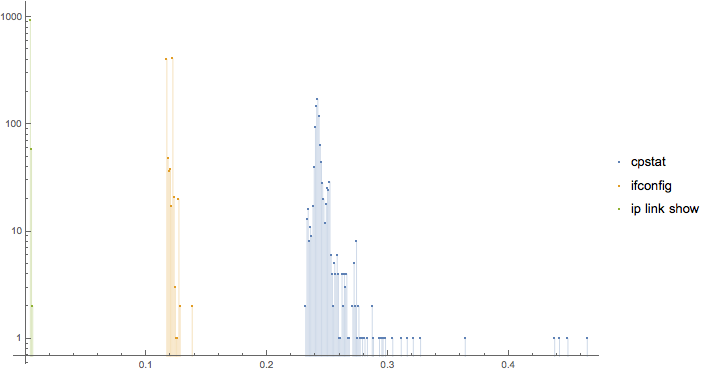
Here is a linear-log plot of the execution time of commands to find the interface names. In green, we have 'ip link show', in orange, we have 'ifconfig -a', and in blue, 'cpstat os -f ifconfig'. All include the necessary text processing to get down to just a list of interface names with no additional information. I ran them each 1000 times to collect the data. The X axis is the time taken, and the Y axis is the number of times the command took that long. 'ip link show' took 0.004 seconds
...;It is 2.1 now already - great work ! This by now is a really lovely tool ![]() .
.
Besides a noticed bug: On FIREWALL-MANAGEMENT Page, the last command (cpca_client set_mgmt_tool off) is also used for the "on" command before, then all above trigger the next command instead of the displayed. The line for migrate export issues the vpn overlap_encdom and the first command is correct again. So migrate export is currently left out.
Also a slight feeling of insecurity: When started, the script is updated in the background without asking - i would rather not run it on a customer system ![]() .
.
It is 2.1 now already - great work ! This by now is a really lovely tool ![]() .
.
Besides a noticed bug: On FIREWALL-MANAGEMENT Page, the last command (cpca_client set_mgmt_tool off) is also used for the "on" command before, then all above trigger the next command instead of the displayed. The line for migrate export issues the vpn overlap_encdom and the first command is correct again. So migrate export is currently left out.
Also a slight feeling of insecurity: When started, the scrip
...;Thanks for providing these interesting results. Let's create a a One-liner based on 'ip link show' that provides a similar out to what 'cpstat os -f ifconfig' provides.
Fixed in version 2.2. If you won't have the self-update as requested by other users, just comment out the two lines in the script.
Hi,
Great tool!
Some commands for MTA (maybe new branch?):
cpstat fw -f smtp
tail -f /var/log/maillog
/opt/postfix/usr/sbin/postqueue -c /opt/postfix/etc/postfix/ -p
tail $FWDIR/log/emaild.mta.elg
Bug:
When trying to select: Threat Emulation -> /opt/postfix/usr/sbin/postqueue -c /opt/postfix/etc/postfix/ -p this option disappears and I am unable to use arrows anymore.
Best Regards
Maciej
Hi,
Great tool!
Some commands for MTA (maybe new branch?):
cpstat fw -f smtp
tail -f /var/log/maillog
/opt/postfix/usr/sbin/postqueue -c /opt/postfix/etc/postfix/ -p
tail $FWDIR/log/emaild.mta.elg
Bug:
When trying to select: Threat Emulation -> /opt/postfix/usr/sbin/postqueue -c /opt/postfix/etc/postfix/ -p this option disappears and I am unable to use arrows anymore.
Best Regards
Maciej
;Commands and code optimization implemented in version 2.3
Changed tail -f to tail because it's non-interactive and SIGINT (Crtl-C) needs to be pressed in order to quit the routine which quits ccc as well.
Thanks!
Hi Danny,
in [ < MAIN - MULTI-CORE PERFORMANCE TUNING ] you have
netstat -ni Check for drop on interfaces
Beat me when I am wrong, but I think this is not multicore relevant
in [ < MAIN - FIREWALL-MANAGEMENT & GATEWAY ] you already have
cpstat os -f ifconfig Show advanced interface summary
Both commands have pretty the same output.
Maybe you can remove one of them.
Regards
Sven
Hi Danny,
in [ < MAIN - MULTI-CORE PERFORMANCE TUNING ] you have
netstat -ni Check for drop on interfaces
Beat me when I am wrong, but I think this is not multicore relevant
in [ < MAIN - FIREWALL-MANAGEMENT & GATEWAY ] you already have
cpstat os -f ifconfig Show advanced interface summary
Both commands have pretty the same output.
Maybe you can remove one of them.
Regards
Sven
;How easy would it be to implement the watch command into the commands? I think that's a really good feature to see the increase or decrease of values when running a command? I sometimes come out of the script to then run the command separately?
How easy would it be to implement the watch command into the commands? I think that's a really good feature to see the increase or decrease of values when running a command? I sometimes come out of the script to then run the command separately?
;Hello Danny,
Thanks for the 2500 points. It's a little too much for a one-liner (One-liner for Address Spoofing Troubleshooting).
I think it's a great community and we should all help each other without rewards.
I gave you back 2500 points ![]() for your great work in this article Common Check Point Commands (ccc)
for your great work in this article Common Check Point Commands (ccc)![]() .
.
And thanks to everyone who helped to find the great commands for ccc.
For more infos see this article with revisions:
Show Address Spoofing Networks via CLI
Best Regards
Hello Danny,
Thanks for the 2500 points. It's a little too much for a one-liner (One-liner for Address Spoofing Troubleshooting).
I think it's a great community and we should all help each other without rewards.
I gave you back 2500 points ![]() for your great work in this article Common Check Point Commands (ccc)
for your great work in this article Common Check Point Commands (ccc)![]() .
.
And thanks to everyone who helped to find the great commands for ccc.
For more infos see this article with revisions:
Cool tool! Another suggestion to add to the Threat Extraction menu:
Bypasses all files. Use this command to debug issues with the scrub (Threat Extraction) daemon. When you set bypass to active, requests from the mail transfer agent (MTA) to the scrub daemon are not handled. Threat Extraction is suspended. No files are cleaned.
[Expert@te250x:0]# scrub bypass
Available options:
scrub bypass on - activate bypass
scrub bypass off - deactivate bypass
scrub bypass state - checks the threat extraction bypass current state
[Expert@te250x:0]#
Cool tool! Another suggestion to add to the Threat Extraction menu:
Bypasses all files. Use this command to debug issues with the scrub (Threat Extraction) daemon. When you set bypass to active, requests from the mail transfer agent (MTA) to the scrub daemon are not handled. Threat Extraction is suspended. No files are cleaned.
[Expert@te250x:0]# scrub bypass...;
Available options:
scrub bypass on - activate bypass
scrub bypass off - deacti
The System info is wrong on a Server running FW Management & SmartEvent, because it only says SmartEvent server, even though it is both.
I ended up dropping your one-liner as it still relies on ifconfig and not the actual configuration from $FWDIR/state/local/FW1/local.set which can differ from what is configured in GAiA. This makes troubleshooting address spoofing issues worse while the intention is to make it easier. Also your one-liner doesn't work correctly on single firewall gateways that are not part of a cluster. Sorry.
I created a new one-liner that is implemented in ccc starting from version 2.4.
I ended up dropping your one-liner as it still relies on ifconfig and not the actual configuration from $FWDIR/state/local/FW1/local.set which can differ from what is configured in GAiA. This makes troubleshooting address spoofing issues worse while the intention is to make it easier. Also your one-liner doesn't work correctly on single firewall gateways that are not part of a cluster. Sorry.
I created a new one-liner that is implemented in ccc starting from version 2.4.
;I tested this new version and IPv6 on the is not correctly displayed (btw. they were missing completely in the original one of Heiko), because colons are missing.
And this reminds me that the topology information for IPv6 on both one-liners is missing ![]()
Also adding again the anti-spoofing mode/setting per interface would be great ![]()
[Executing:]# echo; egrep -B1 $'ifindex|:ipaddr|\(\x22<[0-9]' /opt/CPsuite-R80/fw1/state/local/FW1/local.set | sed 's/[\x22\t:()<>-]//g' | sed 's/interface_topology/\x20\x20\x20\x20 Calculated Interface Topology/g' | sed '0,/ifindex 0/{/ifindex 0/d;}' | sed '/ifindex 0/q' | tac | sed '/ifindex 0/I,+2 d' | tac | sed '/ifindex/d' | sed 's/,/ -/g' | sed 'N;s/\nipaddr/ >/;P;D' | sed '/ - /s/^/\x20\x20\x20 /' | grep -C 9999 --color=auto '>'
eth1.2501 > 192.168.221.3
ipaddr6 2a0119015efe0013
Calculated Interface Topology
192.168.221.0 - 192.168.221.255
eth2 > 192.168.229.2
ipaddr6 2a0119015efe0ff2
Calculated Interface Topology
192.168.229.0 - 192.168.229.255
eth1.2500 > 192.168.220.3
ipaddr6 2a0119015efe0003
Calculated Interface Topology
192.168.220.0 - 192.168.220.255
eth0 > 10.2.231.53
ipaddr6 2a0119015efd000e002
Calculated Interface Topology
0.0.0.0 - 126.255.255.255
128.0.0.0 - 192.168.219.255
192.168.222.0 - 192.168.228.255
192.168.230.0 - 223.255.255.255
240.0.0.0 - 255.255.255.254I tested this new version and IPv6 on the is not correctly displayed (btw. they were missing completely in the original one of Heiko), because colons are missing.
And this reminds me that the topology information for IPv6 on both one-liners is missing ![]()
Also adding again the anti-spoofing mode/setting per interface would be great ![]()
[Executing:]# echo; egrep -B1 $'ifindex|:ipaddr|\(\x22<[0-9]' /opt/CPsuite-R80/fw1/state/local/FW1/local.set | sed 's/[\x22\t:()<>-]//g' | sed 's/intAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
