- Products
Network & SASE IoT Protect Maestro Management OpenTelemetry/Skyline Remote Access VPN SASE SD-WAN Security Gateways SmartMove Smart-1 Cloud SMB Gateways (Spark) Threat PreventionCloud Cloud Network Security CloudMates General CloudGuard - WAF Talking Cloud Podcast Weekly ReportsSecurity Operations Events External Risk Management Incident Response Infinity AI Infinity Portal NDR Playblocks SOC XDR/XPR Threat Exposure Management
- Learn
- Local User Groups
- Partners
- More
This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
- Products
- AI Security
- Developers & More
- Check Point Trivia
- CheckMates Toolbox
- General Topics
- Products Announcements
- Threat Prevention Blog
- Upcoming Events
- Americas
- EMEA
- Czech Republic and Slovakia
- Denmark
- Netherlands
- Germany
- Sweden
- United Kingdom and Ireland
- France
- Spain
- Norway
- Ukraine
- Baltics and Finland
- Greece
- Portugal
- Austria
- Kazakhstan and CIS
- Switzerland
- Romania
- Turkey
- Belarus
- Belgium & Luxembourg
- Russia
- Poland
- Georgia
- DACH - Germany, Austria and Switzerland
- Iberia
- Africa
- Adriatics Region
- Eastern Africa
- Israel
- Nordics
- Middle East and Africa
- Balkans
- Italy
- Bulgaria
- Cyprus
- APAC
CheckMates Fest 2026
Join the Celebration!
AI Security Masters
E1: How AI is Reshaping Our World
MVP 2026: Submissions
Are Now Open!
What's New in R82.10?
Watch NowOverlap in Security Validation
Help us to understand your needs better
CheckMates Go:
Maestro Madness
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- CheckMates
- :
- Products
- :
- Network & SASE
- :
- SMB Gateways (Spark)
- :
- Re: Multi Factor authentication for RAVPN users wi...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Are you a member of CheckMates?
×
Sign in with your Check Point UserCenter/PartnerMap account to access more great content and get a chance to win some Apple AirPods! If you don't have an account, create one now for free!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jump to solution
Multi Factor authentication for RAVPN users with Google Authenticator on SMB devices
Hi,
I have setup 1590 appliance to work with RADIUS server for 2ND factor for RAVPN users.
Radius server is Ubuntu 20.04 with FreeRadius service on it.
Radius server part works as a charm, it communicates with Google Authenticator and makes authentication decisions according to user/pass/OTP policy setup.
Problem is that on our CP 1590 appliance side. After successful Radius authentication (RADIUS packets are exchanged between CP 1590 device and Radius server), RAVPN client gets disconnected every time (RAVPN connection is never completed).
SMB appliances use RADIUS v1, and because of that password length together with OTP from goolge authenticator should not be over 16 characters long (it is limitation on SMB appliances they can not use Radius v2).
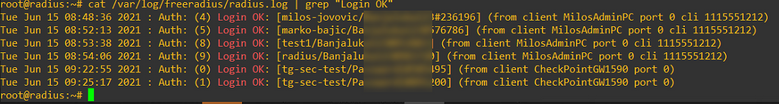
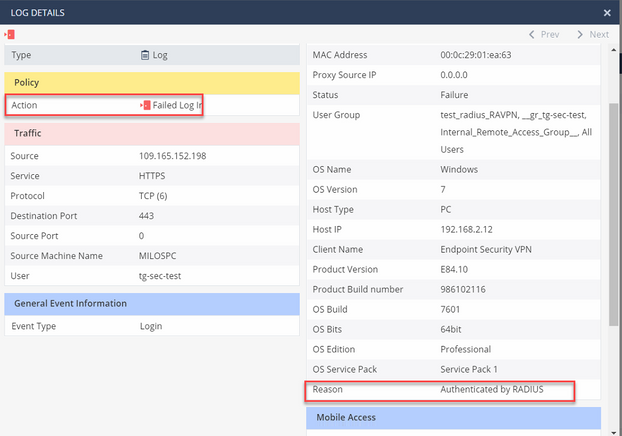
In security logs we get:
Action: Failed Log In
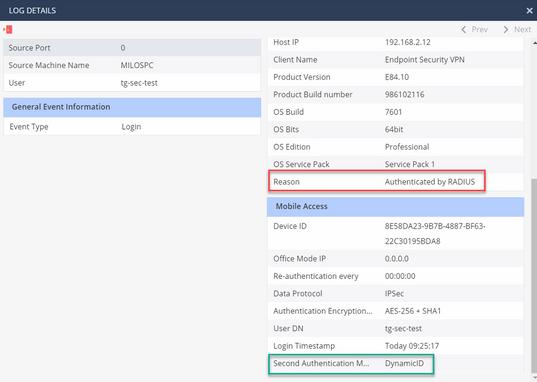
Reason: Authenticated by RADIUS
Second authentication method: DynamicID
Surely, this is where the problem is.
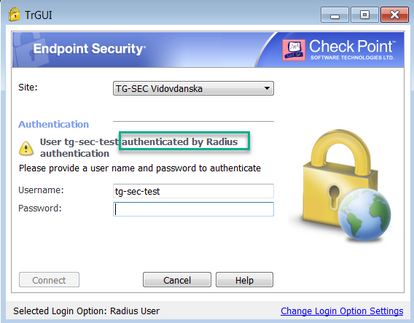
Our endpoint security VPN client shows: User XXX authenticated by Radius authentication
Check Point 1590 setup:
1. local users with ravpn permission created (according to Radius server - to match username and password with Radius server local users database)
2. Put users in user group with RAVPN permissions
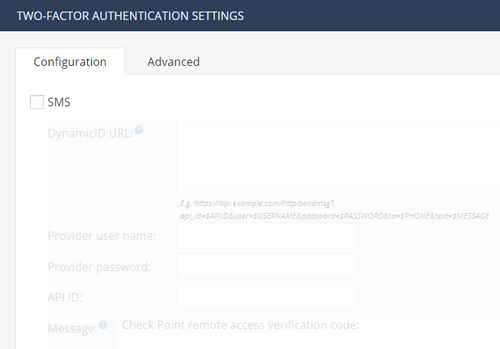
3. Checked option - Require users to confirm their identity using two-factor authentication
Did not checked SMS option as we do not use SMS DynamicID (left it default):
4. Changed auth method on RAVPN client to Radius server
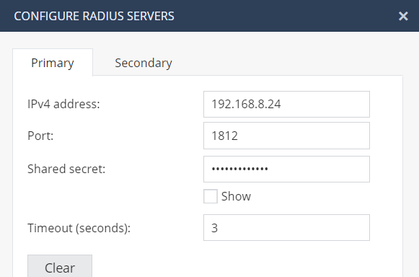
5. We created authentication server (Radius):
Kindly ask You for a hint how to make this work?
All suggestions are welcome.
Thanks!
Milos
1 Solution
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is listed in Limitations: sk159772: Check Point R80.20 for 1500, 1600, and 1800 Appliances Features and Known Limitations
| Blade / Feature | Locally managed |
Centrally managed |
Comments |
| VPN and Remote Access |
| Remote access client multi factor authentication | Yes | No | SMS as second factor authentication. |
#
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
15 Replies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
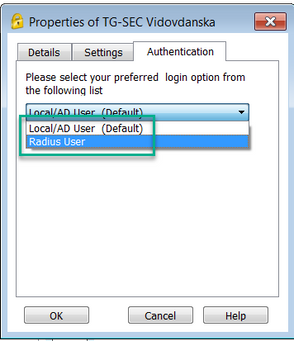
As addition to my first message, if I check on 1590 GW the option - Require users to confirm their identity using two-factor authentication,
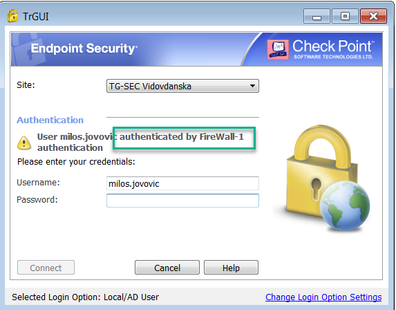
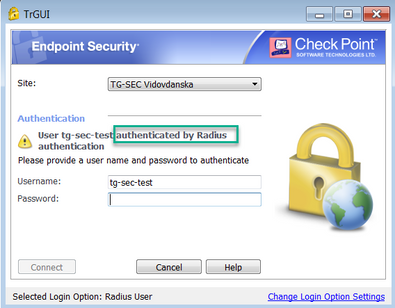
on VPN client I got these two auth options:
With both auth. options from picture, RAVPN user gets successfully authenticated, but VPN tunnel establishment is not being started by 1590 appliance at all (no tunnel test traffic (port 18234) , it's like that VPND is not being triggered by these auth options), and at the end client gets disconnected with messages like this:
Local/AD user (Default):
Radius user:
On the contrary, if I do not check on 1590 GW the option - Require users to confirm their identity using two-factor authentication, on VPN client there are many auth options (username/pass, SecureID, certs,...). But no radius at all.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
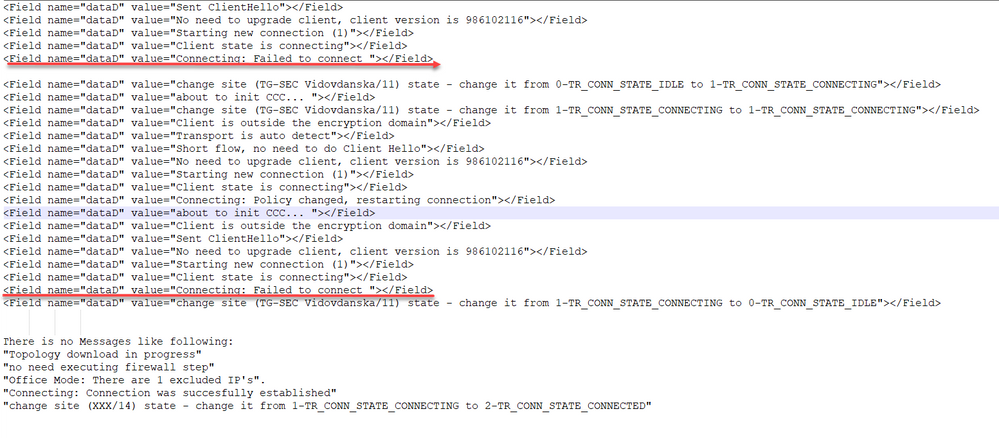
VPN client side logs during testing with test radius user:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2FA currently only works with SMS, see To configure Two-Factor Authentication, Quantum Spark 1500, 1600 and 1800 Appliance Series R80.20.25 Locally Managed Administration Guide p.212 - so there is currently no way to achieve what you want !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Albrecht,
I have just solved an issue by:
1. Deleting all users on CP 1590 appliance (which were already configured on Radius Server),
2. Creating Radius type group (checked all users, groups) and checked RAVPN permissions for Radius group,
3. Unchecking the option on CP - Require users to confirm their identity using two-factor authentication,
4. In VPN client I choose auth. scheme (username/password).
And it works as a charm! Users are authenticated by external Radius server (FreeRadius on Ubuntu), which is further
responsible for handling Google Authenticator OTP. Basically in VPN client, in password field we put together a password which is defined on Radius server along with OTP token from google authenticator app on Mobile phone in following manner:<passwordOTP>
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes - 2FA is outsourced here to RADIUS. See sk137732: 2FA (Factor Authentication) support for remote access VPN in locally managed SMB appliance... for details about this R77.20.xx restriction.
With R80.20.xx., 2FA is possible for locally managed SMBs using SMS.
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It would be great if we could be in situation to configure MFA directly on the Security Gateway (locally managed SMB appliance).
Thanks for comments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, certainly !
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It is listed in Limitations: sk159772: Check Point R80.20 for 1500, 1600, and 1800 Appliances Features and Known Limitations
| Blade / Feature | Locally managed |
Centrally managed |
Comments |
| VPN and Remote Access |
| Remote access client multi factor authentication | Yes | No | SMS as second factor authentication. |
#
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks Albrecht.
At the end, I really look forward that CP will as soon as support radius v2 on SMB appliances (to avoid authentication with up to 16 character passwords (Radius v1 - RFC 2138)).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why is this option that 'require users to confirm their identity using two-factor authentication' not available in my R80.20.05 experimental environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The option 'require users to confirm their identity using two-factor authentication' is available on the R80.20.10 ver. and above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mjovovic - do you have the document for setting up this freeRadius and google authenticator. i did configure it but when i am trying to do a local test- it says packet rejected. not sure where have i done mistake. i am not very good in linux. it would be great if you can share the doc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi @G_W_Albrecht This SK doesnt have freeradius method explained. the one which is mentioned is SMS based authentication. i need FreeRadius with GoogleAuth.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
sk72940: How to configure RADIUS server for authentication on Gaia OS
CCSP - CCSE / CCTE / CTPS / CCME / CCSM Elite / SMB Specialist
Leaderboard
Epsum factorial non deposit quid pro quo hic escorol.
| User | Count |
|---|---|
| 5 | |
| 2 | |
| 2 | |
| 1 |
Upcoming Events
Thu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 12 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 3: Exposing AI Vulnerabilities: CP<R> Latest Security FindingsThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudThu 08 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 1: How AI is Reshaping Our WorldThu 22 Jan 2026 @ 05:00 PM (CET)
AI Security Masters Session 2: Hacking with AI: The Dark Side of InnovationThu 26 Feb 2026 @ 05:00 PM (CET)
AI Security Masters Session 4: Powering Prevention: The AI Driving Check Point’s ThreatCloudAbout CheckMates
Learn Check Point
Advanced Learning
YOU DESERVE THE BEST SECURITY
©1994-2025 Check Point Software Technologies Ltd. All rights reserved.
Copyright
Privacy Policy
About Us
UserCenter